
Wiz sees big impact of AI on runtime security, but also stresses old threats
Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...

Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

On the issue of the recent attacks on US federal agencies, president-elect Joe Biden has promised tougher res...

Headlined by Microsoft and McAfee, a group of 19 security firms, non-profits, and tech companies announced pl...
Within enterprises, thousands of endpoints often are active at once. Many times, these devices are not identi...

EU agency also issues its own report highlighting threats from 5G. Global cybersecurity firm Positive Tech...

IBM Trusteer researchers have uncovered an extensive fraud operation unlike anything anyone has ever seen bef...

The password system we use today pre-dates the Internet. Fernando Corbato is the American computer scient...

Researchers say that around 3 million people worldwide have been affected. Threat Intelligence researchers...

Python-based malware family targets Microsoft users to steal Outlook processes and browser credentials. Th...
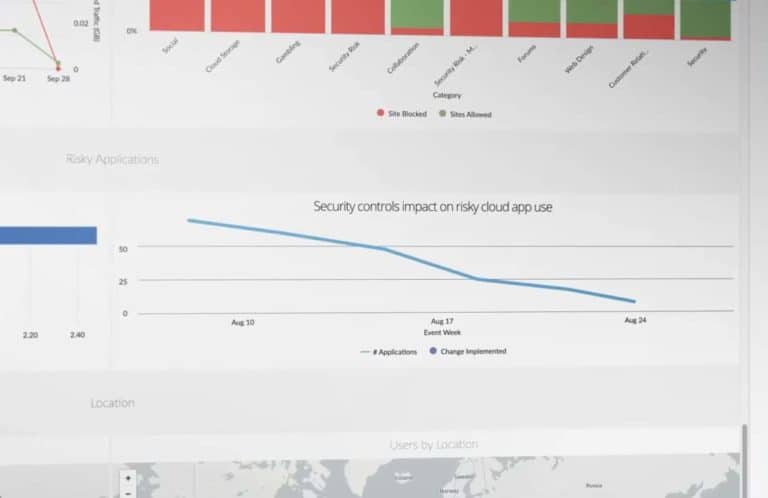
How do you achieve the desired level of security with the right tools? Many security vendors are currently lo...

Forecast indicates that remote and cloud-based systems will be aggressively targeted in the coming year Tr...