Many companies have seen their infrastructure and application landscape become more complex. This, in turn, creates new challenges. After all, how do you properly set up identity and access management? The basic zero trust component is essential for authentication and access to protect users, apps and sensitive data.
We talked about securing security with Sales Engineer IAM Michiel Pouw of OpenText Cybersecurity. According to Pouw, many companies struggle with securing access to apps in complex environments. He sees that they do think about it and invest in it. They use a variety of tools to manage users and access. It indicates that companies are looking for the right approach.
The zero trust approach is seen as a way to do work more securely. The rise of applications in the cloud and a lot of remote working are some of the reasons for embracing such an approach. A fixed location is no longer always the case. This needs to be considered so that security, users and access are set up according to the “never trust, always verify” idea.
Getting the basics right
So zero trust looks at who is trying to access a resource. This requires a primary focus on identities. If identities are to be the starting point for security strategy, a number of technologies are crucial. Thus, zero trust often consists of multi-factor authentication (MFA) and privileged access management. Microsegmentation, which splits the environment into smaller zones, also falls under zero trust. That way, access remains limited to that smaller zone even if a hacker somehow manages to get in.
The MFA component of zero trust forces a user to use at least two authentication factors. It makes it harder for cybercriminals to gain access to apps and environments. Authentication factors can be something you know (like a password), what you have (like a smartphone) or what you are (like a fingerprint). Furthermore, zero trust relies on the least privilege principle. It means that a user only gets access to the apps and data he actually needs for his work, optionally within a certain time or with additional security controls.
Many solutions
What Pouw sees during conversations with organizations is that they are enthusiastic about the zero trust idea and are trying to properly regulate access and users. They embrace one or more IAM point solutions to address the needs. Often these little islands within the IAM strategy are very good at what they need to do. A kind of best-of-breed approach has emerged where solutions have very specific features.
“We see more and more organizations using IAM components from different vendors,” Pouw said. According to Pouw, however, it leads to many different solutions within an IAM approach. As a result, the overall approach does not function properly. The solutions sometimes cannot work well together, even though they have a lot in common and can do a lot for each other. Moreover, many solutions can lead to certain solutions being barely used or inadequately managed, causing configurations to become insecure or risks to grow because updates are not implemented. For example, organizations face undercapacity or people forget to use one of the many solutions.
Pouw also sees that the many point solutions lead to support chaos among the various vendors. For example, you have to deal with different contacts and contracts from the vendors. It can also be unclear where an IAM problem, if it occurs, comes from. Finding the solution in that case can be tricky, as multiple platforms must be investigated.
Considering options
Basically, according to Pouw, you have to look at setting up the three components of identity management, access management and privileged management. If you want to set those things up properly, it’s important to know your landscape. If you have already invested significantly in various solutions, it is wise to continue using those existing investments. You can then add a platform that acts as the underlying technology. Such a platform makes use of open interfaces and standards to allow the solutions to integrate well with each other. From this platform you can then control most things.
Another option is a landscape in which few to no IAM point solutions are yet available. In that case, you can embrace a platform that covers all three components as part of a best-of-breed approach. In theory, a company then may not always have the most comprehensive functionality as point solutions offer, but in meeting its needs, it can offer many advantages. For example, everything instantly works much better together, making your organization able to prevent an attack.
Also read: OpenText reports Q2 results after buying Micro Focus
Adding dynamics to access
Pouw sees that companies with a firm focus on zero trust and IAM are becoming much more resilient. At the same time, the need for adaptive access is also growing among these companies. Pouw says that many companies are now still configuring which authentication method is needed for access on a per-application basis for each user. If a known device then gets into the wrong hands or its behavior changes, the static control mechanisms would be maintained. New threats would not be seen. Adaptive access aims to change that.
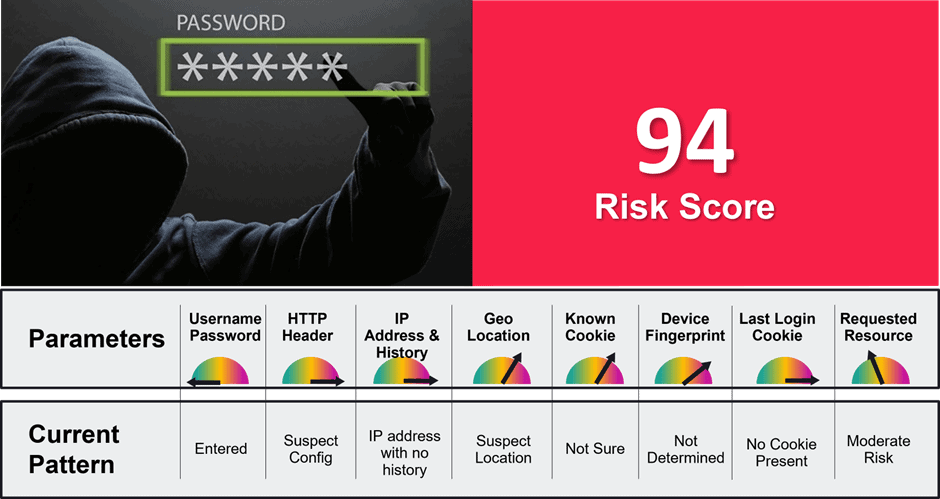
To do so, adaptive access applies a risk engine. It continuously assesses access to see if the risk level changes since the session started. In the picture below, you can see what parameters such a risk engine takes into account. If new risks are found, a user will have to perform additional authentication to access apps and data.
Towards zero trust
Pouw also revisits the segmentation component of a zero trust architecture, in conjunction with all IAM components. “With zero trust, you have to look at how you segment and classify different security components. You make sure that the least privileged principle is maintained, so that people only get access when they really need it. And how long do they need that access? What authentication methods are best for that? Don’t users have too much access? And how do you then ensure that management is securely set up for the entire environment? If you do all that with separate solutions that don’t work together enough, zero trust becomes difficult.”
Although we’re talking Pouw specifically about IAM in this case, it’s inevitable to talk about your entire cyber resilience approach as well. “You can link IAM to other OpenText Cybersecurity products for an even stronger zero trust approach. There are solutions that go much more into the data security and encryption piece. And there are solutions for application security, that is, making and developing applications more secure. There’s also the Security Operations piece that provides monitoring of entire environments, so you have real-time visibility into what’s going on. And of course that piece adaptive in zero trust, that you can also use machine learning to detect the anomalies that you can’t detect with normal monitoring. We can see a lot and know a lot, but machine learning helps us recognize the things we don’t see as quickly as possible.”
Ultimately, OpenText Cybersecurity can play quite a role in companies’ IAM strategy. It sees it as its strength that it can offer a complete platform that includes more than 20 years of experience and development. According to Pouw, when organizations grow or the business case changes, they run into the limitations of their point solutions and knock on OpenText Cybersecurity’s door. “They come to us for the experience and identity and access management features we have. These include real-time provisioning, real-time governance and adaptive access. If you make all that work together, you take a big step in your IAM strategy,” Pouw concludes.
Want to know more about zero trust, identity governance or least privilege? OpenText Cybersecurity also offers on-demand webinars on various topics.