The 8Base ransomware group has been detected since March 2022, but has suddenly become much more active in the past month than before. The hacker collective uses known cybercrime methods, but is suddenly operating at lightning speed with victims in many industries. VMware warns in a blog of the danger the group presents.
8Base describes itself as a group of “simple pen-testers”, short for “penetration testers.” This can in principle be a legitimate service. With this group, it is patently not, owing to the fact it demands a ransom after hacking their supposed ‘customers’. Like other cybercriminals, 8Base maintains a “leak site,” where victims’ data becomes available if people are unwilling to pay a ransom.
Interestingly, security experts have not yet figured out the malicious actors’ exact methodology, motivation and identity. What is clear, however, is that the group operates quickly and efficiently.
What VMware discovered
VMware’s analysis shows that 8Base’s communication style is strikingly similar to that of RansomHouse, another criminal organization. That group came into the crosshairs of cyber experts earlier this year, when it was revealed to have carried out a giant hack on AMD with 450GB of financial data and research data. However, it is not entirely clear whether we can call this collective a proper ransomware gang, as VMware describes that it buys stolen data and tries to extort companies on that basis.
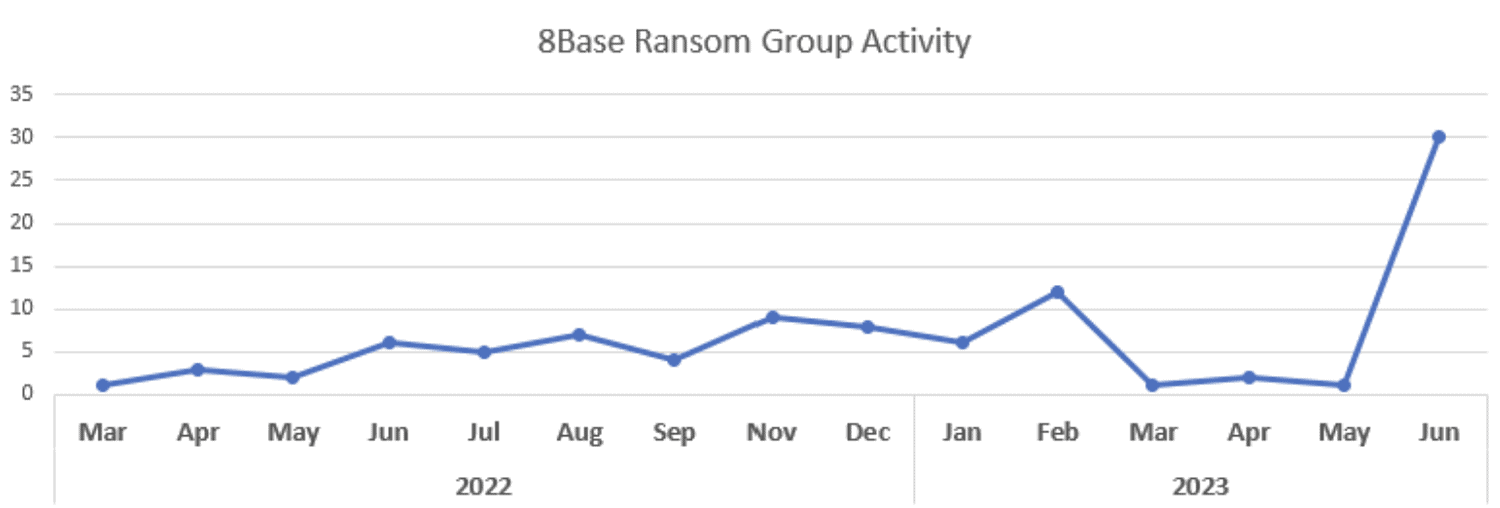
The statistics regarding 8Base activity are pretty clear: in June, the ransomware gang went from having the fewest detections in more than a year to the most by far.
The targets vary widely, from business-oriented service providers to financial services, manufacturing, IT and healthcare. For that reason, VMware characterizes the choice of victims as “opportunistic.”
Unlike more brutal organizations such as RagnarLocker, 8Base tries to maintain a tinge of authenticity. Under the guise of the aforementioned “pen tester” excuse, it claims to serve affected companies. On top of that, they have a full-fledged FAQ, Terms of Service and offer assurances about course of action after payment.
