Microsoft, Fortra and the non-profit organization Health-ISAC are jointly cracking down on providers of illegal Cobalt Strike copies. This is to prevent more abuse of the legal tool.
The tech companies and the U.S. nonprofit have permission from a U.S. judge for the action. The goal of the action is to track down and take offline illegal copies of old versions of the tool worldwide. Both Microsoft and Fortra want their (security) tools and services to be used legitimately.
Legal actions
More specifically, the companies and the nonprofit can now seize domain names and take offline the IP addresses of servers hosting the pirated versions. Techniques they use to do this are detection, analysis, telemetry and reverse engineering. This combined with other data and insights.
They will also cooperate with relevant CERTs and Internet service providers. The first actions have already started.
Cobalt Strike
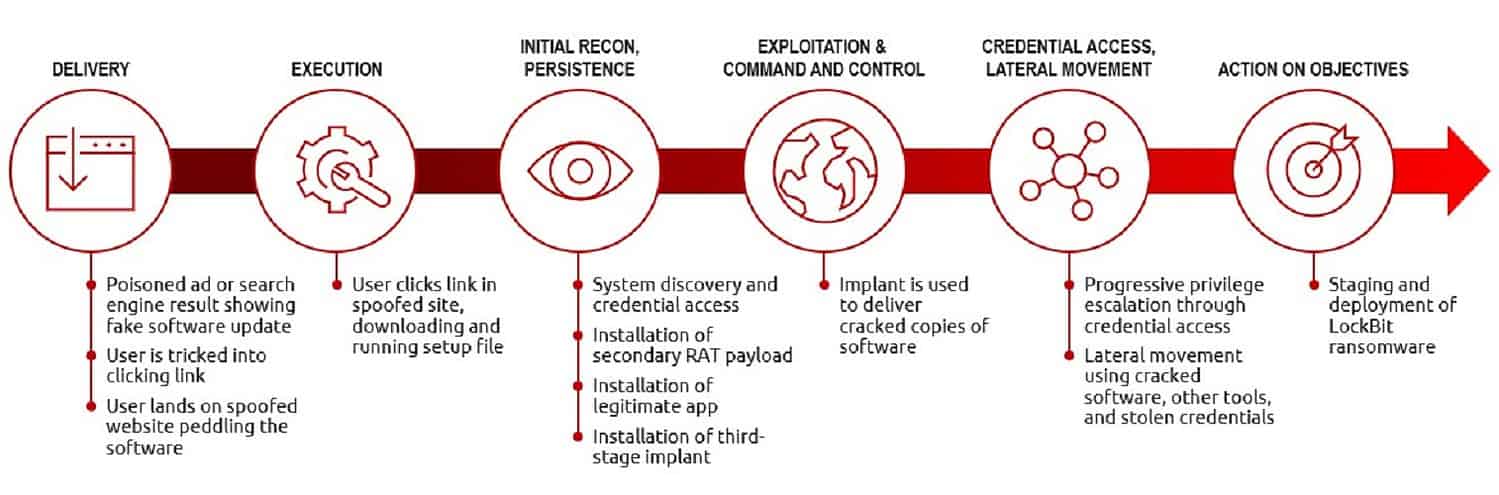
Cobalt Strike was developed by Fortra in 2012 as a legitimate product for pen testing. Red teams can use it to scan companies’ infrastructure for vulnerabilities.
The tool is also abused by cybercriminals for scanning networks for vulnerabilities. Especially for more persistent-access to affected infrastructures. For example, for “harvesting” sensitive data or spreading other malware such as ransomware.
So-called statesponsored cybercriminals also abuse the tool. Malicious use of Cobalt Strike is often found in China and Russia, but also in Vietnam and Iran.
Also read: Google Cloud protects customers from rogue Cobalt Strike attacks