Cisco has been developing Intent-Based Networking since 2014. The technology started in the data center and has also been available for Campus networks since 2017. The new technology is so different that it needs time to roll it out completely. Every year, new steps are taken in the development, migration and adoption of the technology. Ultimately, it is only a matter of time before Intent-Based Networking becomes successful, as it is a complete re-vamp of how we build networks. Hardware is no longer leading; everything is software-defined. From the campus to the data center to the cloud.
Cisco started Intent-Based Networking in 2014, but two years ago, the biggest step was taken. Then the concept of Intent-Based Networking was presented for Campus networks. It is Cisco’s way of software-defined networking (SDN), something that more companies are working on today.
The idea behind it is that users can travel freely through the network, through a campus network, to the data center and even to the cloud. This is regardless of whether the user uses a network cable or is wirelessly connected to the company network with his or her laptop or smartphone. The user is identified, and the endpoint is confronted with a policy that applies to the entire network. The way in which enterprise networks are managed and built has been completely overhauled. We no longer talk about VLANs with user groups, but about policies per client. During Cisco Live this year, the announcements were much smaller. There are a lot of small new features that were discussed in the sessions, but if we look at the big news, it is mainly in more network automation, more analytics and a review of Cisco’s training program.
The steps that Cisco has taken in recent years have focused on DNA Center (Network Management and Automation service), among other things. In most cases, DNA Center already knows what is expected. The network recognizes the device and the software then configures it. Previously, you first had to add devices manually via the console. Nowadays you can simply connect new switches and access points in the network, and they will appear automatically in DNA Center. This saves a lot of manual actions and possible configurative errors.
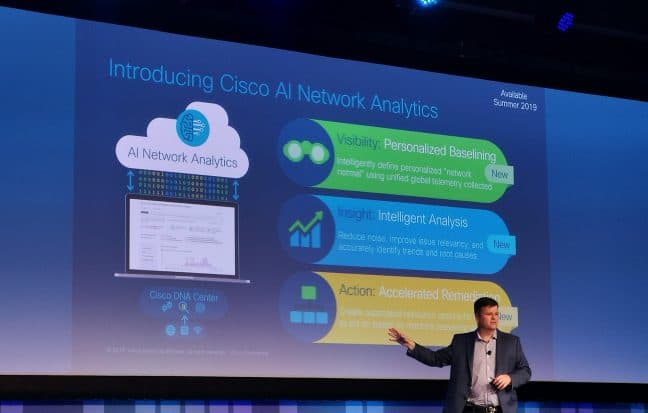
Cisco not only uses analytics in DNA Center, but with the help of AI, it can now also detect deviations and therefore give very specific advice. This takes a lot of work off your hands, especially for troubleshooting, so that errors can be repaired faster and with less work.

The role of the network admin is changing, and so are the training courses
Where a network admin used to have weeks to build a network, nowadays everything has to be done almost immediately. Configuring each switch separately and stopping the rollout of new applications for weeks to months is no longer possible. That’s why everything is now software-defined, and Cisco tries to control and automate as much as possible centrally from the Cisco DNA Center. Cisco DNA Center is basically designed to control and configure Campus networks, but it is slowly gaining in importance with support for SD-WAN and SD-Branch. Cisco uses Application Centric Infrastructure (ACI) technology for the data center and the cloud, which is also based on Intent-Based Networking. Cisco DNA Center cannot manage ACI, but traffic can be segmented between the campus, the data center and the cloud.
The road to software-defined also means that network admins have to think and work differently. The Cisco training courses play an important role in guiding them in this direction. However, Cisco saw that with the advent of software-defined networking, there is a greater demand for scripting for customized solutions within the network. The Cisco Devnet community plays a major role in this, but it was separate from the network professionals. That is now a thing of the past. Both communities have been merged. It means that based on the need, one can now follow training courses from both camps. Someone can, therefore, specialize in certain network technology (campus, IoT), but at the same time also follow Devnet training courses in order to use or automate this better.
