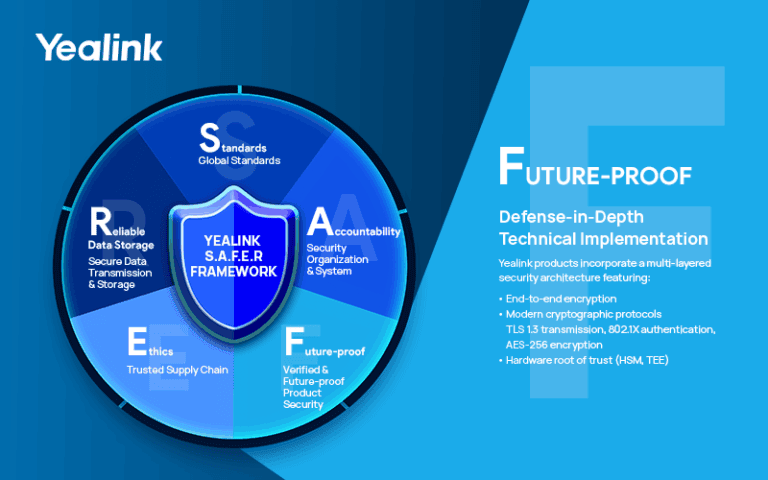
What does it mean to be “safer with Yealink”, as the company’s slogan suggests? A combination of five commitments work together to establish a secure foundation. These result in an end-to-end key management system and comprehensive protection, covering customer data, communication links and the entire device lifecycle.
Perhaps “Safer” isn’t the right way to put communication specialist Yealink’s promise here, but “SAFER”. It’s an abbreviation of Standards, Accountability, Future-proof, Ethics and Reliability. Together, they ensure that compliance is guaranteed, supply chains are secure and experts are on hand when needed. Demonstrating a future-proof (the aforementioned F) approach to product security, Yealink has implemented its End-to-End Key Management System as part of the forward-looking scheme of the SAFER framework. This intends to guarantee robust protection across all devices and communications. Role-based access control (RBAC) further locks down systems, providing robust safeguards for system security and data privacy.
Policies, policies
Ultimately, security rests on organizations implementing the instruments at their disposal. Access control policies rely on network isolation, least-privilege authentication through Ukey and key management. Yealink does as much as possible to prevent mishaps by making their devices secure by design. Examples include utilizing unique keys for each Yealink device in their respective Trusted Execution Environment, randomly generated keys in the HSM, and uniform management through Yealink’s Security Center.
Yealink further aims to avoid potential problems at key points in the device lifecycle. When a firmware update executes, the system establishes a trusted foundation through a Hardware Root of Trust, which integrates Secure Boot and firmware signature verification mechanisms. This ensures rigorous authentication at every stage from firmware loading to execution, effectively preventing malicious code injection and tampering. Yealink supports optional encrypted communication and integrity verification during the software update process to ensure fast, secure, and seamless updates. This multi-layered protection system not only enhances device security but also provides users with reliable usage guarantees, effectively addressing potential threats during firmware updates.
Firmware is further locked down thanks to encryption, signing with RSA4096 and SHA-512, transmission through TLS 1.3 connections and boot measures that deny unsigned firmware at startup. These measures make it obvious what the ‘end-to-end’ nature of Yealink’s security really is all about.
Never sitting still
However, security is not only end-to-end, but ever changing. Measures that were once more than enough coverage to combat cyber threats, are now compromises in waiting. Yealink therefore seeks to address future threats by improving today’s posture for tomorrow. In-depth collaborations with major security laboratories help to enhance technologies and safeguard against vulnerabilities we’ve yet to see.
Yealink also collaborates on the implementation of ISO/IEC 27001 and OWASP’s best security practices to raise whatever baseline companies should strive for today. More concretely, Yealink says it will offer deeper integrations of hardware-level chips in the future, continuous optimization of end-to-end encrypted communication protocols, and enhancements of end-to-end security auditing capabilities.
In conclusion, Yealink can only strive for the security organizations require in the present, but it does what it can to make the jump to covering tomorrow’s threats as short as possible. That’s what sums up this combination of factors that define the “Safer with Yealink” promise.
Also read: Yealink delivers secure collaboration with Microsoft’s MDEP