
How do the RagnarLocker cybercriminals operate?
Israeli cybersecurity company Sygnia has set its sights on RagnarLocker, a group of ransomware criminals. Using a hodgepodge of self-developed tools and commercial software, the hackers look to penetrate organisational networks, encrypt important data and demand a crypto ransom from their victims.
... Read more

Israeli threat actor hacks civil society in 10 countries, reports say
Two new threat analyses expose a new player in the field of targeted hacking for intelligence gathering.
New research published this week by Microsoft and the internet watchdog Citizen Lab detail the operations of a new Israeli spyware company targeting journalists, politicians, opposition figur... Read more

CrowdStrike introduces protection for xIoT devices
CrowdStrike announced this morning that it is expanding its CrowdStrike Falcon platform. The expansion includes the first solution to provide EDR/XDR protection for xIoT (extended Internet-of-Things) devices.
CrowdStrike responds to the digital transformation that is currently affecting many ind... Read more

Netskope launches faster, more secure software service
Netskope is integrating its offerings with a new software service. Netskope Endpoint SD-WAN combines two techniques of cloud and network architecture. In this way, legacy problems should be solved.
The company says the service will become available later this year. Users deploy Netskope's Secure... Read more

Small number of security vulnerabilities pose biggest threat
Three-quarters of security vulnerabilities pose hardly any risk. The real danger comes from a very small number of vulnerabilities, especially those where attack paths converge at points leading to important business assets.
This is stated by security vendor XM Cyber in a recent survey. XM Cybe... Read more
Apple releases latest security patches for older devices
Last week's security updates are now available for older iPhones, iPads, and Macs.
This week Apple released iOS and iPadOS 15.7.5, macOS Monterey 12.6.5, and macOS Big Sur 11.7.6 to patch two security vulnerabilities in older devices that are still receiving software updates but aren’t capable... Read more

Hard action against illegal Cobalt Strike providers
Microsoft, Fortra and the non-profit organization Health-ISAC are jointly cracking down on providers of illegal Cobalt Strike copies. This is to prevent more abuse of the legal tool.
The tech companies and the U.S. nonprofit have permission from a U.S. judge for the action. The goal of the actio... Read more

Ransomware gang wants $4 Million from MSI for data theft
Taiwanese hardware giant is being extorted by a gang who claims to have stolen their source code.
A newly formed ransomware gang is demanding a giant payment from MSI after claiming to have stolen a bonanza of data, reports BleepingComputer.
The gang calling themselves "Money Message" is new ... Read more

Security pros are often pressured not to disclose data breaches
A new study finds that nearly half of security practitioners are being told to ‘keep data breaches under wraps’.
A new study published this week shows almost half of cyber security professionals are pressured to keep data breaches secret, according to ITPro.
The survey of 400 IT and secur... Read more
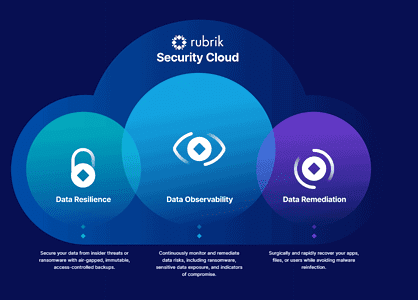
Back-ups should be part of a modern layered security approach
Rubrik has recently been increasingly asserting itself as a security vendor. The announcement in late 2022 of Cyber Recovery seemed like a good reason to talk to Anneka Gupta, Rubrik's Chief Product Officer. What can we expect from Rubrik and more generally from backups in terms of security?
Wit... Read more









