Dutch security company EclecticIQ has developed a decryptor for the Key Group ransomware. The tool has been made available free of charge.
Researchers at EclecticIQ recently succeeded in developing a decryption tool or decryptor for the Key Group ransomware from Russian hackers.
Key Group
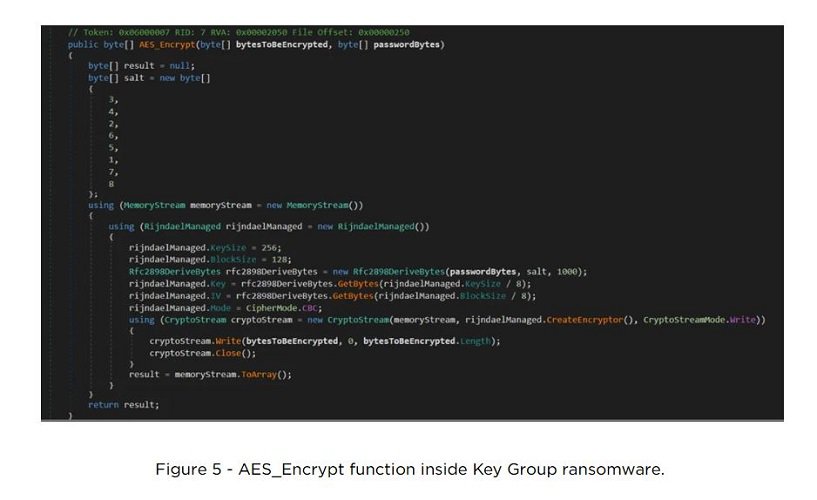
The Russian hackers from Key Group have been active since early this year, using a ransomware variant that is supposed to provide “military-grade AES encryption.” This variant is said to be based on the Chaos 4.0 builder. The Key Group’s malware is said to steal data from victims and then ask and negotiate for ransom via a Telegram channel.
The hackers would also be guilty of trading stolen data and SIM cards on Russian-speaking darknet sites, sharing doxing data and providing remote access to compromised IP cameras.
Persistent malware
The Key Group ransomware is particularly nasty because post-encryption, it deletes all original files from an affected system and adds the KEYGROUP777TG extension to all entries.
So-called Windows living-off-the-land binaries (LOLBins) are deployed to delete Volume Shadow copies, making recovery operations of the affected systems and data impossible without paying the ransom.
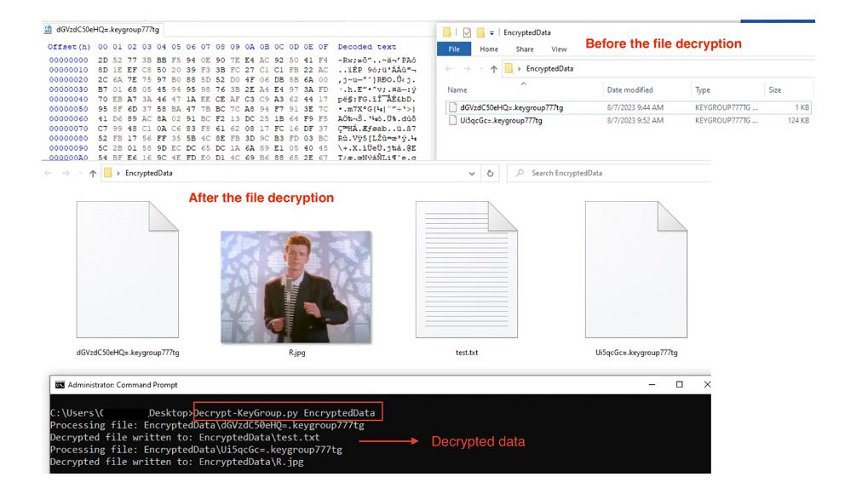
However, EclecticIQ researchers have managed, via an unnamed vulnerability in the variant, to develop a decryptor: the Key Group ransomware decryptor. This is a Python script that searches the target directory and underlying directories for files that have the .KEYGROUP777TG extension.
The files are then decrypted and the content is then stored under the original file name decrypted from the base64 string.
The researchers have now made their tool available for free. However, the tool does work for the current Key Group ransomware version. It is possible that the hackers may modify their malware in response to this decryptor.
Tip: Hackers figure out your computer’s location via malware Whiffy Recon