Within enterprises, thousands of endpoints often are active at once. Many times, these devices are not identical and are located everywhere. Properly securing all of these devices could be complex. Security provider MobileIron, however, responds to these issues. With its products, it wants to help make the ‘Everywhere Enterprise’ possible and secure: employees are working everywhere, and data and devices are located all over the place.
MobileIron started as a Mobile Device Management (MDM) vendor. An MDM platform is used to manage mobile devices, such as iOS and Android devices. Over the years, many features were added to the MDM solution, making it a broad platform fort management and security tasks. All endpoints of an enterprise, including Windows 10 and macOS devices, can be managed within one platform.
To catch up with recent innovation, we got an update from Global Lead Solutions Enablement Maxime Chardome and Regional Sales Director Benelux Arjan Veenboer.
Everywhere Enterprise
Most of the activities are dedicated to support the Everywhere Enterprise. The Everywhere Enterprise is how MobileIron sees the current business world and workplaces, where valuable assets of enterprises are everywhere. Of course, this is because staff members work everywhere: in the office, at home, on the road, in the warehouse and so on. Because of this scattered landscape, the endpoints, the data, the infrastructure, the customers and the employees are scattered all over the place. The world has become incredibly hybrid.

A very strong on-premise endpoint security strategy alone is no longer sufficient. This was already somewhat the case before the coronavirus outbreak, with mobile working on the rise. However, the coronavirus accelerated this shift. Companies have responded by speeding up the roll-out of all kinds of IT services. Cloud-based services are increasingly popular, as they can help the Everywhere Enterprise.
Cybercriminals are also aware of these changing circumstances. They are adapting their attacks to the new situation. For example, the use of phishing attacks has become more attractive. If hackers can use this to get their hands on credentials, they can extract data like sensitive business information from cloud services. In theory, a single successful phishing attack can cause serious damage. Like this, several types of attacks have recently seen a boost in popularity. Hackers are trying to gain access to businesses and their information in a variety of ways via devices, networks and applications.

Unified Endpoint Management as a foundation
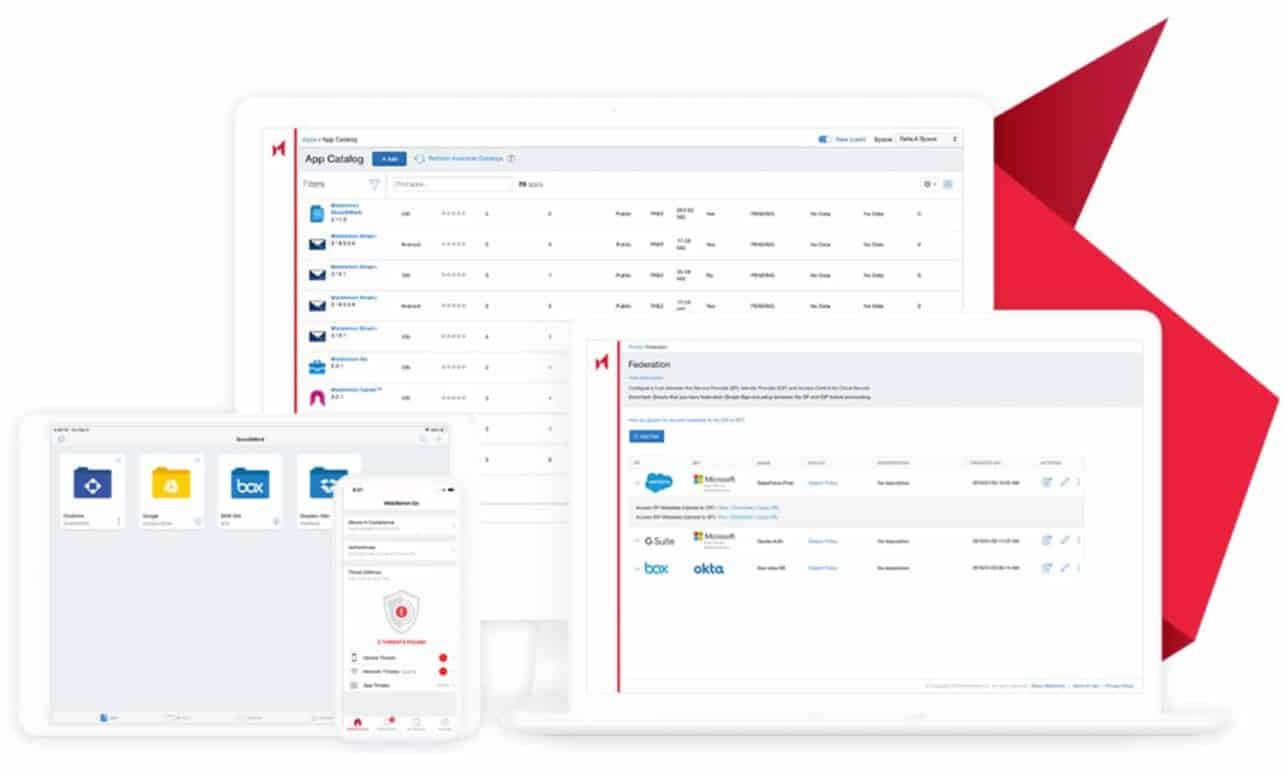
MobileIron’s answer is to deploy a Unified Endpoint Management (UEM) solution. This grants administrators access to a single console, from which they can manage security for all devices within the organisation. They can provide the apps, settings and configurations that are required to guarantee the security of the company data. Administrators can, if they wish, push a configuration to multiple endpoints at once, without having to go through each device separately.
