Many security investments do not deliver what was expected or hoped for. Organizations can do better, however, if they invest wisely, and base their investments on hard evidence.
The number of security solution providers on the market is staggeringly large. The total runs into the thousands, all of whom adamantly claim that what they provide is indispensable for organizations. Many are rather specific point solutions, others opt for the platform approach. It says a lot that the number of security vendors that have a turnover of more than $1 billion per year can be counted on the fingers of two hands. Certainly if you look at the pure security players and leave out vendors such as Cisco and VMware.
On the one hand you can say that this variation and choice is a positive thing, because the larger security issue is very complex. You need many different solutions to be able to set it up properly. So it’s nice to have a choice. On the other hand, the availability of a tool for every specific need makes it tempting to just throw a new security tool at every problem. Without really looking at how it integrates and continuously checking whether it all delivers what it is supposed to. Many of these kinds of investments are made in a kind of project form, where people move on to the next project when one is finished. There’s hardly any follow-up.
Promising the world doesn’t help either
Mind you, not only the customers of security solutions are part of the underlying problem. The vendors that are active in this industry have a role to play here too. They often promise the world. That is, they overpromise how much a particular solution will bring an organizations. We are very familiar with that side of the story over here at Techzine. Existing vendors send us marketing and PR statements that sound too good to be true on a daily basis. New vendors als knock on our door on a regular basis, to add to that daily stream of ‘good news’, with new ‘disruptive’ solutions that promise to solve the security troubles of organizations. That makes it potentially even more confusing for decision makers at organizations, who have to consider their budget restrictions too.
An ever expanding number of offerings in the market isn’t necessarily a bad thing, by the way. In fact, it is often simply necessary. A good example of this is the rise of API security. Until a few years ago this did not really exist, now it should be high on the list of priorities at organizations. In general, the layering of the security infrastructure follows that of the attacks. With a new type of attack, in this case via APIs, a new layer must also be added.
Silver bullets don’t seem to be working
Organizations with security issues are very often tempted to purchase something new to face that new issue. Whether this is due to big promises from suppliers, fundamentally new threats or the strategic vision of an organization depends on the situation. The available budget obviously also plays an important role.
If we consider for a moment what has happened in recent times, we don’t get the impression that organizations are safe from attacks. At least not safer than they were a few years ago. That is, breaches, leaks and other security problems still occur. In fact, it seems to get worse, not better. Now, against some problems security tools can’t do much. Think of zero-days like the recent Log4Shell vulnerability. Nobody was aware of this, so it’s difficult to assess whether your security controls are working properly.
However, attacks, targeted or otherwise, by means of phishing, ransomware and other methods are also very common. In theory, the right tools, and things like security awareness training should be able to protect organizations adequately. Based on what we read and hear, this isn’t necessarily the case. Obviously, this also depends on the number of attacks that occur. That is, if that number increases dramatically, tools can detect or prevent a higher percentage of attacks, but still let more attacks through undetected than was the case a couple of years ago.
Security becomes everyone’s business
A consequence of the situation outlined above is that more and more vendors are getting involved in security-related solutions. For example, over the past few years we have noticed a strong rise in the ransomware theme among vendors such as Rubrik, Veeam, Commvault and Cohesity. These are traditionally suppliers of data management solutions and backup and disaster recovery. Even a company like NetApp, with its origins in infrastructure technology announced at its recent Insight conference that ONTAP now has a feature that can detect ransomware.
In itself, detecting ransomware in organizations’ backups sounds pretty logical and desirable. After all, ransomware is all about data, so who better to come up with something to tackle this problem? However, it is also a last resort to detect it at that point. It’s fine if there’s really no other way, but ideally you want to detect this much earlier. A backup is pretty much the last stop of data within an organization. So you could argue that it’s actually a sign of weakness that we can’t seem to tackle ransomware before that point. That is not to say that the capabilities in the tools of the vendors mentioned above aren’t useful. They can be, but it is far from an ideal situation.
In other words, it seems as if security has become everyone’s business. Again, that’s not a bad thing in and of itself, because it fits within a layered security approach. However, you still need to set that layered approach up properly. And that’s where the shoe pinches in practice. To find out more, we talked to Ross Brewer, the VP and GM of AttackIQ for (among others) the EMEA region.
