
Temporarily no new users welcome on PyPi due to malware
The Python repository felt compelled to intervene after packages were uploaded that executed malicious code on devices. It was also temporarily unable to create new projects.
PyPi has since returned to normal operation. However, it was not possible to register and create projects for 10 hours. G... Read more

Large-scale attack on Ray framework exposes AI security risks
For seven months, attackers had free reign to wreak havoc inside the AI infrastructure of major tech companies. An exploitation of vulnerability CVE-2023-48022 in the widely used open-source Ray framework has led to manipulated models, stolen hardware cycles and compromised data. Its developer Anys... Read more
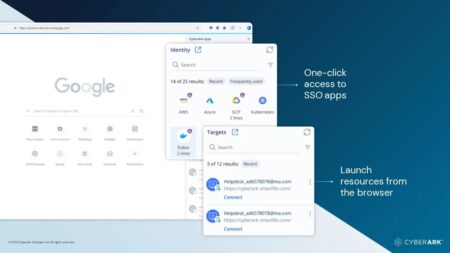
CyberArk launches Secure Browser for secure access
With the CyberArk Secure Browser, companies can build additional security and privacy safeguards into employee browser sessions.
CyberArk has experience in privileged access management. This allows employees' and partners' access rights to applications to be controlled so that only authorized us... Read more

Fortinet integrates FortiGuard SOCaaS with Security Fabric
Companies that have outsourced SOC operations through FortiGuard SOCaaS can now integrate Fortinet solutions (local or cloud-based) through the Security Fabric. This further streamlines mitigation processes for network environments.
Users of the managed FortiGuard SOCaaS service can now integrat... Read more

CrowdStrike Falcon XDR now integrates with Rubrik Security Cloud
CrowdStrike and Rubrik have announced a strategic partnership. Customers can now combine CrowdStrike's XDR platform with Rubrik Security Cloud, allowing security teams to better protect sensitive data.
Both parties state that IT environments today are highly complex, requiring defenses against c... Read more

Number of exploited zero-days up more than 50%
Figures from Google show that last year there were 97 actively exploited zero-day vulnerabilities. In 2022, the number was still 62 vulnerabilities.
With this, the upward trend has returned. A year ago, the figures still showed a positive trend downward. According to Google data, the year 2021 m... Read more

Cisco: ‘3% of companies fully prepared for cyber attack’
Most companies globally are still not fully maturely prepared for cyber incidents.
That's according to research by Cisco. Companies are still major targets of cyber attacks, such as phishing, ransomware, supply chain and social engineering attacks. Nearly three-quarters of companies expect to be... Read more
Supply chain risks are becoming an ever larger problem for businesses
The increasing complexity of IT environments is leading to more hidden cyber threats. The risk of cyberattacks and data breaches through the software supply chain is hard to ward off, according to research by JFrog.
To point out how cluttered corporate IT infrastructures can be today, JFrog cite... Read more
 Expert talks
Expert talks

The impact of evolving regulation and compliance on API security
Regulations are constantly evolving, becoming more punitive with larger fines and penalties every year. As a result, there is a collective industry movement towards the continuous improvement of cybersecurity in business and their ecosystem. This includes understanding what policies and processes m... Read more

FBI implores developers to finally eradicate SQL injections
The FBI and the U.S. Cybersecurity and Infrastructure Agency (CISA) argue that SQL injections should be a thing of the past. Despite developers' knowledge for two decades of how to prevent this type of attack, it continues to cause widespread exploits.
SQL injections insert malicious code into S... Read more