What is Intent-Based Networking?
For those readers who are less familiar with Cisco’s chosen path, it is good to reflect on what Intent-Based Networking (IBN) is again. With IBN, the network administrator has to indicate to the network what the intent (goal) of a certain action is or the path that needs to be taken. This is done on the basis of a policy with requirements, after which the network itself compiles the configuration and deploys it across the various network devices. It all happens in software-defined and segmented network blocks.
An example of this is that all users in a secondary office location (branch office) must be able to connect to the payroll application that runs on a server at the head office. To make this possible, the campus network has to be configured in such a way that there is a policy via SD-Access in which the user can make such a connection. Also, SD-Wan will be configured because the connection between the two offices is running.
This is a relatively simple example. It can also become a lot more complex, for example in applications that require low latency. Network traffic should then be given priority, or be directed across travel routes that have faster connections. In addition, security is extremely important, and that is where network segmentation comes into play. For example, this could take place in a factory, where all machines with an IoT solution have to connect to an application that manages and monitors. A private network segment can be set up for this purpose, which other users of the network cannot access.
In the end, when the target is set, the network automatically unrolls the complete configuration across all devices, whether this means access points, switches, firewalls or routers. Nor does it matter whether the network consists of multiple domains. Cisco has developed two different technology standards: Cisco DNA for campus networks (access points, switches, firewalls, SD-WAN) and Cisco ACI for data centers and cloud. The management of the intent-based policies is done via ACI and DNA Controller, which can handle both technologies.
Easier and faster network management
It will eventually lead to simpler and faster network management because the complete configuration is done from a central control panel. Cisco DNA Center is the control panel that stands above all on the Campus, for the data center it is ACI. All Cisco equipment is configured centrally. The configurations are distributed by means of APIs. If desired, companies can also communicate with the API of the controllers. ACI or DNA Center in turn talks to the network equipment if changes are needed.
In the past, companies still too often had to configure the network devices separately from each other. In addition, there was one large configuration, not segmentation and building blocks as is now the case with an SDN.
Because Cisco now extends the Intent-Based Network across all layers of the network, it is possible to control everything centrally. It really is a completely new generation of networks. Because everything is software-defined, the monitoring is also centrally controlled. This also creates new possibilities.
Knowledge base, monitoring and AI offer the possibility of automation
Over the years, Cisco has built up an enormous database of knowledge. Thanks to the training program, and all certified Cisco professionals, a lot of known problems have been tackled and recorded in a knowledge base. Whether it’s a wrong configuration, or the wrong positioning of access points, not being able to reach a DHCP server, a DHCP pool that is empty, a band that is disturbed too much by other masts, in fact everything that comes with rolling out a network.
By putting all these problems and solutions into a knowledge base and applying machine learning and AI to it, Cisco is increasingly capable of solving problems through automation. Cisco is now able to diagnose more than 300 known problems itself. At the moment, many network administrators still prefer to diagnose problems themselves and then give advice, so that the administrator can solve them themselves, but through automation, Cisco’s software-defined network can also solve them directly itself. That is ultimately the future.
In addition, Cisco invests in the continuous monitoring of the network and in the use of analytics. This enables Cisco to detect problems more quickly. An example that Cisco gave during Cisco Live was of an application and group of users that make approximately the same movement in terms of network traffic every day. The network traffic increases significantly around 8:00 in the morning, rises to 10:00, 10:30, and then the line starts to decrease again. If Cisco then detects on any day that the traffic around 10:00 is far below the norm of the usual situation, it can sound the alarm. However, it can also use machine reasoning, as Cisco calls it.
In addition, the system is going to do a little more research. It has already established that there is much less activity. Is this because, for example, it is Sunday and the company is closed? Or are there far fewer clients active in the user group of this application? For example, it can detect that a certain access point in a department is not functioning properly so that users cannot reach the application. Normally you would think that the application or the hardware on which the application runs is not working properly. In reality, the access point of a department is the problem.
