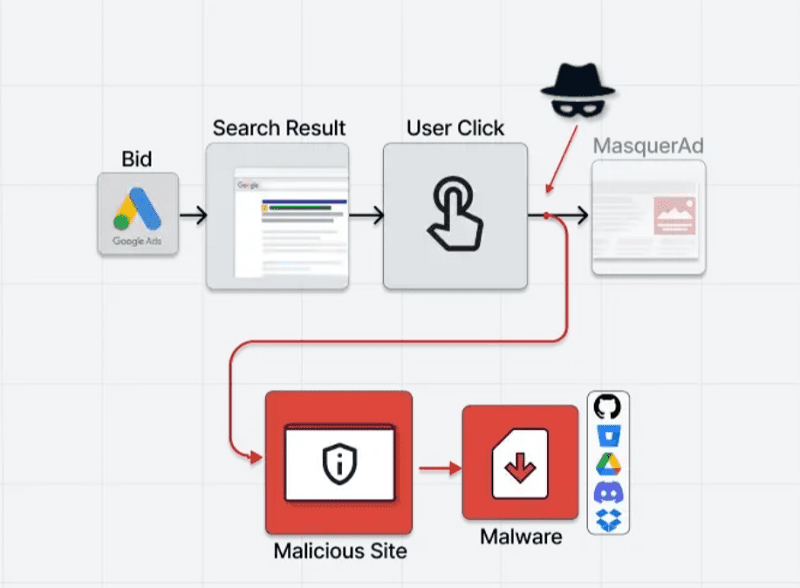
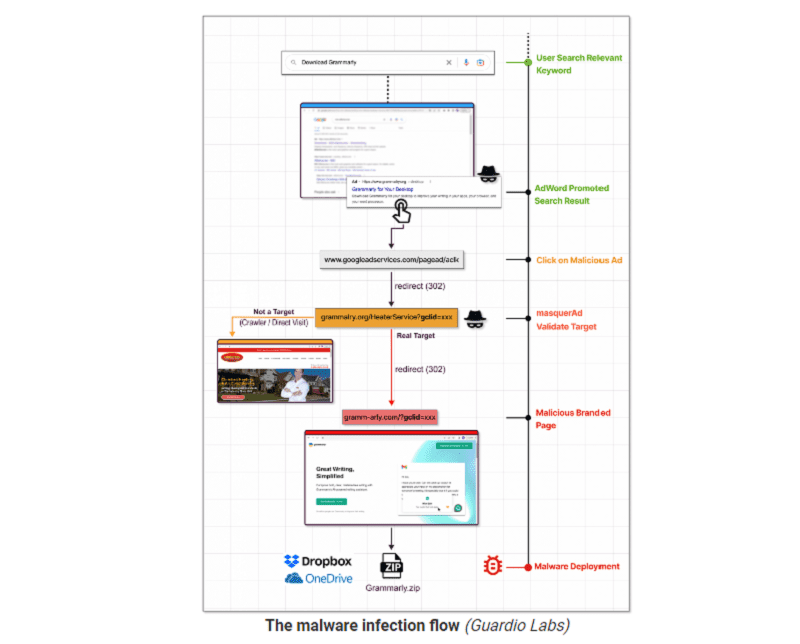
Cybercriminals are increasingly using the Google Ads platform to spread malware as legitimate software. This is according to recent research by Guardio Labs, Trend Micro and others.
Cybercriminals are increasingly spreading malware masquerading as legitimate software. They create a clone of the software’s official websites and distribute versions containing trojans of the software when the download button is clicked. This then allows them to distribute the malware as variants of Raccoon Stealer and IcedID malware loader.
Software increasingly abused for this purpose include tools such as Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird and the open-source Internet browser Brave.
Guardio Labs and Trend Micro research
The investigations by security specialists Guardio Labs and also Trend Micro show that the cybercriminals are now primarily using the Google Ads advertising platform to spread this malware touted as legitimate software. The ads with the spoofed websites are often presented above those of the real ones. Especially users without an adblocker might be more likely to click on these malicious sites as a result, according to the security specialist.
When these “hidden” websites are visited by visitors searched via Google Ads, the server provides a direct redirect to the malicious site and from there to the malware. The malicious sites cannot be found by crawlers and Google’s security specialists, according to Guardio Labs.
The malware is then downloaded as a ZIP or MSI file from legitimate file-sharing services and code repositories such as GitHub, Dropbox or Discord. This bypasses end-users’ anti-virus programs.
Possible solutions
The new malware campaign methods of cybercriminals have been known for some time. Recently, the FBI also warned about this type of campaign. End users who want to avoid being tricked via a spoofed software site should install an adblocker. These filter out promotions from Google’s search engine.
It is also best for them to bookmark official software sites to install updates, for example. Other prevention is possible by paying close attention to the size of downloadable files. Malware often has a larger size than legitimate software. Furthermore, they can also check the URL or domain name for legitimacy. Cybercriminals often use typos, typesquatting, to highlight their malicious sites.