OpenText Cybersecurity research on code security shows that organizations are only just beginning to adapt their security strategies to change. Meanwhile, the software development life cycle (SDLC) is becoming more complex and the number of threats is increasing. It raises the question of whether your organization is paying enough attention to AppSec to prevent vulnerabilities.
We decide to take a closer look at the above issues as a result of OpenText Cybersecurity’s research. With Fortify, OpenText Cybersecurity has a platform that helps build secure code. To really get some more insight into the state of application security within organizations, OpenText had research conducted by Dark Reading. This involved surveying cybersecurity professionals and application developers from organizations of various sizes (up to 500 employees, up to 5,000 employees and over 5,000 employees).
The idea is that the survey should come up with the key influencing factors for tool adoption. It should also identify key implementation challenges. To get some immediate insight into these, we share the table below from the survey. Important to note here is that the data comes from November and December last year, when the question was posed to professionals.
Implementation of DevSecOps not running smoothly everywhere
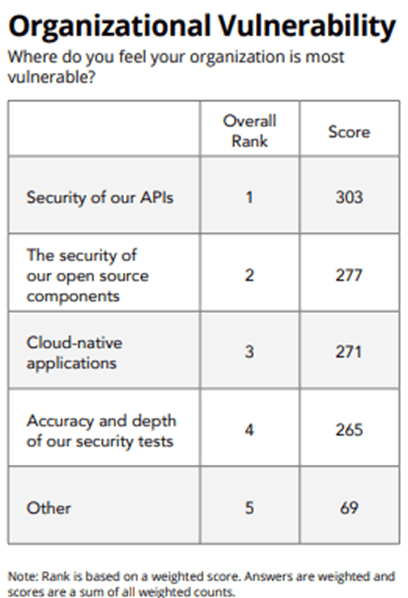
What OpenText Cybersecurity notes broadly in this regard is that organizations in general still have a long way to go until their application security is truly mature. This is no match for the changes and their needs, if we look at the survey that way, and that makes for vulnerable software. OpenText Cybersecurity cites several causes for the increase in threats: increased cloud adoption, APIs as popular targets of cybercriminals and vulnerable software due to the use of open-source components. Some of these causes deserve some additional attention, which we will give in the course of this article.
What OpenText Cybersecurity notes is that many organizations find themselves still at the starting point of incorporating dynamic analysis tools (such as DAST) into the test cycle. What is also often at an early stage is moving testing activities to a much earlier point in the SDLC. This is interesting because as a result, vulnerabilities are often not actually discovered until later in the development process or when the software is already in production. In the latter case, a hacker might take advantage of the vulnerability and find its way to do damage.
Of course, there are differences when it comes to company sizes and maturity levels. However, according to OpenText Cybersecurity, there is no question that shift-left is the way forward so that security protocols are implemented early in the SDLC. This aspect is often hot within organizations implementing DevSecOps. Such organizations bring developers and security experts together to create a collaborative approach and maintain the development pace.
According to survey data, a majority (57 percent) are implementing DevSecOps. At the same time, one in three companies have not yet done so, but plan to do so this year. Finally, 14 percent have no plans to implement DevSecOps at all. This shows, as far as OpenText Cybersecurity is concerned, that many organizations are still at the beginning of AppSec maturity.
