Okta and Cisco recently warned of an unprecedented spike in “credential stuffing” attacks. What does that entail? And what do you do about it?
Credential stuffing involves an attacker using account information stolen elsewhere to get into a particular account. If someone’s credentials were captured in a data breach of a particular service, chances are the person in question is using that login data elsewhere. In other words, a single hack can compromise many accounts in one go.
This process reflects the modern nature of cybercrime. After all, data breaches occur regularly. Malicious parties often sell the personal data captured in the process on the dark web. It’s then up to other cybercriminals to actually exploit the data itself.
Tip: Verified X accounts being traded on the darkweb
Credential stuffing: an automatic process
Performing credential stuffing is relatively easy. Botnets can attempt to take over accounts on a large scale on behalf of the attacker. A global botnet (a network of devices that can be deployed by hackers) not only performs automatic login attempts at lightning speed, but also makes it a lot harder to identify who the perpetrator is.
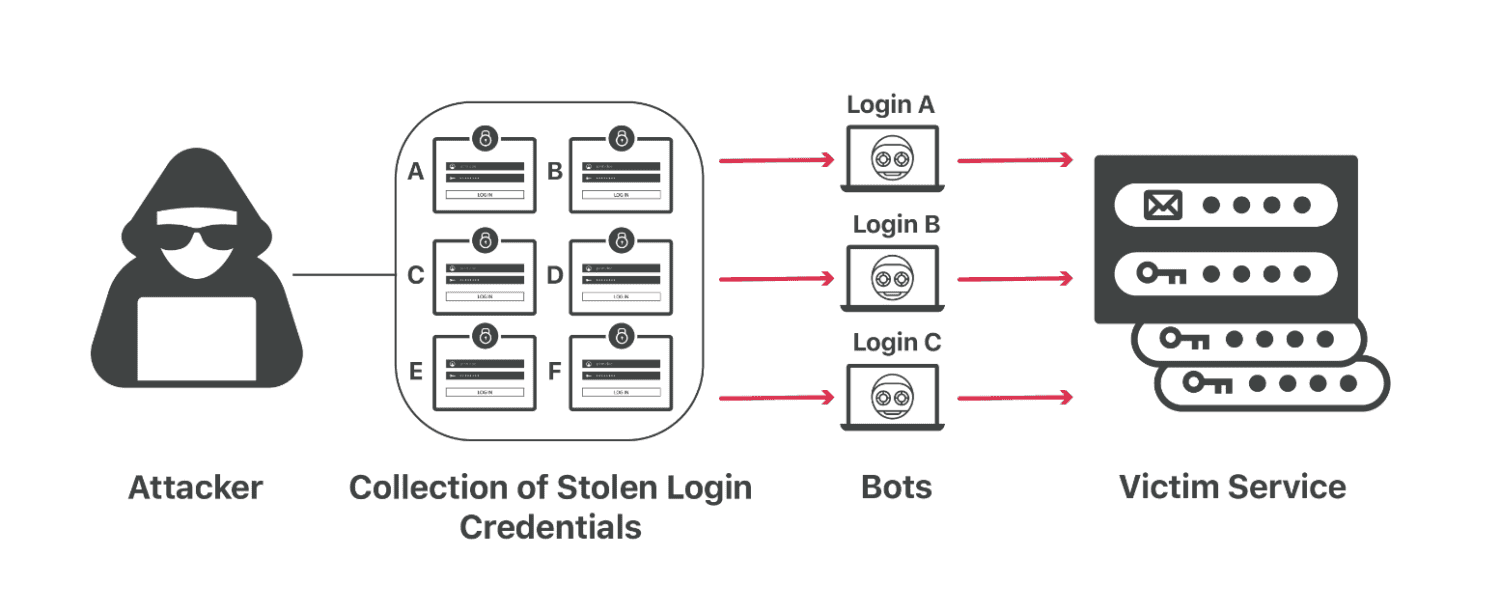
This method bypasses an essential line of defence against automatic login attempts. For example, with “password spraying,” attackers continually attempt to access accounts with a handful of commonly used passwords. By “brute forcing” the login process, the attacker hurls many passwords toward a single user login account screen. However, many services allow only a limited number of login attempts before access is denied. This complicates the successful execution of the above methods. In contrast, a credential stuffing attack “convinces” any service that only asks for the correct password. Thankfully, it’s become the norm to require multifactor authentication (MFA), so many services are unaffected.
The threat of credential stuffing should, however, not be underestimated. CrowdStrike emphasizes that tens of billions of usernames and passwords have been stolen or leaked in recent years. This attack method also has a very low barrier to entry: it doesn’t require any programming experience or other expertise to attack. With some money and a bit of time spent surfing the dark web, someone can start stuffing credentials at will.
A high volume is needed to ensure successful attacks, though. Cloudflare cites that experts typically put the success rate at 0.1 percent. A simple calculation shows that about 100 attacks will be successful out of every 100,000 attempts. Fortunately, there is plenty that can be done against such attacks.
The pass cut off
Both Okta and Cisco have recently experienced credential stuffing attacks. Okta reports that all such requests originate from the TOR network, which anonymizes the source. Successful attacks occurred at organizations running the Okta Classic Engine with ThreatInsight set to Audit-only and not in Log and Enforce mode. Classic Engine has since been replaced by the Okta Identity Engine. Affected organizations still using the old software have simply misconfigured their software, though. It can still be used safely for user authentication management.
A similar attack campaign is underway against Cisco and against other VPN vendors such as CheckPoint and Fortinet. The Cisco Talos research team reports that the attempts in these campaigns involve specific and generic usernames and passwords. The advice from Cisco Talos varies, but it refers to general recommendations for remote access VPN services. Such a service is inherently risky, as a recent MITRE attack showed. However, things like data logging, blocking against rogue sources and other hardening methods help considerably.
Getting the basics right
At the very least, anyone using modern services correctly already has enabled multifactor authentication (MFA). This stops an unknown IP address from accessing an account through a stolen username-password combination. In addition, one should never reuse the same combination. That sounds a bit extreme, but password managers with biometric authentication make logging in through a browser easy enough these days without even requiring a password to be remembered in the first place. The difference with logging in through such a manager rather than based on your own memory is that the credentials can be as obscure as possible and never need to be repeated.
Since the Covid-19 pandemic, many parts of the workforce have become accustomed to hybrid working, something that indirectly promotes the use of personal login credentials. After all, those who continually log into personal Outlook, Facebook and YouTube accounts on their own PCs with the same credentials will soon choose to use the same credentials on professional apps. To avoid that, a culture change of sorts among invididual IT users is needed. Alternatively, organizations simply determine how employees should log in and set it as policy.
For an organization, credential stuffing attacks can cause problems still, even if no account is taken over. This is because a large number of login attempts has a taxing effect on the organization’s IT environment, effectively causing the botnet to launch a DDoS attack. It’s not the intention of the criminals, but it’s still a potential cause for downtime. Thankfully, organizations can defend themselves against a DDoS attack in relatively simple ways. Minimizing the attack surface is perfectly possible, such as by making as few services internet-accessible as possible. Buying into identity services like Okta also provides external protection. In addition, such vendors and various security parties ensure that notorious IP addresses are already immediately rejected.
