Initial Access Brokers (IABs) are a growing threat to businesses, according to research by Group-IB. These IABs find vulnerable companies and sell access to other cybercriminals. It makes the work of ransomware operators easier. As a result, the number of ransomware attacks is also increasing. We spoke about the development with the new CEO of Group-IB, Dmitry Volkov.
Cybercriminals are known for constantly adapting their techniques in order to keep attacking enterprises and individuals. In doing so, they also respond to innovations on the defence side. After all, if cybercriminals use old tactics, they will eventually no longer be able to get into company networks, because the defence knows exactly how to keep all the obsolete attacks at bay.
To gain insight into innovation, the cybersecurity industry is conducting a lot of research. Group-IB, which offers products for detecting and preventing cyberattacks, recently published its annual survey. In it, it zooms in on the growing role of collaboration between cybercriminals.
Access to companies
Group-IB’s research mainly shows that hackers are increasingly cooperating. Individual crimes, such as carding, are in decline. According to Volkov, the increase is due to the number of attempts to sell access to vulnerable corporate networks. This form of cybercrime, also known as IAB, has a relatively low barrier to entry. Poor corporate risk management and the availability of tools for attacking corporate networks are causing the IAB market to be at an all-time high, according to the study.
Globally, the network access market grew from around €5.49 million in July 2019 to June 2020 to €6.36 million the same period a year later. Not a very significant threat when you compare these figures to the total cybercrime market, you might think, but underlying figures make the development worrying. For example, the number of offers to sell access almost tripled, from 362 to 1,099. Underground forums play a role in this because users can access them relatively easily. There are forums that can be accessed via a normal internet browser, although many require additional requirements such as the TOR network and VPN services. A worrying development that Group-IB observes on the forums is that the number of active initial access brokers increased in one year from 86 to 262, with 229 new sellers entering the IAB’s scene in the review period.
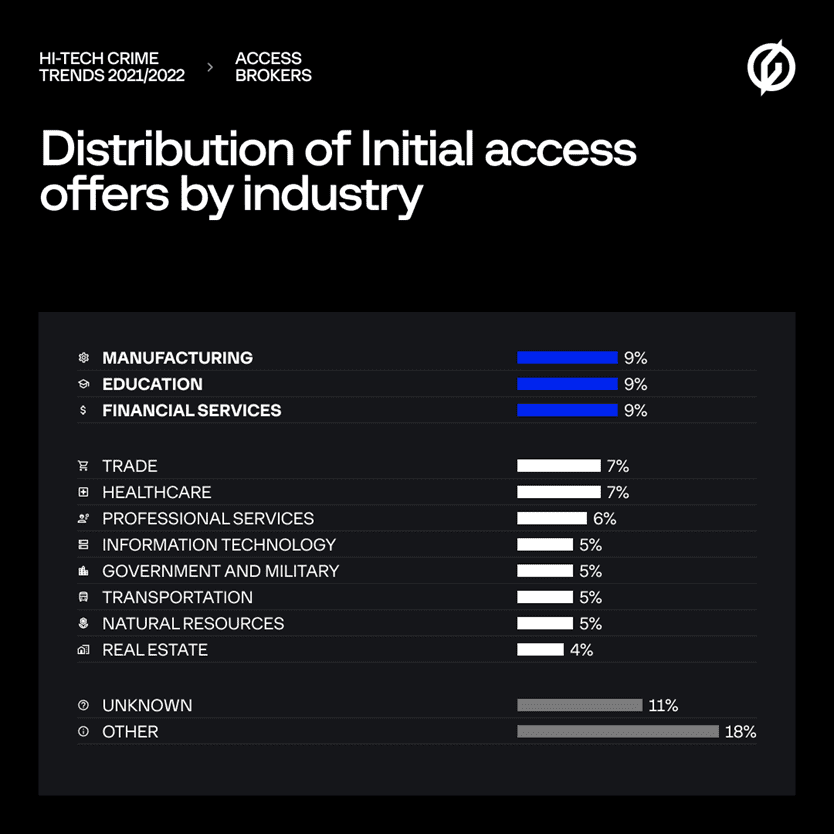
“The Access Brokers, for example, provide access to the network through an account of a regular employee or top manager. They actually target every sector. Manufacturing, education and financial services stand out, but the focus is also increasingly on government agencies,” says Volkov. The figure below shows the distribution by sector.
