‘Lack of standards and policies threaten API security’
Researchers from Enable U indicate that a lack of standards, uniform policies and security awareness among employees threaten the API security of IT environments. There's plenty of room for improvement, the organization concluded in a recent research report.
APIs are the building blocks that en... Read more

Mandiant Threat Intelligence integrates with SentinelOne XDR
SentinelOne launched an integration of Mandiant Threat Intelligence and Singularity XDR. The integration allows Mandiant to stream threat intelligence to SentinelOne's XDR platform, providing security professionals with additional information on vulnerabilities and threats.
SentinelOne develops ... Read more

Google launches GUAC, open-source tool for software security reviews
Google introduced GUAC, an all-new cybersecurity tool that combines strategic data from different sources to help developers efficiently review and analyze software security.
Google collaborated with Citibank NA, Purdue and Kusari to launch the tool, which helps companies find software vulnerabi... Read more

HP Wolf Security provides endpoint protection with secure access
HP has expanded its Wolf Security endpoint security portfolio Sure Access Enterprise (SAE). The solution helps tightly secure access rights to sensitive data, systems and applications using dedicated VMs.
The new security solution should protect both compromised and uncompromised endpoints from ... Read more

ID-ware hack hits thousands of university students and employees
The personal data of tens of thousands of Eindhoven University of Technology students and employees were captured in a recent ransomware attack on the Dutch branch of German smart card specialist ID-ware.
In an email to about 21,000 students and employees, TU Eindhoven announced that personal d... Read more

Misconfiguration causes controversial data breach at Microsoft
A misconfigured Azure Blob Storage endpoint caused unauthorized access to large amounts of Microsoft customer data last month. Although security researchers indicate that the breach affects tens of thousands of organizations worldwide, Microsoft believes the extent of the incident is exaggerated.
... Read more

Sophos MDR gained a myriad of third-party integrations
Sophos unveiled new third-party integrations with its managed detection and response (MDR) service to improve security capabilities across various client and operational environments.
As a component of the Sophos Adaptive Cybersecurity Ecosystem, the new third-party support incorporates data fr... Read more

WIP19 malware threatens IT service providers and telecom companies
Security researchers from SentinelOne have discovered a new malware cluster dubbed WIP19. The malware variant is likely used by Chinese cybercriminals and primarily targets IT service providers and telecom companies.
According to the security researchers, the malware variant recently surfaced am... Read more

FortiSASE delivers cloud-secured SD-WAN connectivity
FortiSASE integrates cloud-delivered SD-WAN connectivity with cloud-delivered security (SSE).
This week Fortinet announced cloud-delivered enhancements to FortiSASE that integrate software-defined wide area network (SD-WAN) connectivity with cloud-delivered security to enable flexible secure pr... Read more
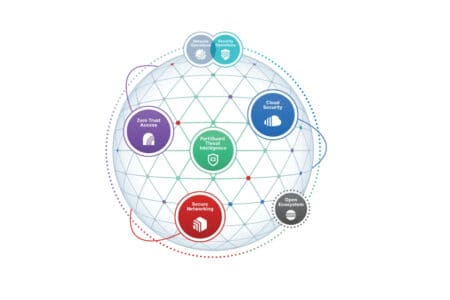
Modern organizations can no longer do without a security fabric
Increasing complexity of organizations' environments poses questions that a security mesh architecture can answer.
The number of cybersecurity solutions within organizations is constantly increasing. They have to be, because the environments of these organizations are also becoming increasingly ... Read more









