Many so-called ransomware attacks on OT environments are actually attacks on IT environments. Hence, Ric Derbyshire, Sr. Security Researcher, and Charl van der Walt, Head of Security Research, of Orange Cyberdefense set to work to scientifically devise and test a “real” cyber extortion attack on OT. Not only to use this to demonstrate that this is a substantially different type of attack, but also to advance the industry as a whole. We spoke to them at length recently at RSA Conference.
Ransomware has been the main topic of conversation in the security world for several years. The impact is felt in OT environments as well. According to Van der Walt, the manufacturing industry in particular is often impacted by what he does not want to call ransomware, by the way. He prefers to talk about cyber extortion. After all, the ransomware is not the criminal act, that is in fact the extortion after it: “Ransomware is a mechanism to achieve this.”
Anyway, back to the OT environments affected by this cyber extortion. According to Van der Walt, the manufacturing industry now accounts for 25 percent of the attacks on these environments. This is not because they are more often attacked, but simply because they are more often impacted. That implies that these environments are more vulnerable. Hence why we hear a lot about OT security these days. The general trend in reporting here is that we are on the eve of an OT apocalypse.
Attacks on OT environments soared, or did they?
Based on the figures cited by Van der Walt and Derbyshire in our conversation, it is not surprising in itself that OT security is seen as a huge problem. They collected 35 years of data from reported incidents, from 1988 through 2023. It shows that between 1988 and 2020, OT was almost never targeted. That changed completely in 2020. Since then, there has been a huge explosion in attacks. The emergence of RaaS (Ransomware-as-a-Service) in 2020 and double extortion will undoubtedly have contributed to this.
However, Van der Walt also noticed that this explosion in attacks was not carried out by the usual suspects: “They were carried out by cybercriminals, not state actors or hacktivists.” That’s not what you might expect. OT is primarily a target if you want to destroy or disable something. At least, that’s the common narrative. In practice, however, the situation is quite different, specifically in manufacturing.
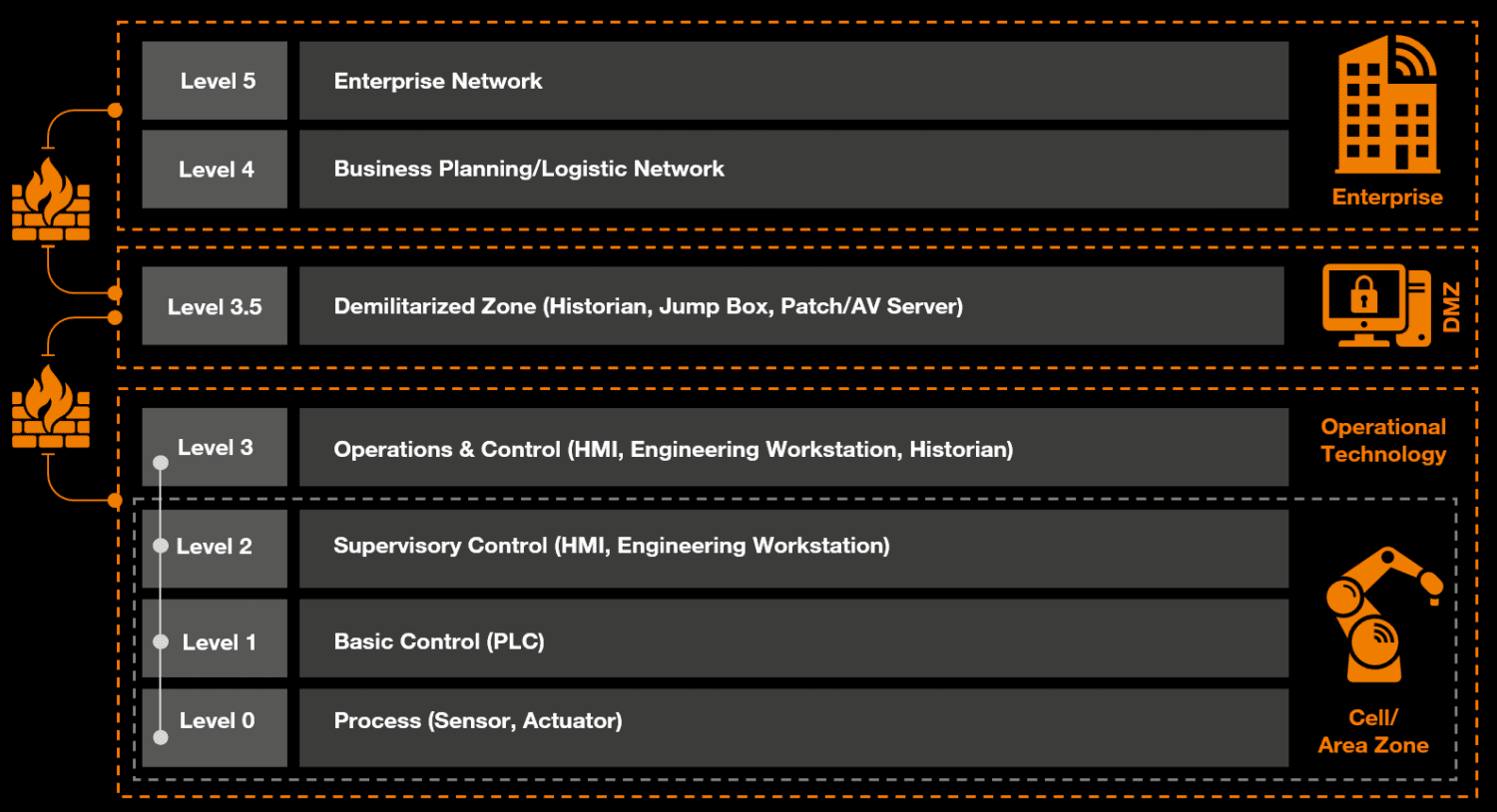
However, Van der Walt also sees something else: “The impact of the attacks is mainly in the higher layers of the Purdue model.” This model focuses on describing industrial systems. That’s because they (initially) don’t target OT at all, but IT. Those two environments are merging more and more, so there may be a degree of obfuscation. IT is a more interesting target for ransomware attacks and the extortion that comes with them anyway, Derbyshire points out. “IT has data, which is obviously very important for ransomware attacks.”
