
Biden says he won’t stand idly by as the US gets hit by cyberattacks
On the issue of the recent attacks on US federal agencies, president-elect Joe Biden has promised tougher responses during his tenure. In the statement that was issued by his transition team, Biden said that he had already been told by government officials, about the attacks, with possible Russian ... Read more

Microsoft and McAfee are part of a new Ransomware Task Force
Headlined by Microsoft and McAfee, a group of 19 security firms, non-profits, and tech companies announced plans to form a collective task force that will deal with the threat of ransomware.
The group has been named the Ransomware Task Force (RTF) and will focus on assessing the existing technic... Read more
MobileIron protects ‘every endpoint, wherever it is’
Within enterprises, thousands of endpoints often are active at once. Many times, these devices are not identical and are located everywhere. Properly securing all of these devices could be complex. Security provider MobileIron, however, responds to these issues. With its products, it wants to help ... Read more

Report: long-standing vulnerabilities threaten 5G Smartphone users
EU agency also issues its own report highlighting threats from 5G.
Global cybersecurity firm Positive Technologies have published their latest report on 5G security this week. The report, "5G standalone core security assessment," discusses vulnerabilities and threats for subscribers and mobile n... Read more

Malicious mobile emulator farms are robbing US and EU banks
IBM Trusteer researchers have uncovered an extensive fraud operation unlike anything anyone has ever seen before. In simpler terms, it is the nightmare of automated fraud. A network of mobile device emulators was used to steal millions of dollars from bank accounts in just a few days.
The scale ... Read more

Microsoft is creating a world without passwords
The password system we use today pre-dates the Internet.
Fernando Corbato is the American computer scientist whom many say created the computer password. He developed the Compatible Time-Sharing System (CTSS) in the 1960's. His eureka moment was to create a way for people to share a computer wh... Read more

Third party browser extensions infect millions with malware
Researchers say that around 3 million people worldwide have been affected.
Threat Intelligence researchers from Avast this week announced that they have found 28 extensions for the Google Chrome and Microsoft Edge browsers that contain malware.
According to Avast, the add-ons presented thems... Read more

New Information-Stealing Trojan goes after Outlook files and more
Python-based malware family targets Microsoft users to steal Outlook processes and browser credentials.
The good people at Palo Alto Networks have identified a new cybersecurity threat. Their Unit 42 researchers have been tracking the threat group AridViper, which has been targeting the Middle E... Read more
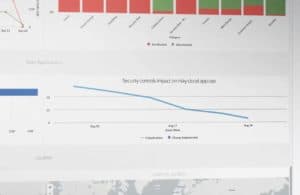
Netskope’s cloud perimeter secures enterprise data
How do you achieve the desired level of security with the right tools? Many security vendors are currently looking for the answer. Consolidation is a smart move, according to many experts. Netskope, which has been active in the market for a number of years now, also sees bringing together security ... Read more

Trend Micro issues Cybersecurity threat predictions for 2021
Forecast indicates that remote and cloud-based systems will be aggressively targeted in the coming year
Trend Micro this week issued its predictions for cybersecurity trends in 2021. In its forecast, the company predicts that cybercriminals will target home networks, remote working software and ... Read more