This is also extremely useful for the end-user. The user probably prefers to work with either Android, iOS, Windows 10 or macOS and can now work with his platform of choice within an established security policy. MobileIron supports all these operating systems. Imagine an enterprise that purchases 1,000 Windows 10 laptops to support working from home. In that case, employees can be sure that the devices comply with the standards of the IT department. After all, the desired settings and required apps and tools are available right away. UEM also ensures that the devices continue to comply with the set guidelines. Managed devices offer IT departments insight into what is going on in the endpoint landscape. For example, UEM can see when an app that is necessary for the security policy has been removed from a managed device and can take appropriate action. The software could then block the device from accessing company data.

However, IT administrators are also looking for better securing of unmanaged devices, such as employees’ private devices that access company data. You want to have the necessary security assurances when they access sensitive data. It is therefore important for the protection of unmanaged endpoints to adopt a zero-trust approach, MobileIron says. With this approach, only users, devices and services that should have access to the valuable company assets can actually get in. Don’t trust anything, always verify. That is the idea of zero-trust.
Tip: MobileIron’s Zero trust platform uses mobile devices as a digital ID
Extra security with Threat Defense
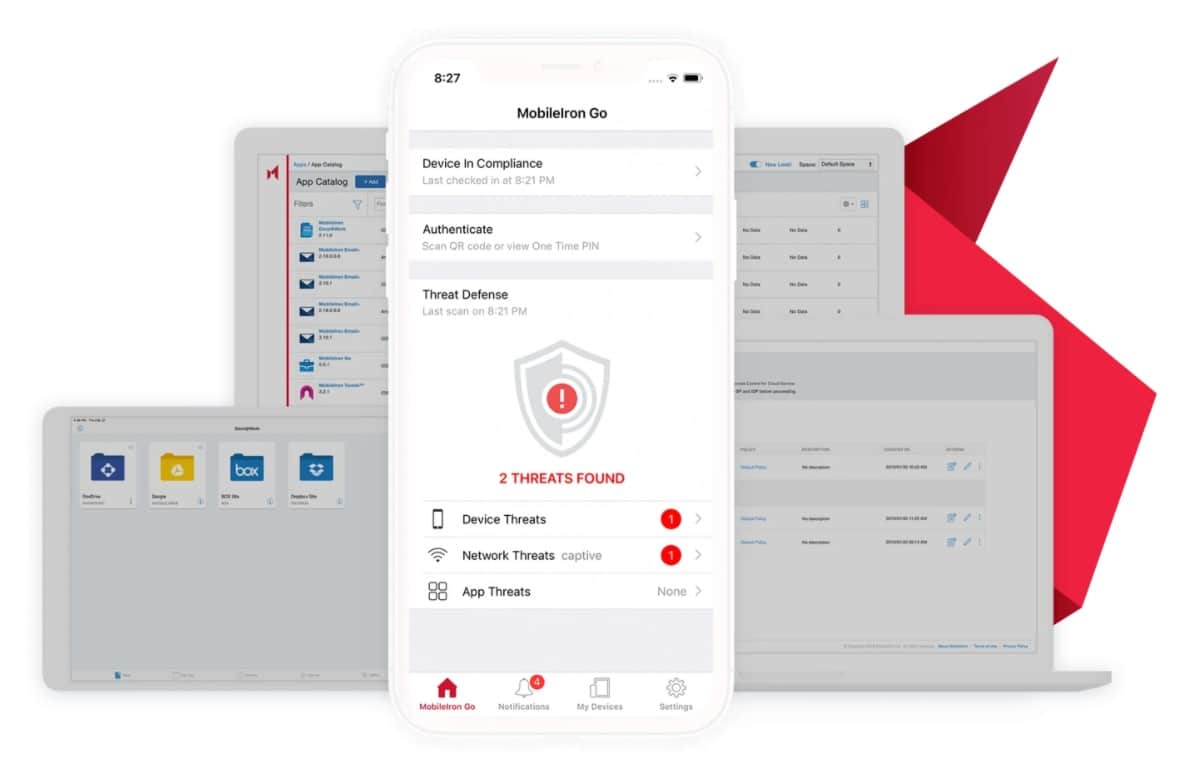
MobileIron has implemented the zero trust principle in most of its services. The company also did so with the Threat Defense (MTD) service, an extra module of the UEM platform. This enables MobileIron to protect iOS and Android devices against attacks that occur at device, network and application level, as well as to prevent phishing attacks. MTD does not require an internet connection, as the required technology is installed on the device and uses machine learning algorithms. These algorithms are capable of continuously detecting important threats. They also check for suspicious URLs in e.g. phishing emails, SMS, etc.
