The so-called DarkGate malware not only attacks Skype accounts but also spreads through affected Microsoft Teams accounts.
Between July and September of this year, Skype accounts have been the target of attacks with the DarkGate malware, Trend Micro discovered. This malware enables the spread of ransomware and malicious payloads that aim to enable crypto mining.
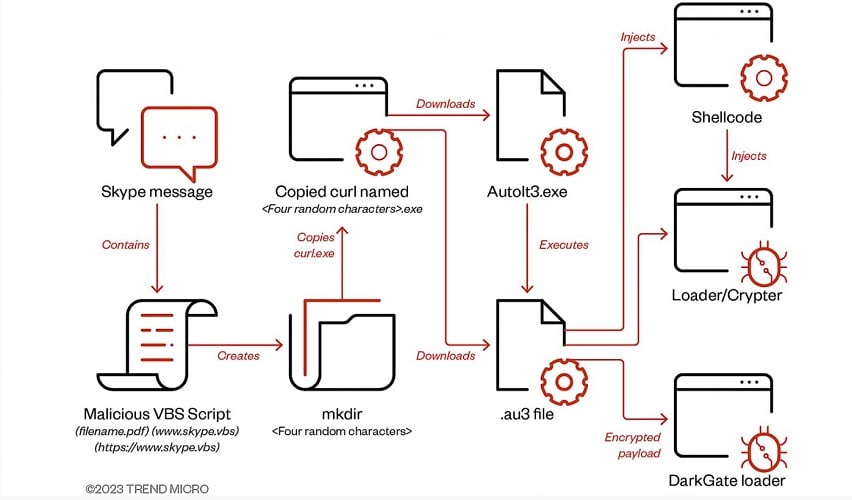
Affected Skype accounts are infected via messages that contain VBA loader script attachments. These scripts download a “second-stage” AutoIT script that eventually downloads and executes the DarkGate malware payload.
Hackers thus managed to take over the entire messaging thread of a Skype account and then create (malicious) files related to the discussion in the message thread. The Skype accounts were possibly attacked via leaked login credentials.
Microsoft Teams also vulnerable
Not only does Skype act as an access path for the hackers, which Trend Micro links to the Black Basta ransomware gang, but Microsoft Teams is also vulnerable to DarkGate malware.
Teams is especially vulnerable if the Microsoft platform allows receiving messages from remote users, Truesec and MalwareBytes also discovered. Teams accounts were attacked via compromised Office 365 accounts from outside companies and via a freely available TeamPhiser tool.
This tool allows hackers to bypass restrictions on incoming files from outside users and send phishing attachments to Teams users.
Use of the DarkGate malware is becoming increasingly popular, according to researchers, especially after Qakbot network was taken offline. Annual subscriptions to the malware-as-a-service service cost about $100,000 each on the darkweb.
Also read: Hundreds of thousands of mail servers vulnerable due to Exim bug