
Bug bounty in practice: the final layer of security
What does a bug bounty program look like, and what does it deliver? We talk to Visma about its usefulness for security professionals and the ultimate benefit for the user of the software.
"With the bug bounty program, we have extra eyes looking at our products," explains Chief Information Securi... Read more

Application testing democratised via GenAI in Tricentis Copilot
Software application development is benefiting from AI-assisted testing at the ‘back end’ of enterprise IT systems in order to make our business apps bug-free, more functionally complete and safer. Among the firms pushing forward AI tools of this kind is continuous testing and quality engineeri... Read more

Wiz nearing acquisition of Lacework for a bargain
A week after it acquired Gem Security, Wiz is already aiming for its next target. Lacework, which once seemed to be worth nearly 8 billion euros, is said to cost between 140 million and 190 million euros.
A letter of intent is said to have already been written to finalize the proposed acquisitio... Read more

Meta unveils powerful open-source model Llama 3 and chatbot Meta AI
Meta has announced Llama 3, the successor to the highly successful open-source model Llama 2. Along with the new LLM debuts Meta AI, one of the best AI assistants in the world, according to the company.
Llama 3 launches with two models: the compact Llama 3-8B (8 billion parameters), which can be... Read more
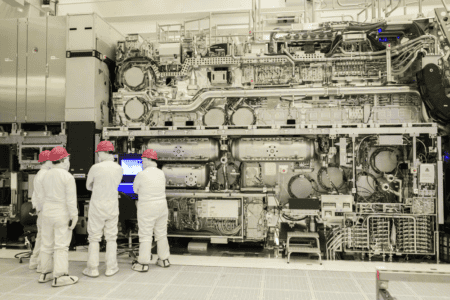
Newest ASML machine at Intel is ready to go, with plenty of R&D ahead
Intel has just announced that ASML's High-NA EUV machine has finished construction. For the first time, the so-called Twinscan EXE:5000 has made 10-nanometer lines on a piece of silicon, proving that all components work correctly to some degree. The new device will enable future manufacturing proce... Read more

How did Phishing-as-a-Service group LabHost operate?
With "Operation PhishOFF," phishing gang LabHost appears to have exited the cybercrime stage. This criminal group was broken up through international cooperation between 18 countries and security services. But how did the LabHost members operate? And how did they eventually get caught?
LabHost w... Read more

Cisco Hypershield: new security architecture protects against new (and old) problems
According to Cisco, what we need is not so much new security products, but a completely new architecture to better protect organizations and especially their workloads. That's what Hypershield is supposed to accomplish.
Hypershield is a big announcement for Cisco. A very big one, even, based on ... Read more

SAS wants to make AI models and AI modeling as accessible as possible
AI models sometimes have an almost mythical status. You can do a lot with them, but building and deploying them is no easy task. If it were up to SAS, that wouldn't be necessary at all. How does it want to achieve that? Some announcements during SAS Innovate shed light on this question.
Organiza... Read more
Google hints at breakthrough for LLMs with Infini-attention
Google researchers claim they've cracked the code to give large language models (LLMs) the literary equivalent of an endless appetite. Their latest paper unveils 'Infini-attention,' a technique that supposedly lets models munch on input of infinite length without getting indigestion from memory ove... Read more

Process HQ steals the show in 24.2 release of Appian Platform
Process mining is taking on an increasingly important role within Appian's automation and orchestration platform. It should provide both more insights into organizations' processes, but also into the underlying Data Fabric. Of course, there is also the necessary space and focus on AI in version 24.... Read more








