Researchers from security specialist Wiz Research penetrated the backend of Microsoft Bing through a misconfiguration in Azure App Services and Azure Functions. This allowed them to manipulate search results and add malicious code.
The security specialists discovered the so-called BingBang vulnerability through a misconfigured application in Azure App Services and Azure Functions. This misconfiguration allowed any Azure user, even public users, to access the specific application.
More specifically, it involved a misconfiguration of Azure Active Directory. When an incorrect option is chosen in the backend to give users access to a particular location, anyone with an Azure account can gain access.
Further research by Wiz Research found that about 25 percent of apps to which multiple users have access contain misconfigurations and are open to any Azure user.
Microsoft Bing also affected
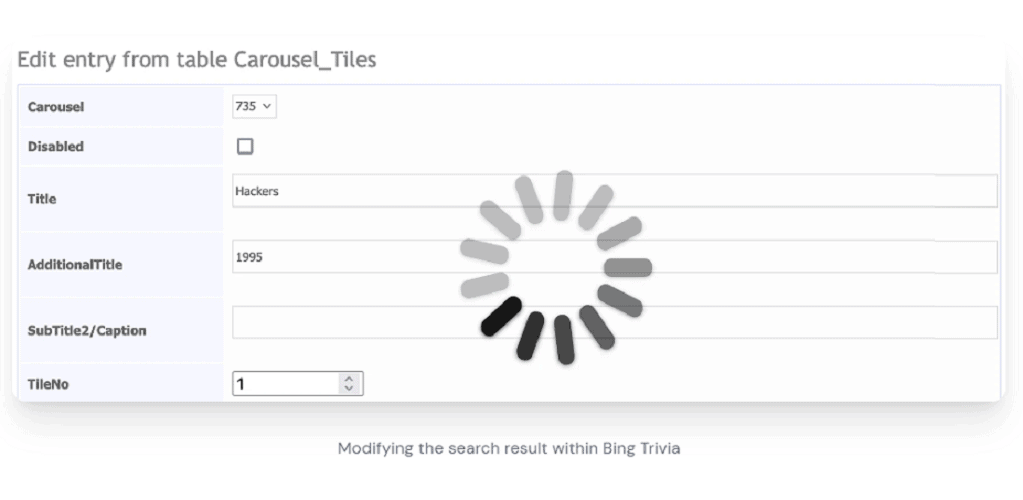
The research found that even at Microsoft itself, Azure apps are open to all users. Wiz Research specialists discovered, for example, that the Bing Trivia app was open. This app provided access to a CMS that allowed researchers to modify live search results in Microsoft’s Bing search engine.
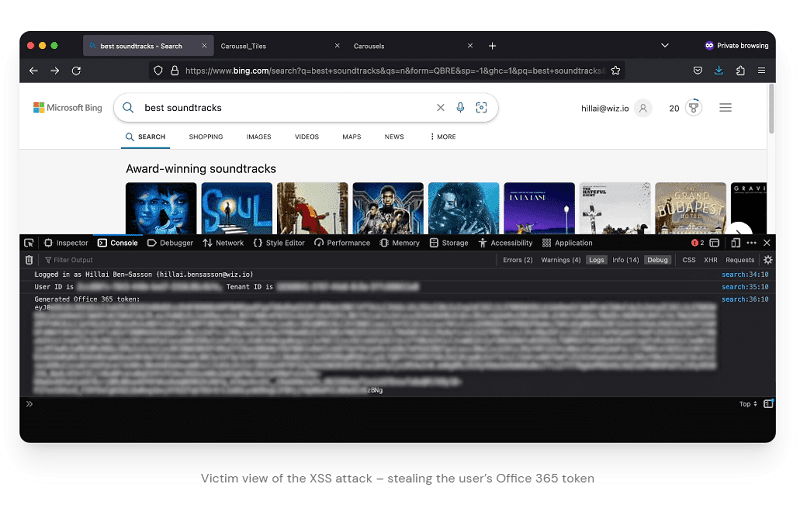
In addition to manipulating the search results, the security experts could also upload malicious XSS code. This allowed them to intercept the Microsoft 365 tokens of Microsoft users who viewed the manipulated search results.
With these tokens, cybercriminals could, in turn, penetrate other Microsoft 365 applications of end users. In this way, it is possible to see and steal emails from Outlook, calendar data, messages on MS Teams, SharePoint documents and OneDrive files.
Microsoft quickly fixes the problem
Security specialists notified Microsoft of the BingBang vulnerability in Azure Active Directory in late January. Microsoft implemented a fix almost immediately, although the tech giant did indicate that only a limited number of internal applications were open to every Azure user.
Microsoft further implemented additional security measures that prevented misconfigurations in Azure Active Directory from causing more problems. For example, by stopping issuing tokens to clients that are not registered in the “resource tenants. This restricts access to only properly registered clients.
This now applies to 99 percent of all client applications, Microsoft indicates. Various other security instructions have been issued for the remaining clients.
Bug bounty
Wiz Research researchers received a $40,000 bug bounty from Microsoft for finding the leak in Azure Active Directory and bringing it out responsibly. The vulnerability was published only after all affected Azure platforms had closed the leak.
Also read: Microsoft Defender identifies Google and Zoom as malicious