We’re not in the OT apocalypse
So you could say, based on the figures and findings above, that what most of what we call attacks on OT environments are really just attacks on IT environments that happen to be linked to OT environments. Cyber criminals have no interest at all in the typical objectives of an attack on OT. They don’t want to break things, but generally want to get paid for not leaking data.
The whole narrative surrounding attacks on OT environments is therefore quite exaggerated as far as Van der Walt is concerned. “We are not in the OT apocalypse,” in his words. This is important to know, he believes. “In fact, there is a narrative in the market that is out to get organizations to take action and invest.” In other words, we hear more and more that OT environments are under constant attack. At the end of the day, these are actually attacks on organizations’ IT environments. Everybody needs to be a little clearer about that.
This distinction is important to make, according to Van der Walt: “It’s important to be clear and precise.” Vendors in the security industry play an important role in this. “We don’t need vendors selling things no one needs,” he believes.
Real OT attacks and cyber extortion are possible
So most attacks that go in the books as attacks on OT environments are not, based on the numbers and insights gained by Van der Walt and Derbyshire. That does not mean, however, that such attacks are not possible. “There does exist a very frightening risk that attackers can take over the OT environment,” as Derbyshire puts it. To demonstrate that, he has set up an attack and published about it in scientific circles. This should result in a better understanding of a real OT ransomware attack.
In the attack Derbyshire devised and executed on real Siemens equipment, IT also plays a role, by the way. In his scenario, the attacker must first gain access to workstations that control PLCs in the OT environment. An important nuance, however, is that they are only needed to get into the OT environment, and do not play a role in the actual extortion following the attack. Once the attackers have control of the OT environment through the workstations, that control takes place in the background, within the OT environment. The authors describe that process in detail in the paper they published about it.
The idea behind the attack is that it makes extortion in an OT environment possible. That makes it interesting for criminals, because they can then ask for a ransom to return control of the OT environment. Of course, a company could also choose to just disconnect everything and replace all the PLCs, but that is probably even more costly economically, especially in larger environments.
In the attack devised by Derbyshire and Van der Walt, monitoring also plays a big role. It is about more than gaining control of the OT environment and determining when the extortionists can flip the switch. The attacked organization cannot do much to find out what is going on either. This is because the attacker/extortionist is constantly monitoring the environment. If a PLC misses even a single heartbeat, the attackers can take action and switch off everything. The attack did not get the name Dead Man’s PLC for nothing. It uses a dead man’s switch.
Below you can see how Dead Man’s PLC works. The numbered blocks are the Siemens PLCs. In the top left corner is the workstation that controls and monitors them. The orange lines indicate the interdependency of the PLCs and the workstation. The green lines indicate the heartbeats of the PLCs that attackers can register in this example of cyber extortion.
Chance of real OT attacks is small
OT attacks as we described above may be possible, but the chances of them actually happening are not high. Van der Walt and Derbyshire readily admit as much. “A lot of stars would have to align for this to happen,” in Van der Walt’s words.
The article and research are therefore primarily an academic exercise. It does not intend to reveal an important, new method of attack. After all, then it would probably already be common practice for attackers. And that is not the case.
No, the main point is to see (ransomware) attacks on OT environments for what they are: often IT-driven attacks that impact organizations’ OT environments. It is therefore important to stop the attacks in the IT environments. After all, once in the OT environment, there is virtually no security tooling to help organizations anymore. Then attackers can go about their business virtually undisturbed without anyone seeing them. “Living off the land”, as Derbyshire calls that. For criminals who want a quick ransom, this may not be the quickest route to success, but for state actors and hacktivists, it can be interesting.
OT security does need more attention
Finally, it is worth noting that OT security does need more attention. Derbyshire and Van der Walt do not dispute that at all. Above all, they want to contribute to the discussion about what an OT attack really is. As Van der Walt summarizes, “IT security has been around for about 25 years, OT security is still very young. We should have learned from our mistakes, so it shouldn’t take another 25 years to get OT security to where IT security is today.”
This ambition starts with a good understanding of what we are talking about. That is an important part of what Derbyshire and Van der Walt from Orange Cyberdefense want to contribute to the discussion. In passing, they also show what a real OT attack might look like. We can learn something from that, too. And that is ultimately the point of taking a more scientific approach: making hypotheses, expanding on them or trying to disprove them, and thus trying to advance the common knowledge about, in this case, the security industry.
Also read: OT security of data centers should be a top priority