
EU countries form Semicon Coalition to bolster semiconductor industry
At the request of the Netherlands, nine EU countries are uniting to strengthen Europe's semiconductor industr...

At the request of the Netherlands, nine EU countries are uniting to strengthen Europe's semiconductor industr...

Europe has no chip alternative for AI companies at the moment. The chips AI companies purchase at this point ...

At SUSECON 2025, a diverse set of updates were announced around Rancher Prime, SUSE's container management so...

Beginning today, SUSE Security (formerly NeuVector) will integrate with Microsoft's Sentinel SIEM/SOAR offeri...

A new study notes that business applications are becoming increasingly insecure. The number of (code) errors ...

Apple has fixed a dangerous zero-day vulnerability in Safari's WebKit engine with an emergency patch. The tec...

ASML's newest chip machines will soon arrive at the Flemish research institute Imec. Both parties have reache...

The Netherlands will house the first quantum computer in Digital Realty's AMS17 data center at the Amsterdam ...

Google appears to have opened the attack on DeepSeek by introducing its Gemma 3 portfolio of lightweight LLMs...
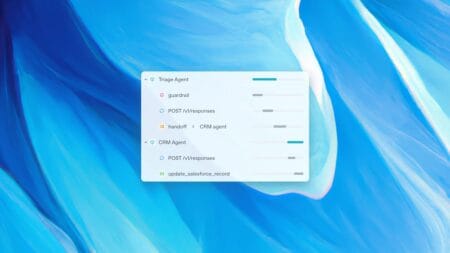
OpenAI has launched a new set of APIs and tools, making it easier for developers to build AI agents. The new ...