Systemic failing
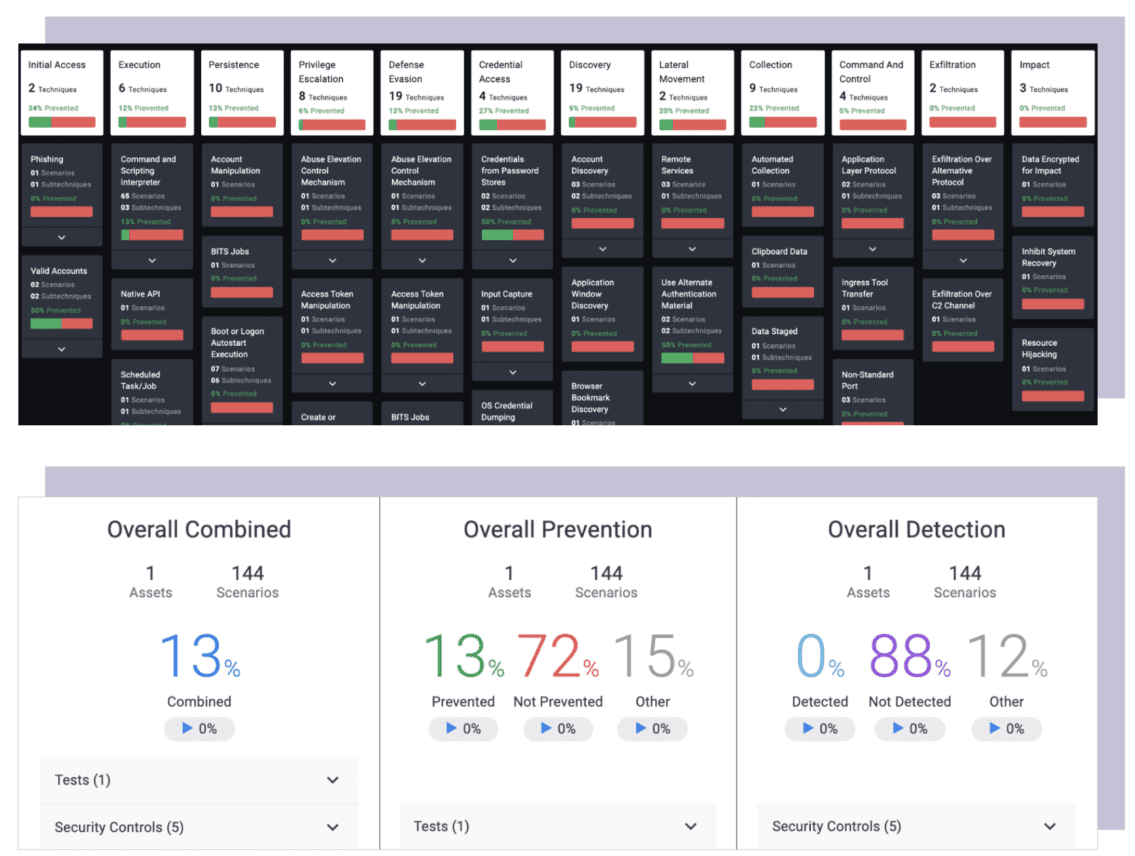
AttackIQ is one of the founders of the breach and attack simulation market. With the solutions of this company, it is possible to make decisions based on actual insights about where investments should be made regarding cybersecurity. Organizations can use them to verify and validate how effective their security controls are. They do this on the basis of the real, actual production environment of the organization. So this is not a nice, fancy, and unrealistic simulation. Security vendors also use the solutions of AttackIQ to test the effectiveness of their own solutions.
Fundamentally, AttackIQ is needed in the market because of the systemic failure of the security industry, Brewer indicates. “AttackIQ is the feedback loop that is needed, but always lacked,” he summarizes. That is, many organizations make decisions regarding cybersecurity without basing them on data or evidence. That’s why the system as a whole is fundamentally broken. With AttackIQ’s platform, the company wants to move toward what Brewer calls evidence-based security during our conversation.
The need to add a feedback loop for security policies is also immediately apparent to Brewer. “In 80 percent of breaches, the controls were in place, but not doing their job,” he indicates. In other words, 80 percent of breaches could have been prevented without making additional investments. Assuming this is true, it is quite sensible say that the way security vendors and organizations work together to address cybersecurity is fundamentally flawed.
