Key points:
- A ransomware attack targeting the ARINC vMUSE systems at Collin’s Aerospace caused widespread airport check-in disruptions.
- Affected were multiple airports across Europe forced to revert to manual operations such as issuing hand written boarding passes.
- This was not just a cyber incident but a supply chain failure with systemic consequences.
In late September 2025, several European airports reported significant delays and flight cancellations due to issues with their check-in and passenger systems. Collin’s Aerospace, the vendor of the vMUSE check-in system, had been hit by a ransomware attack.
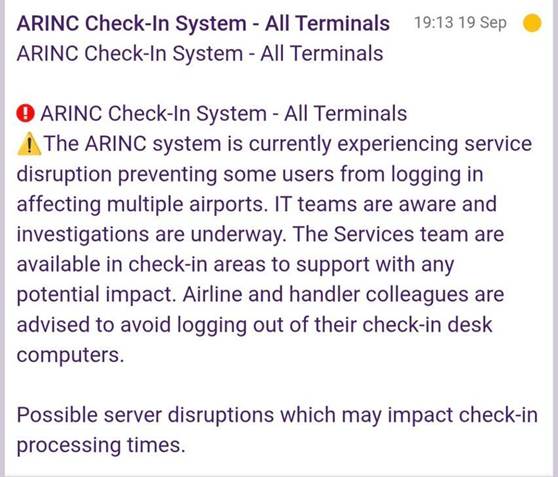
ARINC error message: Source: Cyberplace.social
Collins Aerospace operates ARINC AviNet, a virtual environment that hosts their ARINC vMUSE ground system for customers. Attackers exploited vulnerabilities in the ground system and its proprietary network, resulting in significant operational delays, reputational damage, and a loss of passenger trust. It is believed that the attackers accessed the shared AviNet network and subsequently encrypted portions of the ARINC Multi-User System Environment (vMUSE).
| Airport | Location |
| London Heathrow | United Kingdom |
| Glasgow Airport | United Kingdom |
| Berlin Schönefeld | Germany |
| Dublin Airport | Ireland |
| Cork Airport | Ireland |
| Brussels Airport | Belgium |
Strategic Lessons for Executives
Despite comprehensive regulations like NIS2, most organizations significantly underestimate the security risks stemming from a lack of visibility into their vendors’ security posture. Vendor risk management is not merely a compliance checkbox but a strategic issue of resilience, as this incident demonstrates how a third-party ransomware attack can ripple across entire ecosystems.
The incident was likely a result of security negligence. Researchers discovered several outdated systems (IIS 8.5, Glassfish 2014, Oracle 2015, and end-of-life Cisco ASA devices) that presented predictable vulnerabilities for attackers. Legacy systems represent not just technical debt but also significant business continuity risks. Therefore, modernization programs and operational investments must be integrated.
The effort airports invest in continuity planning was evident as fallback procedures were successfully invoked. While fallback was available, it proved highly disruptive. Furthermore, when experts attempted to restore the software, they were re-infected, indicating the ransomware was still present on the system. This highlights that detection, response, and recovery must be considered as a holistic process.
The incident clearly underscores the need to elevate cyber risk to the board level. The outage affected passenger experience, operational continuity, and brand reputation.
Strategic Imperatives
Supply chain security requires visibility, not just assurances, to mitigate the ripple effects when a vendor is compromised. Security assurance from vendors must evolve beyond simple checkbox exercises to in-depth analysis of their practices and configurations. Merely documenting compliance with ISO 27001, NIST, and NIS2 will no longer suffice. As high-impact cyber-attacks persist, organizations, especially those in critical infrastructure, will demand greater visibility and transparency from their vendors. When it comes to maintaining a country’s operations, the focus must shift from minimizing liability to ensuring continuity.
In sectors where legacy systems are prevalent, rigorous legacy management is essential. For systems with unpatchable vulnerabilities, compensating controls must be implemented, and a phased retirement of high-risk systems must be planned. Legacy systems are common in critical infrastructure, often deemed essential for continued operations and complex to replace. Without proper monitoring and maintenance, outdated systems and missing patches, as seen in cases like Collin’s Aerospace, will expose an organization’s vulnerabilities.
Strengthening supply chain governance is a critical step forward. Organizations should map out dependencies, conduct joint exercises, and establish contractual obligations for security monitoring. Developing resilience by design is the optimal approach. Investments in redundancy, the development and testing of rapid recovery processes, and regular crisis simulations are valuable tools for organizational preparedness.
Conclusion
Organizations in critical infrastructure must immediately stop prioritizing liability reduction which compliance requirements often falsely are interpreted as. Instead, nation-states must incentivize business continuity and offer guidance and oversight to small and medium businesses that cannot afford to develop their own resilience functions. Incentives must be structured so that organizations perceive expensive cybersecurity investments as worthwhile, leading to greater risk reduction and fewer losses.
This approach is crucial for improving supply chain risk management in critical infrastructure, where adversaries are likely to exploit weaknesses. Policymakers must advocate for stronger regulatory oversight and shared responsibility models, particularly in aviation. Executives must view cybersecurity as a strategic business enabler, rather than a technical afterthought.