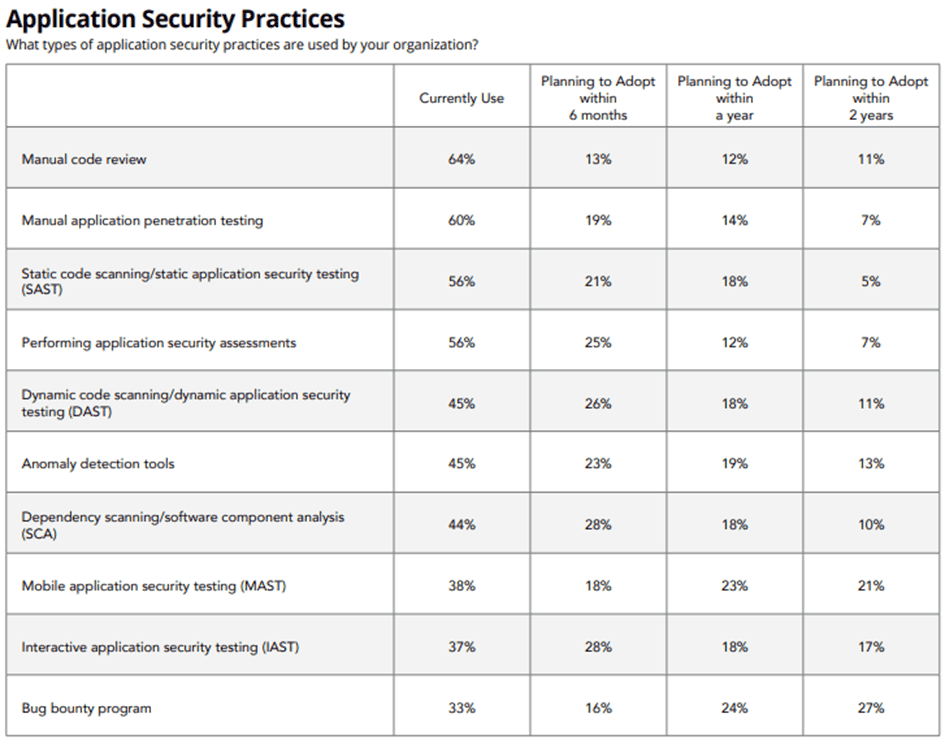
The survey bears out that many organizations may still be too dependent on manual processes, which can hinder good AppSec. As you can see in the table above, nearly two-thirds of professionals manually review code, while six in 10 professionals manually pentest applications.
Ambitions around shift-left
What is good to see, however, is that most companies are making plans around shift-left and implementing security testing at an earlier time is the SDLC. 81 percent of companies are currently setting up application security assessments or plan to do it in the near future. At the same time, the data suggest that organizations that are already somewhat at a further point of maturity may still be lagging behind when it comes to using advanced tools for multiple points in the lifecycle.
Still, organizations struggle with vulnerabilities that come with open-source components. Just over half of organizations use the SAST testing method. That is, most companies probably test source code early in the development process for a range of known vulnerabilities. It again shows that most security teams are well on their way with shift-left.
However, it remains a given, the survey notes, that open-source components are seen as the second most vulnerable area (see table below). In that context, it is worth noting that a good portion use or intend to use the SCA analysis method. This method allows analysis and tracking of dependencies, including open-source components. “It’s likely that high-profile attacks, such as Log4j, have prompted teams to make plans and manage their open-source components appropriately,” the report outlines.
API security top concern
As the above list shows, however, companies feel most vulnerable due to the issue of securing their APIs. This is explainable by the vast application landscapes that companies have built, combined with the desire to have those applications communicate with each other. This is done through the APIs. Today, however, APIs are a popular target of hackers. In fact, the study cites predictions that API-related breaches accounted for some 21.5 billion euros in losses in 2022.
Smaller companies in particular are very concerned about API security, according to the survey data. According to OpenText Cybersecurity, there may be too little knowledge on the subject. Another possible cause is that the to-do list of security has other priorities.
Half of larger companies actually use a tool for API security testing. Among smaller organizations, the percentage is 31. Four in 10 smaller companies want to treat APIs the same as Web applications. 18 percent of smaller companies do not test APIs for security, versus 3 percent of larger companies.
In conclusion, as far as OpenText Cybersecurity is concerned, organizations would be wise to carefully consider the combination with dynamic tools in their approach from now on. This leads to shift-everywhere, realizing the continuous security cycle.
Should you want to know more about the study, you can download the document via this link. In it, OpenText Cybersecurity discusses even more results and best practices. For example, it also discusses the role of a partner in shift-everywhere, a concept that goes beyond shift-left. This is where OpenText Cybersecurity wants to play a role, especially since it was named a leader in Application Security Testing in the recent Magic Quadrant by analyst firm Gartner for the tenth year in a row.
Also read: Zero trust in complex environments: how to ensure secure access to apps?