With machine reasoning, a solution can then be rolled out automatically on the basis of the policy, or a solution can be offered to the administrator. The administrator can then implement the configuration change with a single click. If there is a problem with more than one access point, then it is recommended that this change be implemented in all access points. Again with one click. This solution can also come from the AI technology that has been applied to the knowledge base. All in all, it is a combination of various new technologies.
Wi-fi is problem number one
We understand from Cisco that for many customers at the moment wifi is the biggest problem. Many companies are on their way to the cloud, with more and more on-premise solutions disappearing and being replaced by cloud services. For example, companies are switching to Office 365, Box and other cloud services. This is not very complex in principle, and often a test with a small group of users goes very well. However, if 5000 employees suddenly start using all kinds of cloud services actively via wifi, the network and the required bandwidth must be suitable for this. It is a fact that if a company starts to use more online services, employees will also generate much more data traffic because many cloud services work together or are linked to each other. The use of media is often also increasing.
It is therefore important to tackle problems with a Wi-Fi network quickly. By applying AI, these problems can be quickly identified, and problems can be solved. In case of a persistent problem, it is even possible to travel along to detect problems. Cisco also cooperates with Apple, which makes it possible to watch from the client’s side and thus to solve the problems more effectively.
Cisco networks are self-learning or can be trained using a workbook
As soon as problems are detected, and an administrator provides the solution, the network will learn to apply the solution itself in the future. There is also an alternative method in case the situation is so complex that a complete script needs to be executed with several actions to solve a problem. Network administrators can create a workflow, or what Cisco calls a Workbook. This can be used to define all the steps and scripts that need to be performed for a particular event. This allows the administrator to add a piece of network automation himself.
Cisco Application Centric Infrastructure also to the cloud
As mentioned earlier, Cisco Application Centric Infrastructure is based on Intent-Based Networking as well, but until recently it focused solely on data centers. Now Cisco has started to add Azure and AWS. As a result, certain native cloud services can also be controlled from Cisco Application Centric Infrastructure, and the policy that has been established can be extended to the cloud. For example, when it comes to SLAs and compliance. As a result, applications can easily move to a cloud environment in the event of peak loads or malfunctions. As a result, applications that need to be available at all times can continue to run.
The major advantage of this cloud support is that everything still works from a single control panel. Cisco is linked to AWS and Azure and uses the cloud-native APIs to configure the cloud. When it comes to networking, things work a bit differently in the cloud. Cisco has decided to support the cloud-native APIs and not build its own network on top of the cloud provider’s virtual network, as this has a negative impact on performance. However, this type of cloud support is still fairly new to Cisco. We will undoubtedly hear more about this in the near future.
On paper it’s all good, in practice there’s still work to be done
In order to put everything into perspective, it is always good to have a chat with some partners with these kinds of new technologies. That’s what we did. In general, they are positive about the path we have taken. They really believe that SDN has the future and that the IBN story will bear fruit.
What some partners also say is that rolling out such a network and, for example, setting up Cisco ACI or Cisco DNA is not always as easy as Cisco makes it happen. If you want to roll this out to an existing enterprise environment, you are actually going to replace the entire network, unless you are using Cisco hardware from the last few years. This process has already become more efficient in recent years, but there are still a number of challenges.
This is especially true for enterprise organizations that have no idea which applications the company is using, which applications run where, which user groups there are or should be. There are still many poorly documented and cluttered networks. Few enterprise organizations have properly documented this or really have a good overall view of their network. It takes a lot of time to find out. We asked for a response from Cisco. The company acknowledged that this is often poorly documented, but that partners with the DNA and ACI monitoring functionalities can map out the applications and endpoints.
