Thousands of iOS and macOS apps have been vulnerable to hacking attacks for a decade. Although no attacks have been spotted, vulnerabilities in a ‘trunk server’ meant to manage the CocoaPods repository would have enabled supply-chain attacks.
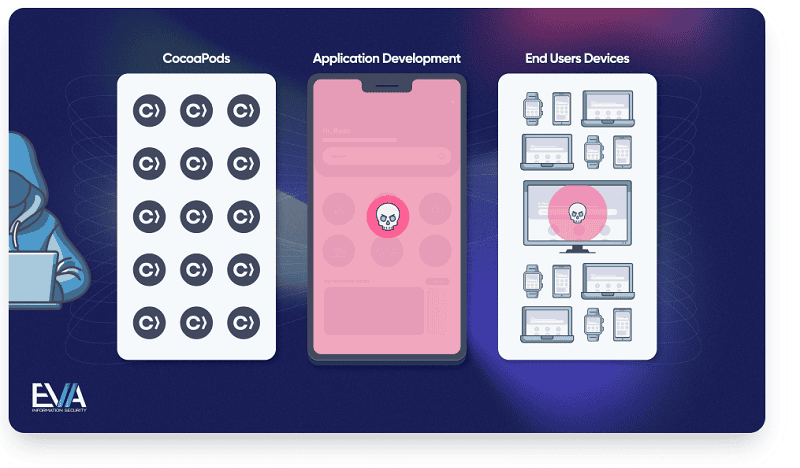
Late last year, researchers from security specialist EVA Information Security discovered three vulnerabilities in a so-called ‘trunk server’ of the CocoaPods repository, intended for open-source Swift and Objective-C projects for iOS and macOS apps. These vulnerabilities allowed hackers to add malicious code to apps.
Through CocoaPods, developers can change individual code packages called pods. These changes are then automatically added via app updates that depend on this code. This requires no action from end users. CocoaPods provides some 100,000 libraries, which are used by more than 3 million apps.
By adding their malicious code, hackers could potentially gain access to confidential data such as credit card information, medical information, and other private matters. This, in turn, could lead to ransomware attacks, fraud, extortion, or corporate espionage.
Three vulnerabilities
According to the security specialists, the cause of the three vulnerabilities that they found, lies in an insecure email authentication mechanism. This mechanism is used to authenticate individual ‘pods’ and developers. In this process, the developer provides their e-mail address for his pod, after which the affected trunk server replies with a link to the address. The developer gains access to the pod when the link is clicked.
The first vulnerability found, CVE-2024-38367, allows manipulation of the link so that it points to a server under the control of hackers. This happens through a so-called ‘spoofed XFH’ or HTTP header to identify the target host.
The vulnerability is specifically in the session_controller class of the trunk server source code that handles the validation URL.
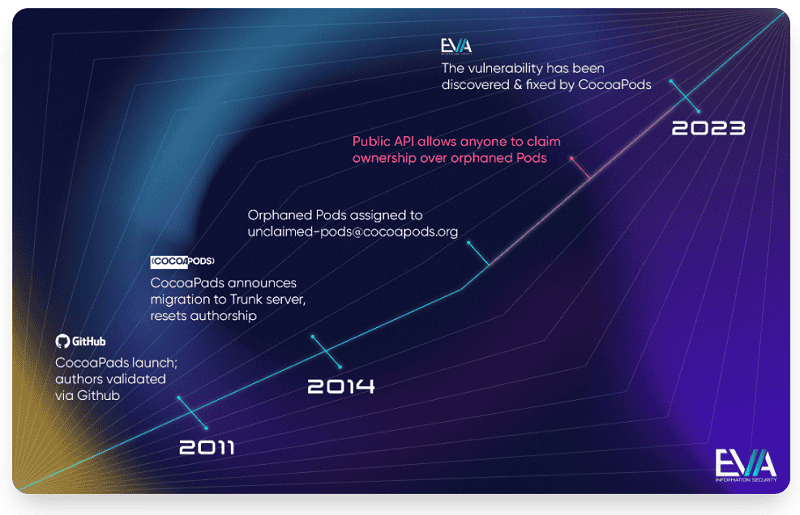
The second vulnerability, CVE-2024-38368, allows hackers to take control of pods that developers no longer maintain but that apps still use. Through a programming interface, developers can still claim pods that have remained active 10 years after their initial deployment. When hackers find this interface and gain access to the ‘orphaned’ pods, they can take over these pods without authorization. A migration in 2014 left thousands of such pods behind.
The third and final vulnerability found, CVE-2024-38366, allows hackers to run arbitrary (malicious) code on the trunk server. This includes modifying a required ‘MX record’ with malicious code.
Session keys removed
The CocoaPods vulnerabilities remained undiscovered for 10 years and only came to light in October 2023. The developers patched them and although they have not yet spotted any attacks, they make no guarantees either. They confirmed that EVA Information Security’s scenarios are realistic.
After the vulnerabilities were discovered, the CocoaPods team removed all session keys, as they may have been stolen. They also implemented new processes to recover orphaned pods.
The EVA Information Security researchers also provide developers with tips on addressing the various vulnerabilities. You can read more about these methods here.
Also read: Apple releases iOS updates for two exploited zero-day vulnerabilities