Cloudflare reported that its system managed to stop the most significant DDoS attack on record in July. In a post explaining what happened, Cloudflare said the attack was 17.2 million requests-per-second, about three times larger than the next biggest one ever recorded.
Omer Yoachimik, the product manager at Cloudflare, explained in a blog post that the company serves over 25 million HTTP requests per second on average in this year’s first quarter, illustrating just how expansive the attack was.
Yoachimik said the attack came from a botnet targeting one of Cloudflare’s financial industry customers.
Infected devices
The attack managed to hit Cloudflare edge with over 330 million attack requests within seconds. The attack traffic came from more than 20,000 bots scattered across 125 countries around the world. The bots’ source IP addresses showed that almost 15% of the attack came from Indonesia.
Brazil and India provided about a combined 17% of the attack’s origin, which indicates that those countries have many infected devices.
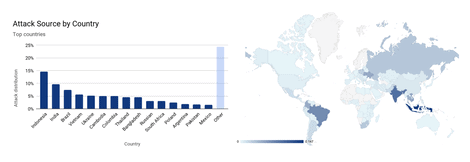
Source: Cloudflare
Yoachimik noted that the 17.2 million rps attack is the most expansive HTTP DDoS attack that Cloudflare has ever seen to date. This specific botnet has appeared at least twice over the past few weeks and targeted a different Cloudflare customer (a hosting provider) recently.
Botnets assemble
Two weeks before the hosting provider attack, Yoachimik says that a Mirai-variant botnet launched over a dozen UDP and TCP-based DDoS attacks, peaking multiple times over 1Tbps, with a maximum peak of 1.2Tbps.
Cloudflare customers, who include a renowned gaming company and major APAC-based telecom and hosting provider, are targets of attacks on the Magic Transit, Spectrum, and WAF/CDN services.
The Mirai botnet generated a significant volume of attack traffic but shrank down to 28,000 bots, having started with 30,000. It would seem that compromised devices that form botnets represent a growing security risk awaiting solutions.