Some partners were also of the opinion that Cisco is still a long way from recognizing everything. For example, companies have industrial machines that are not recognized, but that need to be connected. Cisco informs us that it is getting better and better at recognizing devices, but that there are still a lot of legacy devices. Every network supplier has this problem. The more devices that are connected, the better the recognition will be.

If we have to summarize what partners would like, it is an even faster way to roll out an intent-based network. They are not satisfied with the total time it takes to build an intent-based network. We have discussed this with Cisco, and they mainly point out that a lot of time has been saved in recent years, but that there is always room for improvement.
For companies that start with Intent-Based Networking, it’s also good to keep an eye on the benefits when it’s up and running. In contrast to a perhaps somewhat challenging implementation process, the advantage is that the cost savings only really start. If something new needs to be added to the network, it can be done in 10 minutes, while it would take a few hours. Furthermore, in the coming years, more and more will be done through automation, which will save a lot of management hours. Finally, thanks to SDN, the policies and segmentation, the network is much safer and clearer.
The cloud is central to Cisco’s strategy
We also had quite a few conversations about Cisco about the cloud. We talked to Vijoy Pandey, who is responsible for the cloud and software strategy. He said that a few years ago, enterprises all focused on a single cloud environment, while now they all talk about hybrid and multi-cloud. The experience and use of the cloud have changed. Also, according to Pandey, you shouldn’t want to do a lift and shift from on-premise to the cloud. You need to make effective use of the possibilities that the cloud has to offer and on top of that build cloud-native applications.
What he wanted to say was that Cisco’s focus is more on supporting cloud-native networks and instances, combined with an on-premise campus and data center environment. Something the company recently started.
For example, it is already possible to roll out a Cisco firewall virtually in the cloud, which a customer can do himself, but also by ordering a Cisco firewall via the AWS or Azure Marketplace in addition to the physical firewalls that the customer already has running in his own environment. Cisco Defense Orchestrator ensures consistent security policies across all these security appliances.
The policy that is implemented on-premise can be extended to a private cloud environment in AWS or Azure, where, for example, various applications are running.
Security is at the heart of Cisco Networking
Cisco’s security department is a bit of a poor child when it comes to talking about Cisco. This is partly due to financial results. Cisco Security is doing very well, but in relation to the network department it is only a small part of the result. The fact is, however, that without all the security solutions, the network products wouldn’t be as good, or would sell as well.
Solutions like Stealwatch and Tetration are very important to Cisco. Tetration is good at mapping applications in a network, while Stealwatch focuses more on IP traffic, metadata and host behaviour. For example, if an endpoint is detected as a printer, but its behaviour differs because it connects to the ERP and CRM servers, then the intent can be verified on the network and can be excluded from the network.
Finally, Cisco Talos plays a major role in all of Cisco’s solutions. The network products and security solutions are linked to Talos. According to Cisco, Talos is the largest security database in the world. A huge amount of data is brought together in this database and intelligence is collected from it, which is used to bring security to a higher level. Thanks to Talos, Cisco can, for example, also recognise undesirable behaviour in encrypted network traffic.
Companies that use Cisco solutions have the choice of actively linking them to Talos, something that Cisco does recommend. This makes it possible to share a large amount of log information with Cisco, which in turn brings the necessary benefits.
Cloud services use Talos as standard, and on-premise customers can choose if and when they want to use Talos.
Are we affected?
If, for example, there is a major outbreak or security risk, the management often asks the following question: do we suffer from this? Has anything to do with this been identified on our network? Think of the WannaCry-ransomware, for example. With Cisco Treathresponse, customers can do their own research to see if they are affected. This is also what Cisco Talos is behind.
This strong security proposition helps Cisco to differentiate itself from other network suppliers. It is a strong sales argument to choose Cisco. In the coming years, Cisco will undoubtedly continue to work on its Intent-Based Networking products and their integration, including the combination with the security solutions.
Tip: read our report on how Cisco is branching out with Webex, taking on Microsoft Teams and Slack
