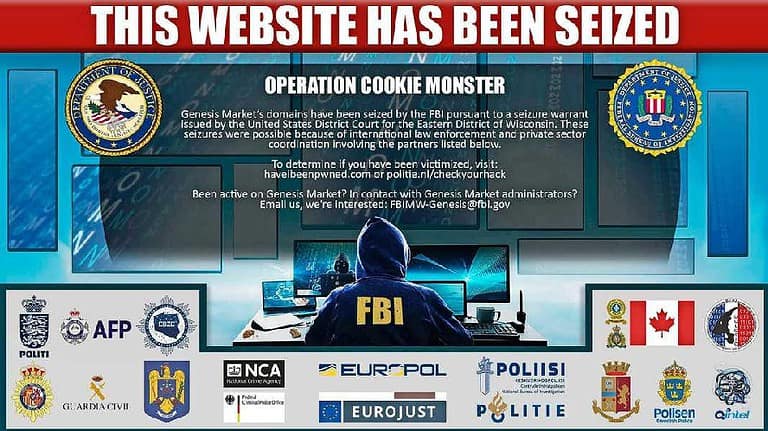
The cybercrime world will have to endure without Genesis Market, now that it has been taken down by authorities on April 4. Criminals were able to sell countless sets of data from unsuspecting victims on the platform. What makes the fall of Genesis Market significant in a world full of cybercrime?
In order to understand why the demise of this website matters, let’s look at exactly what Genesis Market was all about. Since 2018, it was offering so-called ‘bots’. In this context, a bot refers to a single victim’s cookie data along with their digital fingerprint. Online services normally use this data to verify that a user can be trusted. As a result, the malware on which the Genesis service depended allowed a criminal to use a victim’s data to illicitly enter services, rob bank accounts and perform other malicious acts. The large amount of data available about a given victim made it possible to bypass MFA (multi-factor authentication).
Impersonation-as-a-service
Genesis Market was the world’s largest IAB, or initial access broker. Unlike many other cybercrime initiatives, the business model was not to scam people directly, but to enable others to do so by trading data about infected users. Anyone interested in a bot complete with a whole portfolio of login data often had to pay hundreds of euros’ worth of bitcoin for access. In return, a victim’s cookie data would be updated on a persistent basis due to the malware still running on the PC in question.
The commitment to quality went a long way with Genesis, according to research work by cybersecurity firm Sophos. It featured a user-friendly interface, customer service, extensive search functions and tools allowing for targeted attacks. A leap beyond the rather random data dumps shared on underground forums of old, then. Just as big tech companies offer an ever-changing SaaS (Software-as-a-Service), a consumer of Genesis could count on its well-maintained IMPaaS (Impersonation-as-a-Service). Not the first time such a business term has gained traction in the digital underworld, as this example from a few years ago illustrates.
Tip: Why cybercriminals are using forums and the dark web on a large scale
Invite-only
Genesis Market’s business model seemed to be very successful, even though the service was invite-only. There was therefore a very active secondary market around providing access to the Web site, not entirely unlike the reselling of tickets to a popular music festival.
Ransomware groups were among the most interested in Genesis’ services. The ease of use and the format of available data allowed them to attack specific companies by targeting them through multiple infected users. Individual victims were not spared either, sometimes resulting in large financial losses.
Two groups of criminals can be distinguished in this instance. On the one hand: Genesis Market itself, which sold the bots, and the customers on the other, who in turn went on to commit crimes using the stolen data. A sophisticated crime network that was able to persist for half a decade, then. How did the FBI and police finally stop these practices?
Operation Cookie Monster
In 2019, Europol became involved in the ongoing Genesis Market investigation. Based in the Europol headquarters in The Hague, an international team organized a global investigation into the illicit affairs of Genesis associates. In cooperation with cybersecurity experts from the U.S. company Trellix and Dutch-based Computest, the team were able to trace the malware behind Genesis’ data collections. The browser that Genesis customers used was also analyzed in detail to pinpoint the perpetrators. The goal was to unravel exactly how victims were attacked and where the data ended up going to. The data showed that at least 1.5 million bots were available on the Genesis storefront.
Once the research team ensured the malware was detectable, bots were found to be located primarily in North and South America, Europe and Southeast Asia. Computest describes an example of an attack that ironically occurred because the victim thought he had found an illegal activation of an antivirus service. However, the setup.exe uninstalled the antivirus in question and installed the malware. The malware then proceeded to impersonate a Google Drive plugin in the browser. This allowed Genesis customers to access a victim’s browser data.
The data that Genesis provided to other cybercriminals aided in the investigation. 119 suspects were arrested in 13 different countries on April 4. This happened as authorities took down the Genesis website, which now displays an image from the FBI. How does the cybercrime landscape change with these arrests?
Big fish
All indications are that Genesis Market is a highly important catch in the fight against cybercrime. It was the biggest fish in the bot-sellers ocean. In particular, its ease of use allowed malicious actors to commit crimes. Thus, those who depended on Genesis’ functionality will now have to do without all of Genesis’ tricks and features. The professionalization of cybercrime is enhanced by this form of specialization. Genesis collects the data before others make use of it to loot bank accounts or perform other illegal activities.
According to cyber expert Roman Faithfull, however, we should not underestimate how many cybercrime enablers are still on the prowl. Genesis was the largest website of its kind, but has been struggling with technical problems in recent months. As a result, some customers have already switched to alternatives, which are still active.
In short, cybercriminals will always look for new accomplices. Still, it will take quite a bit of time and effort for many of them to continue their work undetected. Whoever takes Genesis Market’s place at the top will soon appear in the sights of police and cybersecurity experts.
Also read: ‘Encrypted cyberattacks increase by 20 percent’