Unclear origin
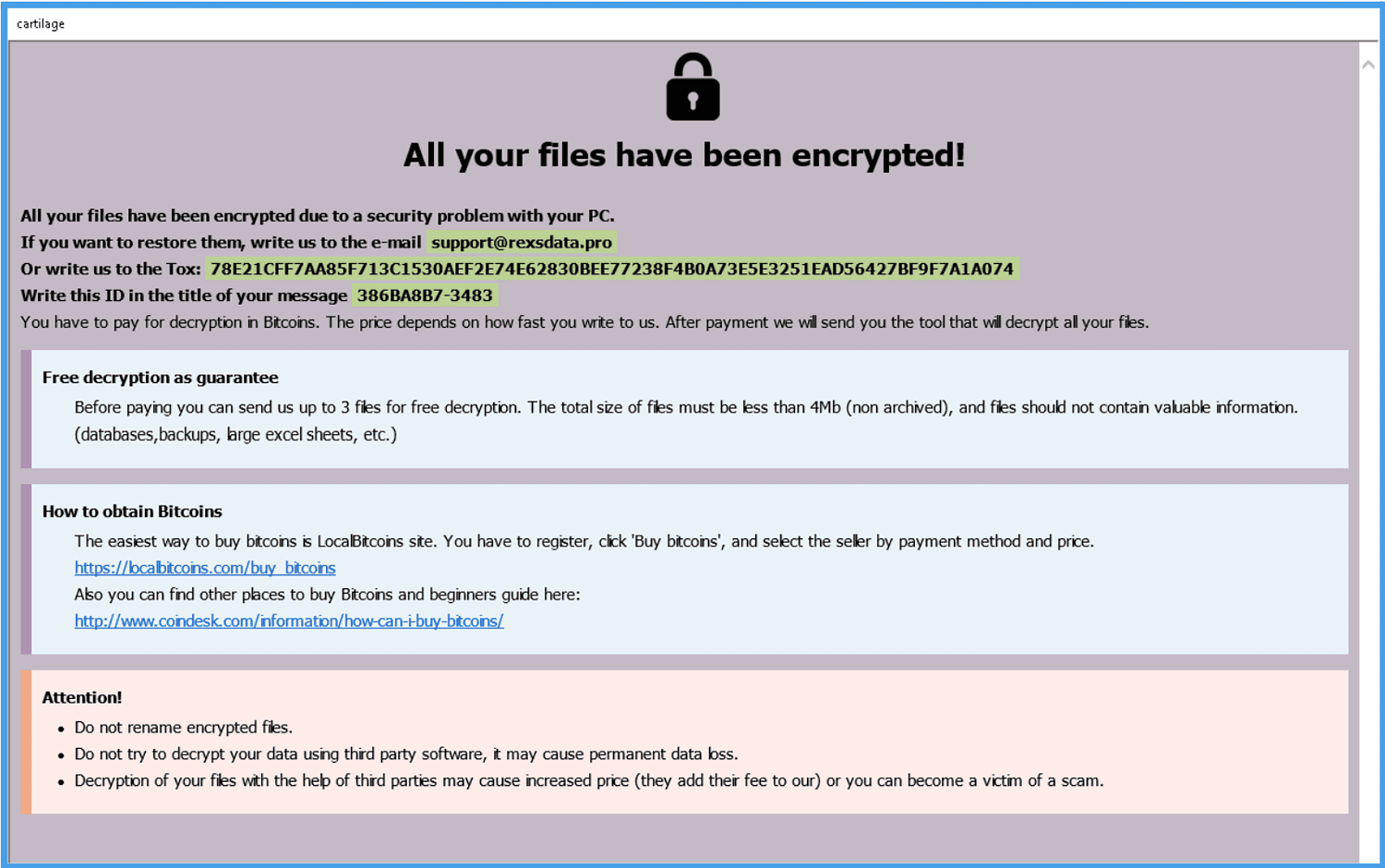
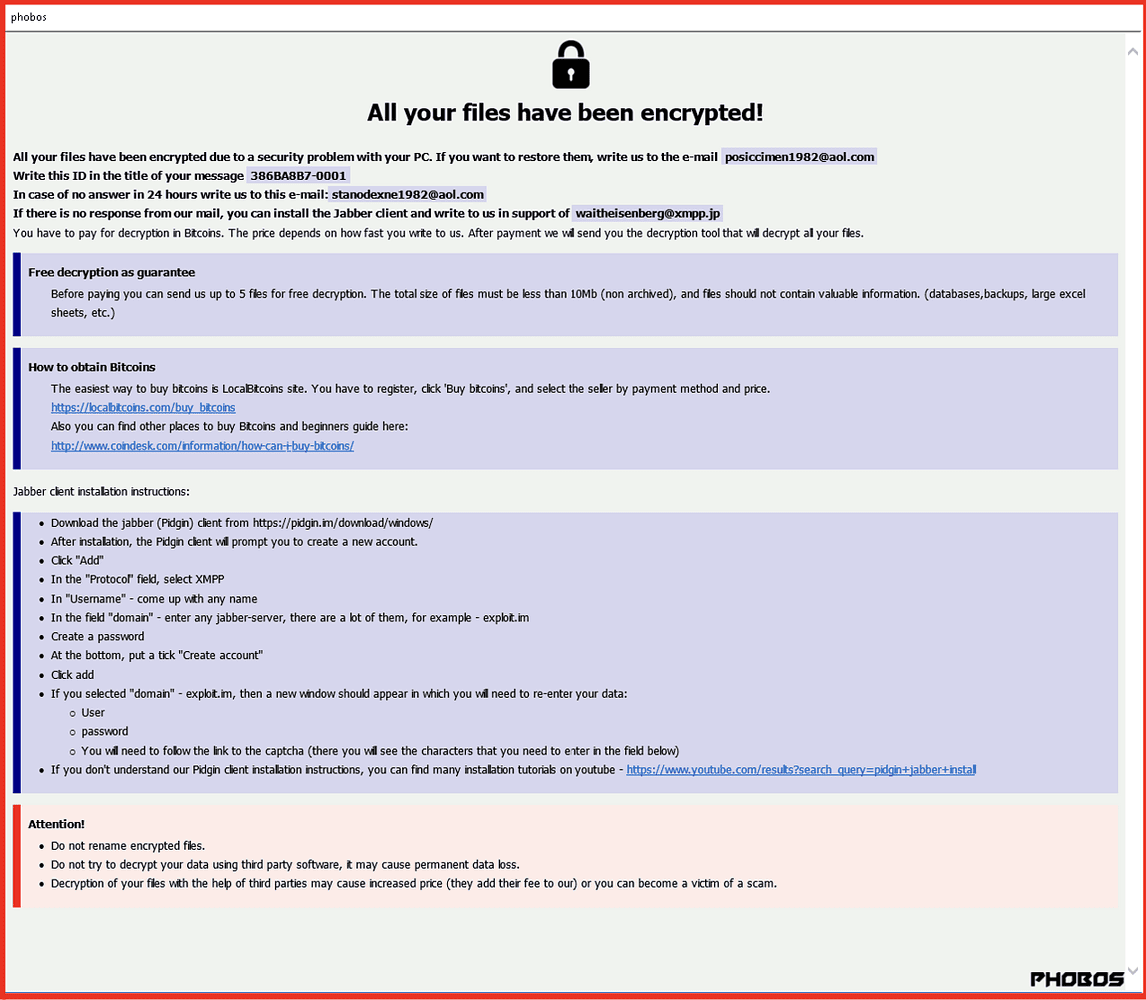
No specific ransomware software was found to be the basis for the practices in the 8Base detections. Also, the “ransom note” sometimes differed: VMware detected one similar to that of RansomHouse and one more reminiscent of another criminal group: Phobos.
Speculation only
As valuable as this information is, VMware, unfortunately, has to conclude that the rest is still speculation. Because of the different ransomware variants used by the group and the scattered targets, it is not yet possible to create a clear profile of the group.
For that reason, too, the advice VMware gives is somewhat generic even if clearly beneficial to would-be victims. Detecting phishing emails and deploying network monitoring the company maps out, on top of using its own Carbon Black Managed Detection and Response. There are many other security vendors like this, but for a larger organization, it is essential not to leave gaps. Endpoints, employees and the transfer areas between clouds are just three “attack vectors” that attackers prey on. 8Base’s rapid growth and diverse group of victims just go to show that there are ever-changing threats in the cybersecurity landscape.
For more information on protecting data from a ransomware attack, a white paper can be requested from Techzine by clicking the link below and filling out the form.
Also read: Defend your data from a ransomware attack