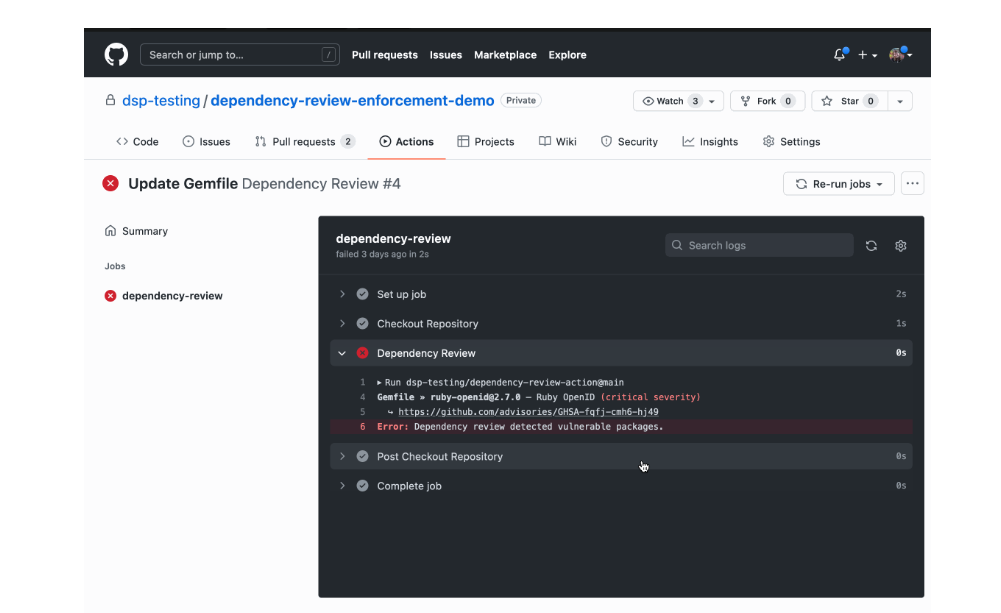
GitHub released Dependency Review GitHub Action. The tool allows users to scan pull requests for new dependencies that may introduce (supply chain) vulnerabilities.
The tool checks whether new dependencies contain vulnerabilities. Vulnerabilities are found by scanning dependencies in pull requests against the GitHub Advisory Database. The database contains a collection of CVEs and other advisories on security flaws in open source software.
Alerts and contextual advice
Whenever a vulnerability is found, developers receive an alert and contextual advice to help fix vulnerabilities. Furthermore, the tool provides information on dependency changes, removals or additions. The tool also shows how many projects use vulnerable dependencies.
Implementation and availability
Developers can use an API endpoint to implement the Dependency Review GitHub Action tool in the workflows of existing projects. This can be done via the Actions tab under the Security menu or directly from the GitHub Marketplace.
Dependency Review GitHub Action is now available in public beta for all public repositories and for private repositories. For the latter, companies must use GitHub Enterprise Cloud in conjunction with a license for GitHub Advanced Security.
Tip: GitHub Advisory Database now welcomes user contributions on threats
