Everything there is to find on tag: vulnerabilities.

Printing feature in Linux vulnerable to RCE attack
The open-source CUPS printing system in Linux is vulnerable to remote code execution (RCE), which allows hack...
Everything there is to find on tag: vulnerabilities.

The open-source CUPS printing system in Linux is vulnerable to remote code execution (RCE), which allows hack...


A critical authentication vulnerability allows hackers to remotely invade and completely abuse the SAP Busine...

Microsoft's August Patch Tuesday update fixed 89 vulnerabilities. Among them were ten zero-day vulnerabilitie...

According to research by Atropos.ai, six companies have escaped paying ransom for a ransomware attack because...

Figures from Zscaler show that in the past year, 56 per cent of organizations were targeted by attacks that e...

Thousands of iOS and macOS apps have been vulnerable to hacking attacks for a decade. Although no attacks hav...

According to security researchers, the risk of users downloading a malicious browser extension from the Chrom...

VMware by Broadcom has disclosed two critical vulnerabilities in vCenter Server, a key component for managing...
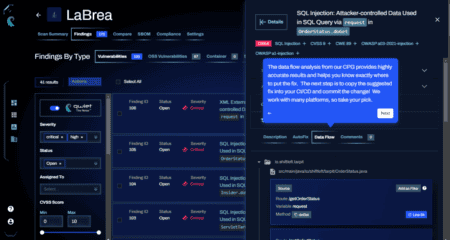
Developers working with the Qwiet AI platform will soon receive suggestions for improvement when the AI finds...