Research by security specialist Cyble indicates that more than 900,000 Kubernetes clusters are vulnerable to malicious scans and data theft. The researchers urge organizations to increase their focus on cluster security.
Cyble’s researchers came across more than 900,000 vulnerable Kubernetes clusters during an exercise. The vulnerable Kubernetes clusters were found on three ports: 443, 10250 and 6443. Most listened to port 443.
When called, the majority of vulnerable clusters returned status code 403. This means that the Kubelet API accepts an unauthorised request, but won’t allow the caller to visit the endpoint in question. Status code 401 was common as well. This means that a Kubernetes cluster is functional and may be vulnerable to exploits.
Cybercriminals can use the same scanning method to map the Kubernetes environments of targets. Furthermore, Kubernetes Dashboards are rarely password-protected, and therefore vulnerable to attacks.
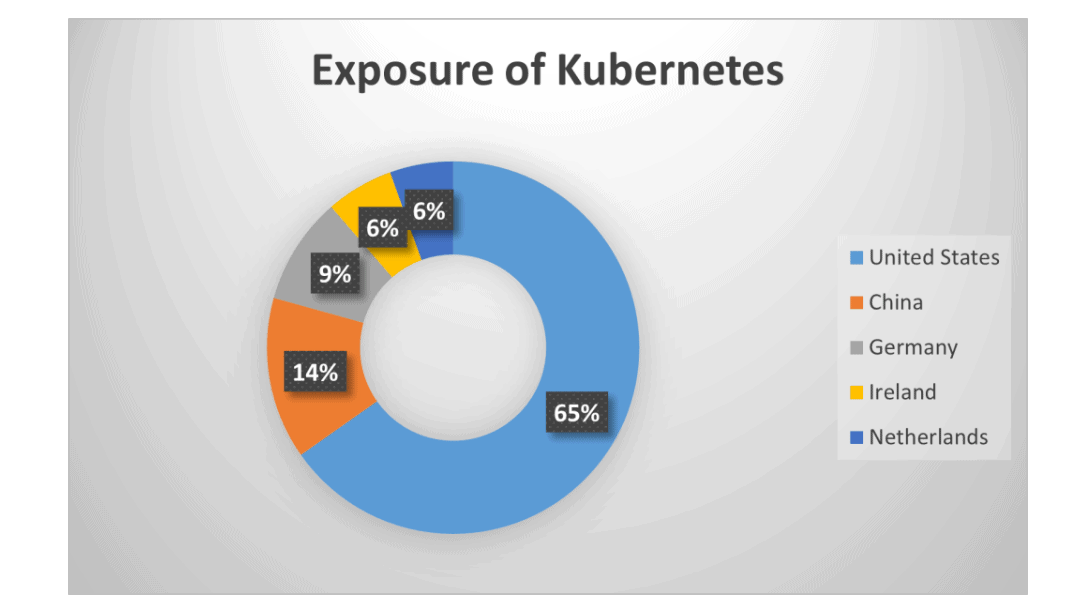
Most vulnerable Kubernetes clusters were found in the United States (65 percent). Clusters in China, Germany, Ireland and the Netherlands were relatively vulnerable as well.
Configuration
The researchers urge companies to improve their security posture in Kubernetes environments. Misconfigurations are particularly common. Examples include the usage of default container names, open service ports and password-less Kubernetes Dashboards.
Tip: Veeam releases Kasten K10 V5.0 with stronger Kubernetes security