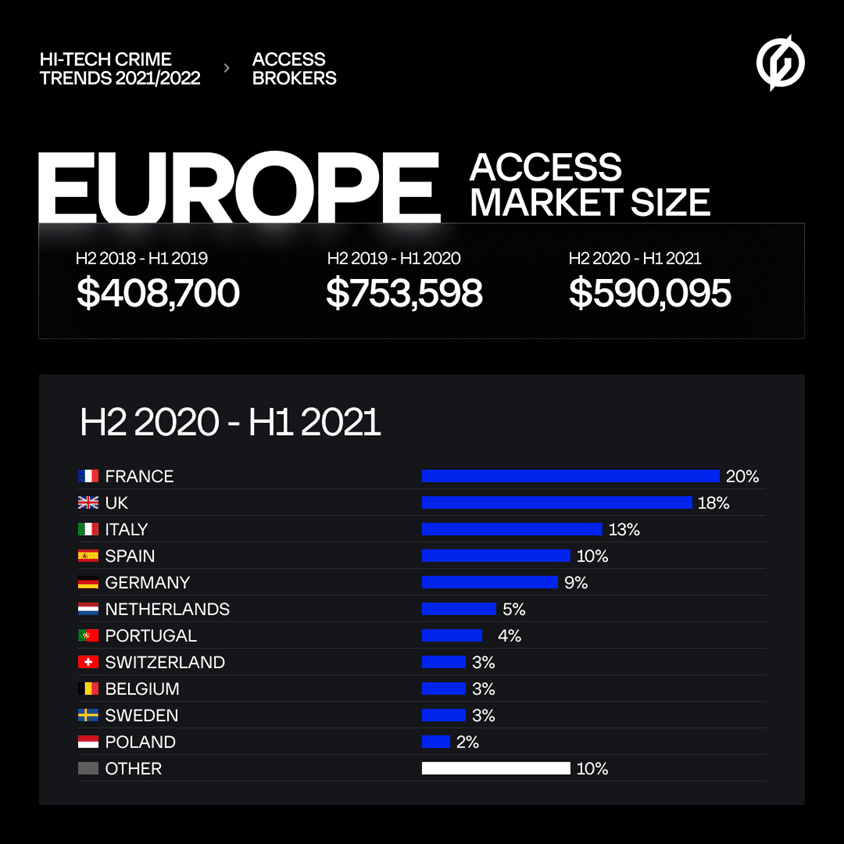
Volkov sees IABs as a global problem that Europe cannot ignore either. In one year, access to 261 European companies was offered. A threefold increase compared to H2 2019 – H1 2020. If this growth continues, IABs will be an immense threat in the foreseeable future. Especially in France and the United Kingdom, they have to reckon with the threat, where there are relatively many companies with vulnerable networks to which access is sold. The Netherlands is also high on the list, as the following data show.
Ransomware unprecedentedly popular
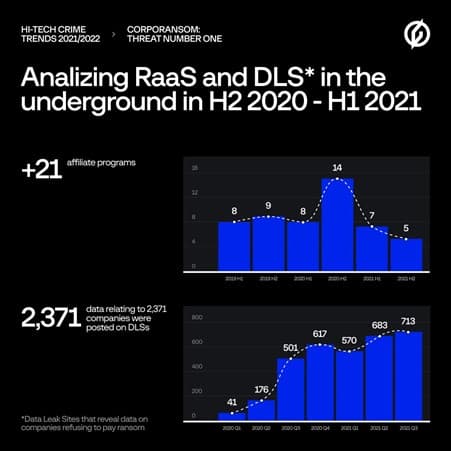
Volkov sees the initial access market growing mainly because of the popularity of ransomware attacks. The IABs lower the barrier for ransomware operators, who no longer have to try to break into a company network themselves. Because of the cooperation between the IABs and operators, Group-IB now speaks of a ransomware empire. An important additional driving force is the increase in the number of the so-called ransomware as a service (RaaS) programs, where advanced cybercriminals develop the malware and then offer it as a service to the affiliates. Infrastructure, including admin panels, communication panels with the victims etc. is also arranged. The RaaS affiliate only has to carry out the attack.
During the period covered by Group-IB’s research, the company identified 21 new RaaS programs. This would represent annual growth of 19 per cent. “The cybercriminals mastered the use of the double extortion technique thanks to Data Leak Sites (DLSs), which are used as an additional source of pressure on their victims to make them pay the ransom by threatening to leak their data. In practice, however, victims can still find their data on the DLS even if the ransom is paid,” states Group-IB. The number of new DLSs has more than doubled in the space of a year.
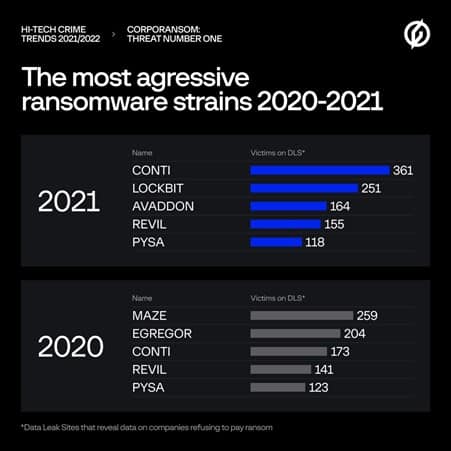
Group-IB analysed the 2021 Data Lake Sites ransomware and concludes that Conti is the most aggressive ransomware group. This group claimed 361 victims, accounting for 16.5 per cent of all companies that saw data end up on DLSs. Other malicious malware types were Lockbit (251 victims), Avaddon (164) REvil (155) and Pysa (118). The manufacturing, real estate and transport industries are particularly affected by Data Leak Sites.
The data in this article originates from Group-IB’s Threat Intelligence & Attribution system. The company also draws other conclusions based on the data. A complete overview can be found by clicking here.