The Linux variant of Microsoft Defender for Endpoint has been strengthened.
Microsoft Defender for Endpoint is Microsoft’s answer to the demand for endpoint threat resistance in Windows, macOS and Linux. Functionality varies by the operating system. Microsoft announces that Microsoft Defender for Endpoint on Linux was enhanced with a range of new features.
Live response
First of all: live response. The term encompasses multiple tools that should allow Linux threats to be addressed and prevented in real-time by executing scripts to investigate suspicious events, collect forensic data and automatically respond to events on a per-device basis. Both single commands and Bash scripts — preset orders of commands commonly used for automation in Linux — are supported.
Live response is currently only available per public preview: manual activation via the settings of Microsoft Defender for Endpoint is required.
Behavior monitoring
Runtime memory scanning and behavior monitoring also make an appearance. Both additions serve for more effective threat prevention.
Runtime memory scanning improves Defender’s ability to analyze work processes — and the interactions between work processes. Here, the focus is on finding threats that do not take place on disks, but in the memory of endpoints. Microsoft mentions ‘Meterpreter’ as an example: a threat that is deployed directly in the working memory of an endpoint, does not write anything to disk and nevertheless obtains authorization for the system. Monitoring via runtime memory scanning brings the threat type to the surface.
Behavioral monitoring provides a shield against ransomware attacks that use legitimate tools to encrypt files, and thus tend to pass the radar of endpoint security. GnuPG is an example of such tools. The encryption software, popular in Linux environments, was previously exploited by ransomware Qwerty to encrypt systems undetected. The new behavior monitoring promises to recognize threats like Qwerty, which largely rely on legitimate tools and processes.
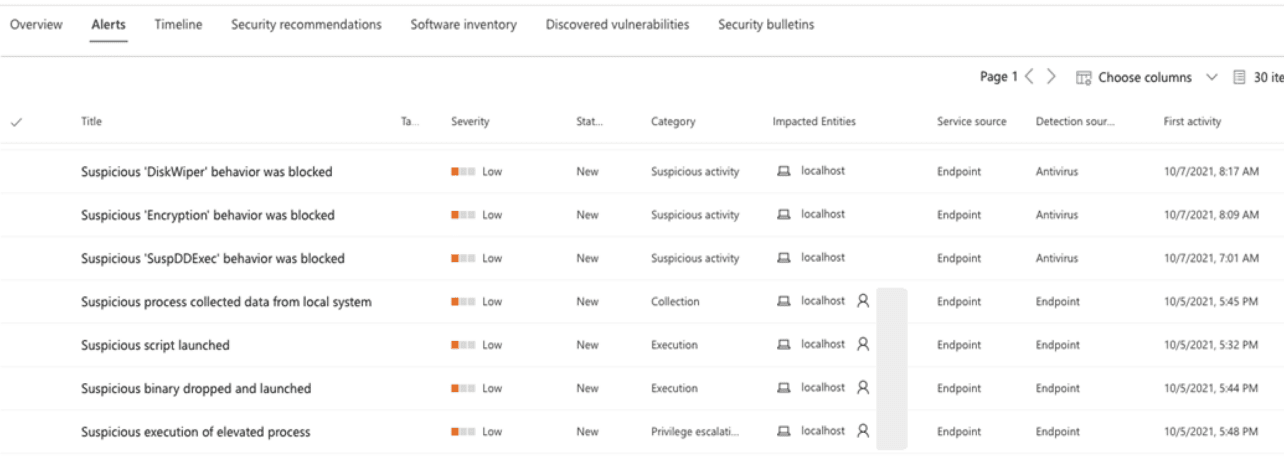
Behavior monitoring will be automatically enabled for users of Microsoft Defender for Endpoint on Linux in the coming weeks. Enabling cloud-delivered protection in the settings of Microsoft Defender for Endpoint is conditional. After all, the frame of reference with which behavior monitoring analyzes endpoints comes from the cloud.
Support for Amazon Linux and Fedora
Microsoft Defender for Endpoint is available for a select number of Linux distros and versions. Among them: RHEL, CentOS, Ubuntu, Debian, SUSE and Linux. In addition to the aforementioned live response, runtime memory scanning and behavior monitoring, Microsoft is adding support for two new distros: Amazon Linux 2 and Fedora 33+.
Tip: Microsoft marks growth ambitions with Defender for Business and Cloud
