Chinese state hackers are using the Linux malware ‘Pygmy Goat’ in their continuous campaigns against government networks of Western countries. Security specialists from the UK National Cyber Security Center (NCSC) discovered that this malware specifically targets vulnerabilities in Sophos XG firewalls.
For the past five years, Chinese state hackers have continuously carried out cyber attacks on the government networks of mostly Western countries but also countries in South and Southeast Asia. In operation “Pacific Rim”, they mainly attack edge devices, especially Sophos XG firewalls. Devices from Fortinet, Barracuda, SonicWall, Check Point, D-Link, Cisco, Juniper, and NetGear are supposedly also among the targets.
Through the attacks, Chinese state hackers want to spy, but also (and much more importantly), steal sensitive data. Known Chinese state hackers potentially involved in this operation include Volt Typhoon, APT31 and APT41/Winnti.
Backdoor access
Researchers from the UK’s National Cyber Security Center (NCSC) have discovered the malware the Chinese state hackers are deploying in their attacks. In particular, this involves the Linux malware variant ‘Pygmy Goat’, which specifically targets Sophos XG firewalls.
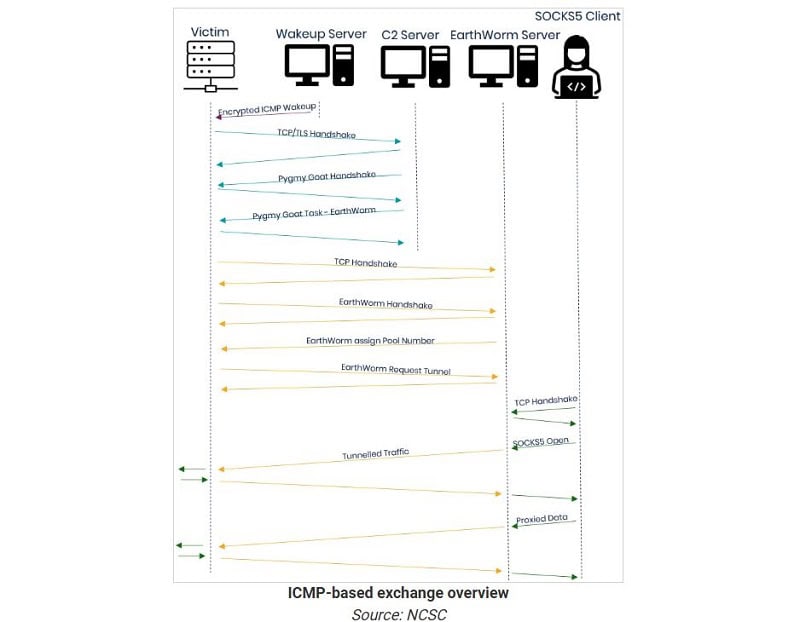
The new malware is a native x86-32 ELF shared object that aims to open backdoor access on an affected device. Among other things, the advanced malware manages to hide in legitimate Secure Shell (SSH) connections, thus evading detection.
Pygmy Goat is additionally capable of sending encrypted Internet Control Message Protocol (ICMP) packets between the malware and the hackers’ remote servers, further contributing to the malware’s attempt to achieve invisibility.
The malware also provides persistent access and control functionality on the affected firewalls, so Chinese state hackers can always continue to secretly manipulate the infected devices. UK NCSC researchers indicate this may also lead to deeper access to the attacked network infrastructure.
Similarities and previous use
BleepingComputer further reports that the Pygmy Goat malware is similar to previous malware from Chinese state hackers. The techniques, tactics, and procedures of the now-discovered Linux malware are said to be reminiscent of the ‘Castletap’ malware that Mandiant previously associated with Chinese state hackers.
The Pygmy Goat malware was also reportedly used in an attack by the Chinese state hacker group ‘Tstark’ in 2022.
Also read: MITRE discovered Chinese hack only months after exploitation