The well-known IEE 802.11 WiFi protocol has a fundamental design flaw in its security, according to researchers at Northeastern University in Boston and KU Leuven. The flaw allows access points to leak so-called “network frames” in plaintext. Cisco has since acknowledged this risk as the first provider of wireless solutions and applications.
According to recent research “Framing Frames: Bypassing Wi-Fi Encryption by Manipulating Transmit Queues,” the design flaw that makes the 802.11 WiFi protocol insecure is in so-called ‘network frames.’ These WiFi frames are data containers with a header, a data payload and trailer. The information contained in these specific data containers includes source and destination MAC addresses and control and management information, among other things.
The frames or containers are arranged in a controlled manner by the 802.11 protocol into neat queues and eventually transmitted. This should prevent collisions between these data packets and improve performance for data exchange. For this purpose, the busy/idle states of the various receiving access points are monitored more specifically.
Also read: Cisco builds integrated and open security platform; what does that mean?
No good queue protection
The researchers have now discovered that the very frames or containers that are located or buffered in a queue are not well protected against attacks by cybercriminals. In doing so, the frames or containers in question are exposed to, among other things, manipulating data transfers, client spoofing, redirecting the frames, as well as stealing them.
In this way, cybercriminals can take over TCP connections and intercept client and web traffic via various devices and operating systems, such as Linux, FreeBSD, iOS and Android.
Power saving the cause
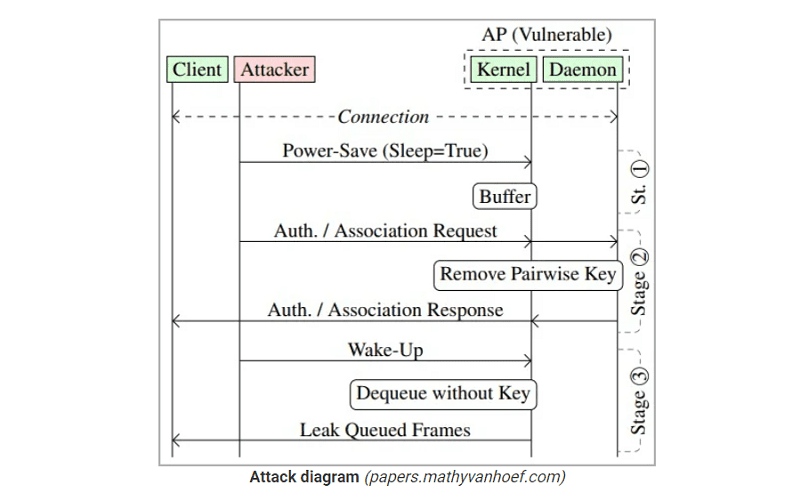
The cause of this vulnerability lies in a power saving mechanism within the 802.11 WiFi standard. This power saving mechanism allows WiFi devices to save energy by buffering or queuing frames or data containers for network devices that are in “sleep mode”.
When a WiFi client is in “sleep mode,” it sends a frame to an access point with the power saving functionality. This causes all frames destined for this client to be queued until the client ‘wakes up’ again.
However, for these queued frames, there is no provision for their security. Also, there is no limit on the duration of the state of these frames. Only when the client wakes up, the frames are taken out of the queue again, encrypted and sent to the destination.
The researchers now indicate that queued frames are vulnerable to attack. Cybercriminals can spoof Mac addresses of other devices on the network and then send these power-saving frames to access points. This then causes these access points to set up frames for the spoofed client. The cybercriminals then send a wake-up call to receive the stack of frames.
Customize encryption
Although sent frames are often encrypted with a key shared by all devices on the network or a unique key for each device, the cybercriminals can also modify this for their own gain.
This by changing the security context of the frames by sending authentication and “association” frames to the access point. This forces the access point to send the contents of the frames in plaintext or encrypt them with a key provided by the attackers. With dire consequences.
Different vendors vulnerable
The specialists from Northeastern University in Boston and KU Leuven indicate that cybercriminals can perform the hack with some hacking tools. For this purpose, they developed their own tool: MacStealer. This tool can test WiFi networks for so-called “client isolation bypasses” and intercept traffic to other clients in the MAC layer.
Especially WiFi devices from manufacturers such as Lancom, HPE Aruba, Cisco, Asus and D-Link would be susceptible to the described method of attack. In addition to intercepting and stealing WiFi data, the attack technique could also be used to inject malicious JavaScript content into TCP packets. Eavesdropping on web traffic is also possible, but limited due to encryption by the TLS protocol
Hacks performed via the now-found vulnerability are not known so far (fortunately).
Cisco admits risk
Meanwhile, Cisco has become the first vendor to acknowledge that the vulnerability discovered by the researchers in the 802.11 protocol for its WiFi devices could lead to security problems. This mainly concerns the Cisco Wireless Access Point products and the Cisco Meraki solutions and applications with wireless capabilities.
The vendor does note that the discovered vulnerability compromises the entire security of a properly secured and configured network.
Cisco does urge its customers to secure their networks with mechanisms that enforce policies through systems such as the Cisco Identity Services Engine (ISE). This solution helps customers restrict network access by implementing Cisco TrustSec or so-called Software Denied Access (SDA) technology.