DNS and network data contain much information about potential emerging and existing cyber threats. With the introduction of SOC Insights, Infoblox is bringing this data to the Security Operations Center.
Infoblox comes originally from the networking world, focusing on the Domain Name System combined with DHCP (Dynamic Host Configuration Protocol)- and IPAM (IP Address Management). Together, they form the BloxOne DDI platform. In recent years, many security options have been added to the platform, as the technology also proves suitable for making an organization more secure. For example, DNS has information about malicious domain names.
What kind of insights does Infoblox provide?
Now, Infoblox will offer a service that automatically collects large amounts of DNS threat intelligence. The service then classifies the threat by using a trained AI model. The model can determine the severity of the threat to decide how quickly to respond. Optionally, it can be resolved automatically with technology from Infoblox or another security vendor, but because of its complexity, the threat can also be forwarded to a SOC employee.
The insights Infoblox provides to the SOC qualify as either a configuration problem or a security insight. For configuration insights, SOC Insights looks at proactively finding weak or dangerous configuration errors. According to Infoblox, it is still too common when investigating a threat to see that a misconfiguration or security tool integration challenge is the cause. In the image below, the left side shows what configuration insights SOC Insights looks for.
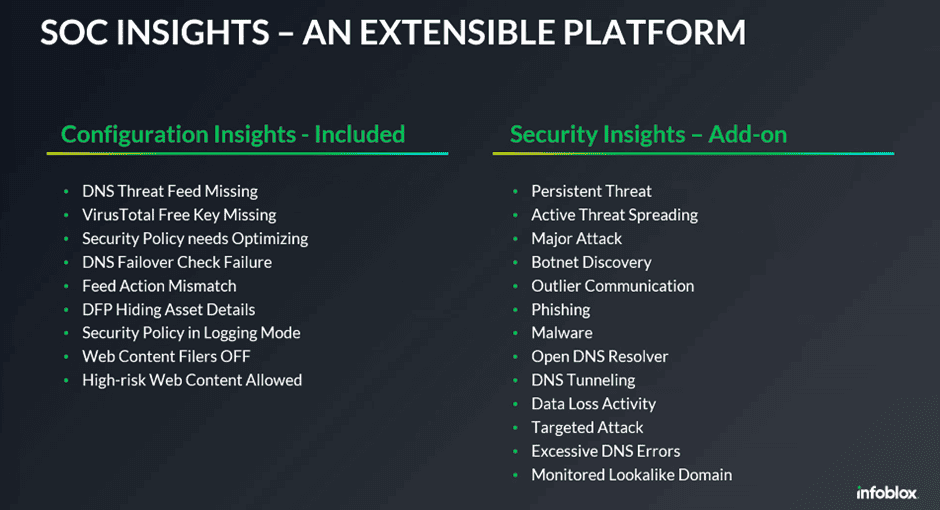
The right side shows what Infoblox’s new service looks for pure security activities. Infoblox’s AI model looks at activities on the network, DNS system and ecosystem to find such security events. As the figure shows, Infoblox analyzes and classifies a huge number of events. SOC Insights, therefore, applies strict classification to the alerts, allowing for considerable deletion in the mountain of security events. This leaves only the valuable insights that require an autonomous response or a manual response from a SOC employee.
These insights should also further strengthen the SOC’s ecosystem. It can share the insights with other security tools, such as SIEM and SOAR tools commonly used in the SOC.
For either option, companies must purchase BloxOne Threat Defense “Business Cloud” or “Advanced. Those versions of the DDI platform can collect a large amount of information from DNS. Configuration insights are standard in BloxOne Threat Defense, while security insights can be added to BloxOne Threat Defense as an add-on.
Eliminating response time
The main reason for Infoblox to come up with SOC Insights remains the large amount of information in DNS about cyber threats. Often, DNS data contains the first indications of an imminent attack. However, SOC staff do not have sufficient access to this information, Infoblox notes. This makes an organization vulnerable, especially given the increasingly sophisticated nature of cyber attacks. Therefore, an extra step to detect a hacker early is welcome.
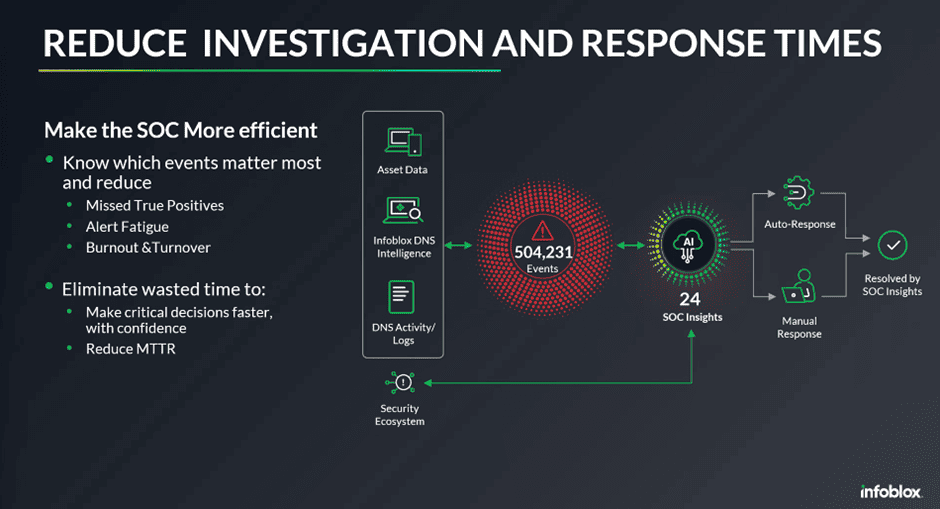
In addition to detecting attacks early, SOC Insights aims to reduce or eliminate mean-time-to-response (MTTR). MTTR is the time required to resolve a problem. To reduce or eliminate this time, SOC Insights consolidates individual alerts into “unique insights.” Infoblox describes them as unique because of access to details about devices, events and attackers’ infrastructure combined with DNS data. “This eliminates the need for SecOps teams to spend time tracking each individual alert or waiting on NetOps for user and device information for context around threat activity,” Infoblox concludes.
Tip: Infoblox launches Network Identity Operating System (NIOS) 8.6.1