A known vulnerability in Ivanti Endpoint Manager Mobile is currently being actively exploited. Device management solution MobileIronCore is also vulnerable.
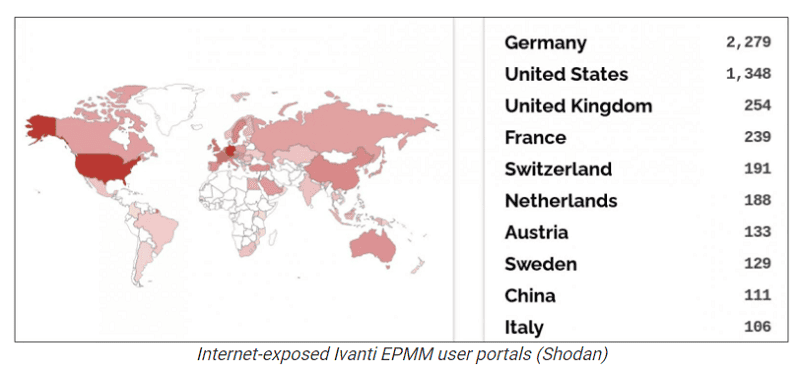
The U.S. security regulator CISA warns of this. The vulnerability is hits many Internet-connected devices. For example, data from Shodan shows that 6,300 Ivanti EPMM user portals are still visible on the Internet. Also, this monitoring platform indicates that more than 150 public organisations are vulnerable.
The Shadowserver platform notes 3,420 Ivanti EPMM appliances exposed on the public Internet.
CVE-2023-35082
CVE-2023-35082 allows, remotely, an unauthorized authentication bypass. This allows hackers to access personal identifiable information of end users of mobile devices. It allows them to install backdoors on affected servers when this vulnerability is combined with other bugs.
The vulnerability affects Ivanti EPMM versions 11.10, 11.9 and 11.8, and MobileIron Core versions 11.7 and below.
Patches have been made available by Ivanti since August 2023. CISA calls for these patches to be installed as soon as possible. U.S. government organizations must have implemented them by Feb. 2, 2024.
In addition to the Ivanti EPPM vulnerability, two other Ivanti vulnerabilities are now being actively exploited. These are the previously discovered vulnerabilities in Ivanti Connect Secure, CVE-2023-46805 and CVE-2024-21887.
There are reportedly already victims in both large and small businesses. In addition, about 1,700 ICS VPN appliances have already been affected by a backdoor installation via a GIFTEDVISITOR webshell variant.
Tip: Critical vulnerability in EPM software Ivanti lets hackers take over core server
