Google Cloud announced new functionality for detecting Cobalt Strike-based cyberattacks.
Although Cobalt Strike was designed as a legitimate pentesting tool, the software’s often abused by cybercriminals to penetrate networks. Cobalt Strike’s pre-configured tools are particularly popular for remote access attacks and ransomware drops.
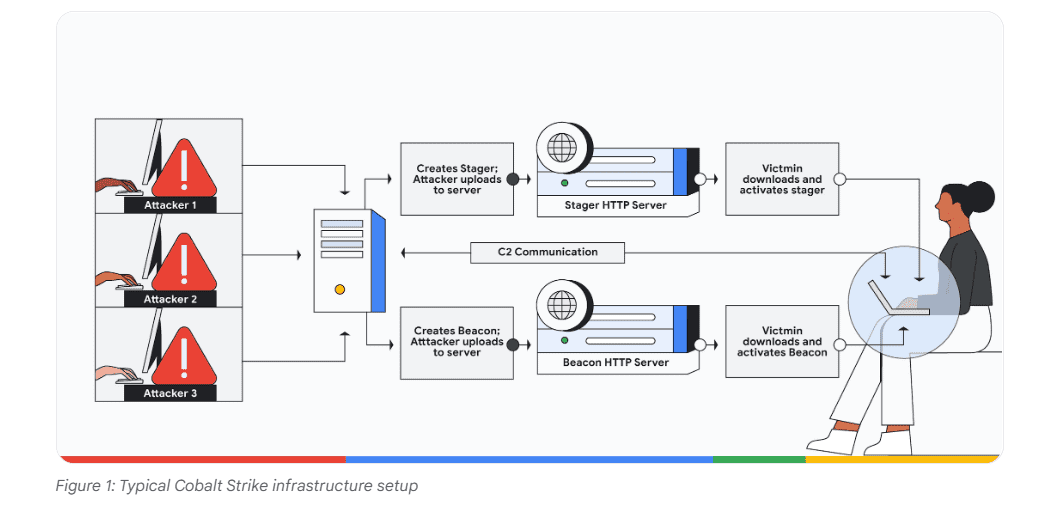
Google recently launched a set of new open-source YARA rules that provide access to 165 detection signatures across various versions of Cobalt Strike. The signatures scan as many as 300 different Cobalt Strike binaries. The binaries are divided into unique JAR files, stagers, templates and beacons.
Together, the YARA rules form a VirusTotal Collection that allows security experts to record and identify the various components and versions of Cobalt Strike. Ultimately, the release helps prevent Cobalt Strike abuse at an early stage.
Return to red teams
According to Google Cloud, recent and legitimate versions of Cobalt Strike are unaffected by the detection rules. The rules are designed to uncover illegitimate users of Cobalt Strike.
The release is one of the ways in which the security industry is attempting to take Cobalt Strike from cybercriminals and put it back into the hands of legitimate red teams.