Researchers at Zscaler ThreatLabz have discovered a new infostealer family for Windows systems: Stact Stealer. The sophisticated malware poses as an authentic Google ad.
According to Zscaler security researchers, the infostealer seeks access to victims’ Windows systems by impersonating an authentic Google ad in Internet browsers. Affected browsers include Chrome, Edge, Brave, Opera and Yandex.
Clicking on this rogue ad infects the operating system with malicious code. This code specifically targets stealing sensitive data such as login credentials, credit card information and details of crypto wallets.
Attack path
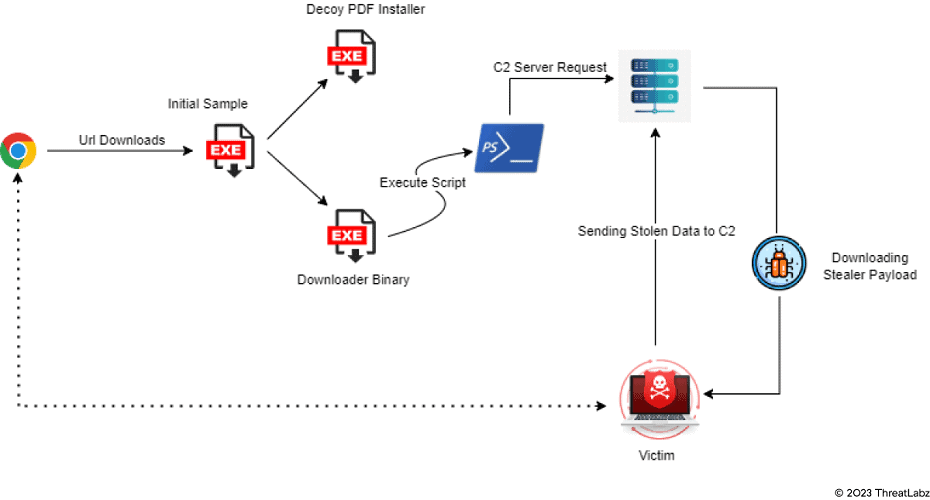
Zscaler has obtained a clear picture of the attack path carried out by the hackers using Statc Stealer. The operation starts by tricking users into clicking on a malicious link somewhere in the Web browser. It then downloads a sample file and executes a Decoy PDF Intsaller.
The sample file also executes a Downloader Binary file designed to facilitate Sttct payload downloading via a PowerShell script.
Once Statc Stealer has extracted the desired information, the data is encrypted into a txt file and stored in a Temp folder. From there, the infostealer calls the C&C server to exfiltrate the stolen encrypted data.
Alertness important
According to Zscaler, the new malware found shows that infostealers are becoming increasingly complex. Companies are therefore urged to remain alert. They should also conduct ongoing research for new threats, inspect all traffic with malware prevention badges for known threats and use sandboxing for unknown threats.
Also read: Chrome can now take down malware masquerading as an extension