Research team Mandiant has seen that attacks via USB malware have experienced a threefold growth. These attacks aim to use a malicious piece of software to make off with classified information.
Mandiant, which is part of Google Cloud, highlights two espionage campaigns in a blog post. First, the so-called SOGU malware, which the company says is one of the most common software variants that land on a PC via a USB drive. This group attacks both state agencies as well as private companies. Mandiant sees China’s TEMP.Hex as the culprit, whose practices drive that country’s state espionage and economic interests. Earlier today we reported on more spying attempts the Chinese government is accused of.
Tip: ‘Chinese email hack affects Western European governments’
Mandiant’s second example is SNOWYDRIVE, which creates a backdoor at a target and then remotely controls the system. In doing so, it also attempts to move laterally within a corporate network to gain as much access to sensitive data as possible. The group behind it, according to Mandiant, is UNC4698, which mainly goes after oil and gas companies in Asia.
World view
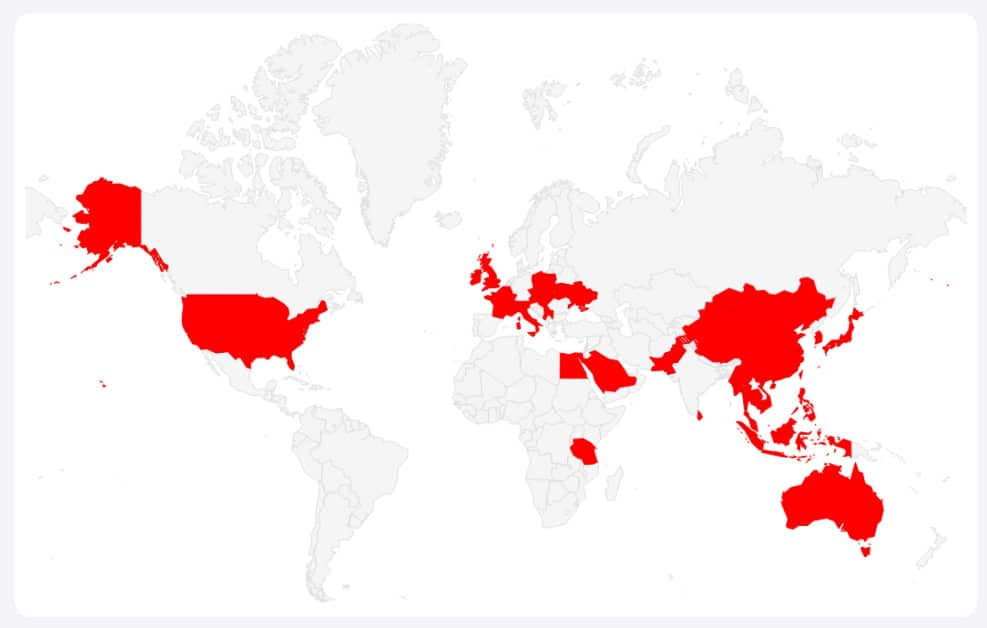
On a global level, Mandiant sees that SOGU attacks are specifically occurring in many places (see image below).
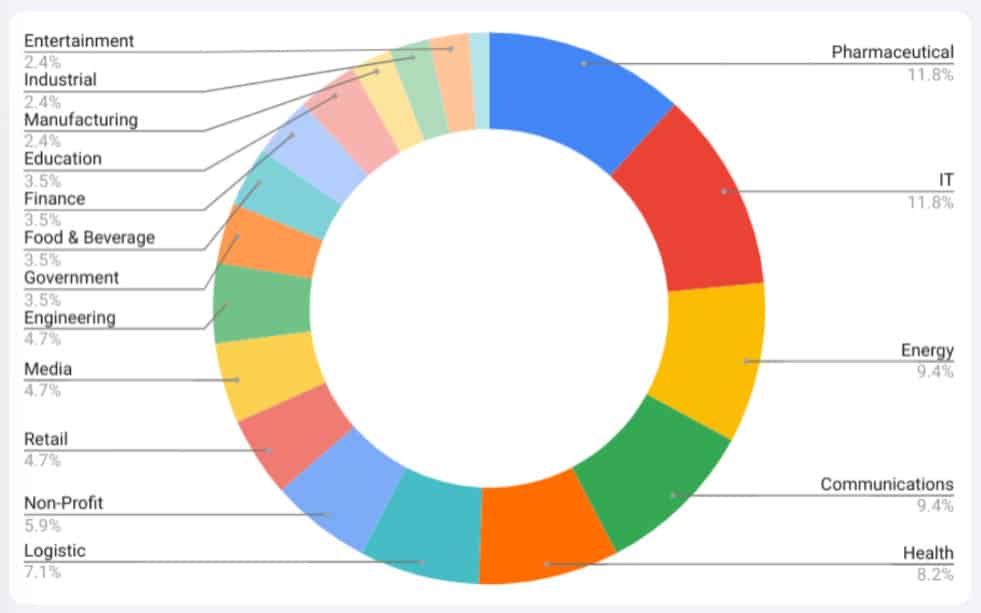
In addition, Mandiant has outlined the sectors where the attacks are occurring. This is a broad spectrum, with pharmaceuticals, IT and the energy sector as the most-affected victims.
Manual action required, but ingenious
Unlike many malware that exploits software vulnerabilities, we are talking about a delivery method that depends on a very cooperative victim or a threat actor who can physically get to a device. While phishing email also needs to fool a target, the level of persuasion is a bit more difficult to accomplish with USB drives. However, some individuals will always uncritically push a drive into their device and launch an .exe on it, after which a complex software process occurs.
With Sogu, the software copies itself to the C drive and to the directory for the existing flash drive. It then exfiltrates stolen documents via HTTP/HTTPS requests. Other possibilities such as file execution, remote desktop sessions and keylogging are conceivable when using the Sogu software.
SNOWYDRIVE works slightly differently: it disguises the files on the local disk in a Kaspersky folder, then the malware’s components work together to install a backdoor. Data exfiltration is also possible with this tool, as well as research and file deletion. By mimicking other legitimate processes, it avoids detection.
Dependent on randomness
Mandiant does not directly explain why attacks have increased so dramatically, but possibly it is simply about recently spurred campaigns. The fact that print stores and hotels are particularly at risk already betrays that attackers will often come up flat. So those who secure their own equipment and don’t simply insert a flash drive will already be safeguarded from this type of attack a lot faster.
Also read: Security-developed tool exploits vulnerability in Microsoft Teams