
Aqua Security’s Trivy now scans multiple container platforms
Aqua Security, a startup for container security, indicates that its open source tool Trivy for scanning container images for vulnerabilities is now suitable for multiple container platforms. New additions include the Mirantis Docker Enterprise Platform and Harbor.
With the rise of containers, th... Read more

Trend Micro zero-days abused by hackers
Hackers have attempted to exploit two zero-day vulnerabilities in Trend Micro solutions. The company reported this earlier this week in an statement.
The Japanese security firm released patches on Monday to address the two vulnerabilities. The patch resolved three other issues, which were basica... Read more

‘TrojAI framework can test cyber attacks on AI models’
Researchers at John Hopkins University in the United States have developed a set of TrojAI tools for 'arming' AI models against cybercriminal attacks. The aim of the framework is to discover how AI models based on machine learning can best be protected against attacks.
Nowadays, AI can no longer... Read more

Hospitals and healthcare providers under fire with ransomware attacks
Hackers are currently targeting hospitals and healthcare providers with ransomware attacks, while many of those institutions are struggling with the COVID-19 corona virus pandemic.
SiliconAngle reports that a health district in Illinois and a hospital in the Czech Republic have been targeted by ... Read more

Phishers adapt to surge in home workers due to corona virus
A significant increase in phishing campaigns has been observed by Mimecast Threat Intelligence, as more people worldwide are working from home. The campaigns would try to take advantage of the situation in order to capture login data by imitating services that are currently used a lot from home.
... Read more

Intel CPUs vulnerable to new ‘snoop’ attack
A software engineer from AWS found a new vulnerability in existing Intel CPUs that allows attackers to extract data from the cache. The attack, described as Snoop-assisted L1 Data Sampling (Snoop for short) would work on a significant set of processors of the American company.
Pawel Wieczorkiewi... Read more

‘Malware campaign is hacking cybercriminals’
Hackers are getting a taste of their own medicine, according to a recent malware campaign discovered by security specialist Cyberreason. Well-known hacker tools are hijacked with the njRat trojan. However, the trojan not only gives access to hackers' systems, but also to systems that they in turn c... Read more

WordPress is working on automatic updates for themes and plugins
Vulnerabilities in certain plugins and themes on WordPress were regularly in the news in recent months, as it allowed hackers to access certain sites. In the fight against hackers, WordPress is now working on a feature that can automatically install updates to improve security faster.
Where them... Read more

‘Companies lose millions due to more cyber attacks and disruptions’
According to Dell, the number of cyber attacks and so-called "disruptive events" is steadily increasing, costing organisations millions. This is reflected in the company's Global Data Protection Index.
The study shows that on average, organisations are managing nearly 40 percent more data than t... Read more
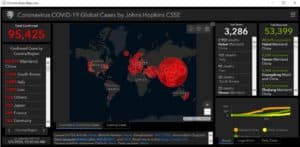
Hackers spread malware with fake coronavirus world map
Cybercriminals deploy a fake world map application showing the number of COVID-19 infections worldwide. Visitors are then infected with malware that tries to steal credentials and other sensitive data.
The security company Reason Cybersecurity discovered the method of spreading malware. By infec... Read more









