
KnowBe4 evolves from security training to human risk management
Security awareness training has come a long way from its origins as a compliance checkbox. Today, it’s evol...

Security awareness training has come a long way from its origins as a compliance checkbox. Today, it’s evol...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
A new CPU vulnerability affects all known computer architectures. The so-called GhostRace exploit makes it po...

In the never-ending game of whack-a-mole between cybersecurity teams and malicious actors, cookie hijacking i...

Two critical vulnerabilities in WordPress plugins from miniOrange will never receive a patch. More than 10,00...

Formula 1 is all about speed. A team's cybersecurity solution must keep up with this. We spoke to Mark Hazelt...
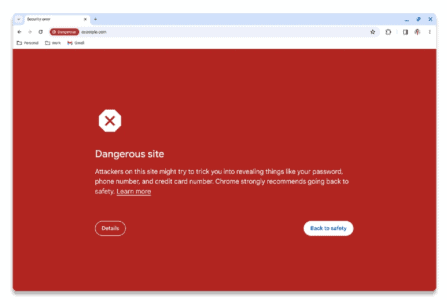
Google is improving phishing and malware protection for Chrome users. Websites are now monitored in real-time...

The startup Avalor has been around for just two years but is reportedly being acquired by Zscaler for hundred...

The amount of secrets leaked in public GitHub repositories is higher than ever. A report puts the total numbe...

Organizations that are part of critical infrastructure face the most cyber attacks in September-December 2023...

The critical vulnerabilities allowed unauthorized access to third-party accounts and sensitive user data. ...

A cybercriminal has been sentenced to four years in prison. The man deployed LockBit ransomware software and ...