Invest sensibly
Determining that the current situation is not working is, of course, only part of the story. Far more important is what organizations can do to make this work better. That’s what they can use AttackIQ’s platform for, says Brewer. He summarizes the guiding principle here as, “Stop investing in the things you’re not sure you need.” Only if it’s demonstrably a good investment should you do it. That’s ultimately what evidence-based security is all about. This obviously involves preventing breaches and the like, but also involves things like governance and compliance. For those parts, too, you shouldn’t just buy any solution. That also has to be done on the basis of actual data.
Investing wisely in cybersecurity is not so much about saving money, by the way, even though that will almost certainly be a consequence of this approach. It’s primarily that you invest in the right solutions and products and configure them optimally. Brewer gives the example of a customer who wanted to invest $30 million in red teaming worldwide. This was going to take about 8 months in total, with the expectation that the outcomes would not be hugely satisfying. If you can replace this by deploying a platform like AttackIQ’s in the production environment of such a customer, you will get much more out of it, he is convinced.
AttackIQ is a transparent platform
There is nothing secretive about AttackIQ’s platform, by the way, Brewer points out. “The source code is completely open and we produce very detailed logs,” he explains. This, he says, also helps to better train the teams that have to work with it. These can really aggregate knowledge and build experience with it, because it’s all so transparent. At least, that’s the point Brewer wishes to convey.
In addition to being relatively transparent, AttackIQ’s platform is also very simple in terms of architecture. The platform contains all of AttackIQ’s knowledge gained by the company over the years. That should be quite a wealth of knowledge when you consider that AttackIQ is part of MITRE Engenuity, the organization behind the MITRE benchmarks and CVEs. From this platform, AttackIQ can perform attacks in the production environment to see if the security controls are doing their job properly. To provide visibility into the entire environment, AttackIQ uses agents, but also works agentless. The latter is important for security controls where no agent can be installed, such as firewalls and DLP solutions, among others. Management can be done in the cloud or on-premises.
Prevention and detection
The purpose of the platform is to test both the prevention and detection capabilities of an environment. Prevention obviously is a very important goal. However, APIs allow the platform to also communicate with security tools and a SIEM and/or SOAR. With that, it should also cover the detection component. In any case, we think the focus on prevention is a good thing. In recent years, this seems to have been neglected, due to the mantra that it’s not a matter of if but when a breach occurs. The fact remains that prevention is still better than cure, something we already discussed in more detail in our article about Deep Instinct last year.
The idea of AttackIQ’s platform, by the way, is not that you deploy it once. That would not only be a somewhat poor business model for AttackIQ, but also not add much for organizations that deploy it. It is the feedback loop that we talked about above that continuously adds value. It allows organizations to move away from the project-based approach to cybersecurity. An approach that doesn’t look back at the effectiveness of solutions after they are deployed. And an approach that is explicitly not based on actual data.
Start with the right conversation
Assuming that AttackIQ’s marketing department does stick to the facts and doesn’t promise more than it can deliver, the platform can deliver a lot to organizations. That is, more sensible investments in better functioning cybersecurity sounds like a winning combination. As always, however, technology alone is not enough. You also need to have better conversations within the organization. We also touched on that theme last year when we spoke with Roel van Rijsewijk of Thales.
For Brewer, the right conversation is primarily about looking at how people are working on the business side of an organization. That’s where people use data to demonstrate what they’re doing. The same needs to happen for cybersecurity, he believes. “We need to get away from seeing security as a dark art,” he states. FUD (Fear, Uncertainty and Doubt) also has no place in the daily discourse around security anymore, he believes. It has to be conversations based on data and evidence that certain things work or don’t work.
This non-technical component of the approach AttackIQ is pursuing is undoubtedly more difficult than the technological challenge. It is, however, the first step toward what it is striving for. If what AttackIQ claims is true, that 80 percent of breaches can be prevented, the end result of this new approach to the security issue is very attractive. In addition, it is almost certainly budget-friendly. The investments can now be focused primarily on the 20 percent that are really needed. If all goes well, this will ultimately result in better protected organizations and a generally healthier security industry. And we all benefit from that.
