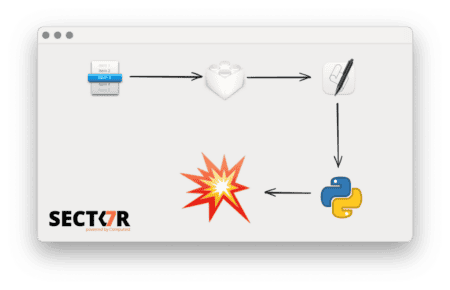
Dutch hacker finds critical vulnerability in macOS
The process injection vulnerability allows access to webcams, microphones and sensitive information. Thijs...

The process injection vulnerability allows access to webcams, microphones and sensitive information. Thijs...
New capabilities are coming to Salesforce's integration platform to support the work of developers and busine...

The beta release of Einstein Copilot for Tableau is now available. Users in all kinds of roles can receive AI...

OpenAI has introduced tools that allow developers to fine-tune AI models more efficiently than before. On top...

Increased demand for NAND and DRAM processors is a significant driver of higher profits for the first quarter...

Regulators are not shy about thwarting Big Tech acquisitions. Yet Google parent company Alphabet may be willi...

In response to -certainly not unwarranted- concerns about job loss due to the rise of AI, major technology co...

AWS is laying off hundreds of employees active in sales, marketing and services. It says the round of layoffs...

Windows 11 Insider build 26100 includes a significantly faster Microsoft Store. The feature was not mentioned...

DataStax, specializing in generative AI data stacks, has acquired the open-source visual framework Langflow. ...