MTD is a component integrated into the MobileIron UEM client that is present on the devices. It has little impact on performance. Because MTD is integrated into the UEM client, the user doesn’t need to install extra apps on the device or follow a complicated procedure for installation, and the IT Security department can be certain that the extra security is active on 100 per cent of the devices. MobileIron strongly believes in this method of threat detection. Mobile threat detection solutions that heavily depend on the cloud also exist. When a threat is detected via the cloud connection, the UEM platform is then notified, and instructions are given to the UEM agent on the device to deal with the attack. Such an approach does not work if there is no cloud connection. MobileIron’s MTD service will actually perform detections on the device itself.
Eliminate unsafe passwords
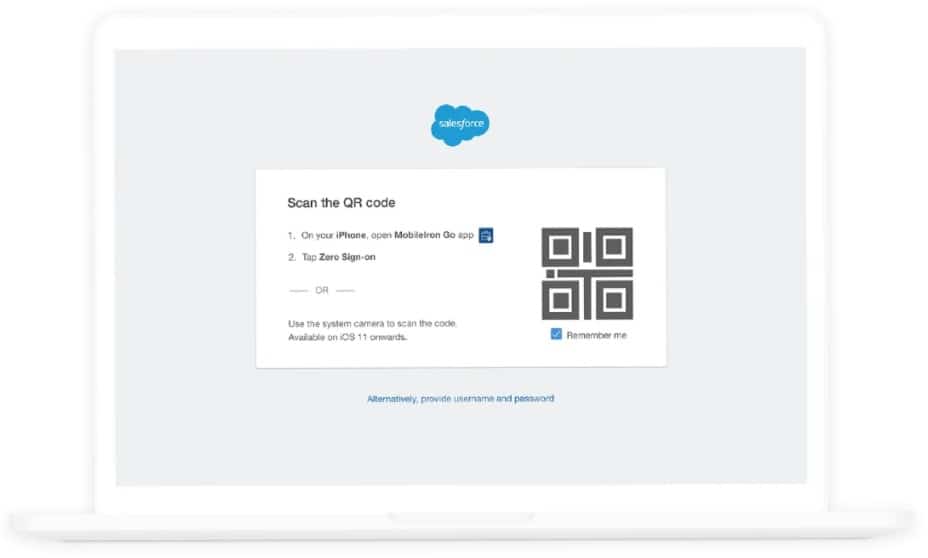
There is a third layer that helps secure the Everywhere Enterprise: Zero Sign-On (ZSO). The deployment of ZSO fits in well within the zero trust principle. ZSO will make logging in with a username and password a thing of the past. Instead, an iOS or Android device will be used for identification, for example by using biometric data as a factor for secure login. We already often do this in consumer applications with solutions like Apple Pay or logging in to banking apps. Here too, certificates are often used with an extra factor such as biometric data for verification. The zero-trust approach must ensure that ZSO is completely secure: it verifies the user, the device, the network and the apps used.
Tip: “Most IT managers want to get rid of password authentication.
This method is relatively simple for employees. Password-free access can be granted to applications such as Microsoft Office 365, Salesforce, SAP, Oracle and Workday. In addition, getting rid of passwords greatly reduces the risk of data loss due to stolen login data. It is a small step for end-users, but it will greatly reduce phishing. Since no passwords exist, there are no login credentials to steal and the overall security improves. Moreover, users and administrators will no longer be burdened with resetting passwords, because they can no longer be lost.
Layered approach for the enterprise of the future
MobileIron chooses to let three very strong layers complement each other. Unified Endpoint Management takes a central role, complemented by Threat Defense and Zero Sign-On. By using a zero-trust approach, the management and security of endpoints must be simple and smooth. This is to support the Everywhere Enterprise: a modern organisation where infrastructure, customers and employees can be located all over the world.

It is also good to see that MobileIron is offering more and more services in addition to its traditional endpoint management activities. This allows IT admins to respond to the growing number of attacks by cybercriminals. In this respect, the company is constantly looking at what else it can do for endpoint security, with an important focus on ease of management and use.
Tip: Ivanti completes acquisition of MobileIron and Pulse Secure