
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Thousands of Citrix servers vulnerable once again
Thousands of Citrix Netscaler ADC and Gateway servers are vulnerable to remote code execution (RCE) attacks. ...

Mallox ransomware targeting Windows is on the rise
Ransomware group Mallox is on a steep rise. The attack targeting Windows systems is experiencing an increase ...

OpenAI credentials for sale on dark web
The data of hundreds of thousands of OpenAI accounts are being offered for sale on the dark web. This is a...

Kevin Mitnick, former most wanted hacker, dies at 59
Kevin Mitnick, who became one of the world's most wanted hackers in the 1990s, has died at the age of 59 from...

Meet NoEscape, the return of the Avaddon RaaS gang
With NoEscape, the ransomware gang Avaddon, which has claimed victims in the past, appears to be returning. S...
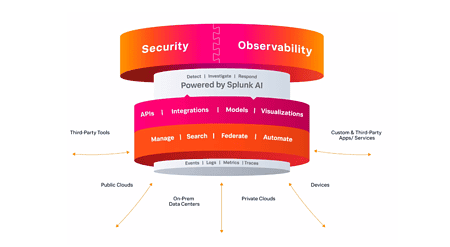
Splunk integrates security and observability with Splunk AI
Splunk has unveiled Splunk AI at .conf23 in Las Vegas, which Techzine is attending. In addition to launching ...

Dutch entrepreneur discovers potentially dangerous typo in mail addresses
A Dutch internet entrepreneur who manages the .ml domain extension for the Malian government has discovered t...

Partnership with Microsoft brings Splunk to Azure Marketplace
During its first keynote at .conf23 in Las Vegas, Splunk announced that it has formed a strategic partnership...

Splunk aims to simplify OT security with Edge Hub hardware
At its own .conf23 event in Las Vegas, Splunk has announced a new OT product. The Splunk Edge Hub can streaml...

LockBit and Clop responsible for about 40% of ransomware attacks
The ransomware gangs LockBit and Clop executed the most ransomware attacks in the month of June this year. Th...