An undocumented feature in the Apple SoCs of iPhones has been a key component in a prominent spyware campaign. This is stated by researchers from Kaspersky in a recent publication about the series of attacks known as “Operation Triangulation.”
iPhones were susceptible to a spyware attack since 2019, in which hackers were able to bypass memory protection in now obsolete iOS versions. Specifically, this involved hardware features within iOS versions up to version 16.6. Thus, the most recent release, version 17.2.1, is not affected by the vulnerability.
Operation Triangulation attack
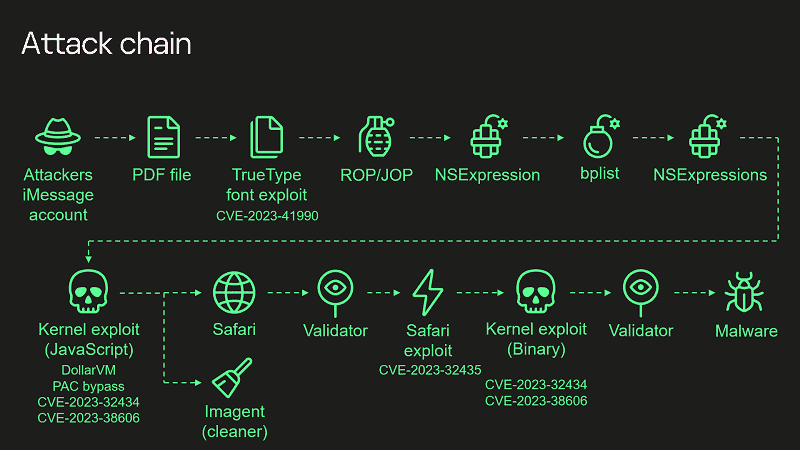
Operation Triangulation, an Advanced Persistent Threat (APT) attack campaign that targets only iOS devices, was discovered by Kaspersky last summer. This attack uses “zero-click exploits” distributed through the iMessage service. This eventually gives hackers full control of affected devices and thus access to user data.
Vulnerability in the Apple SoC
A key attack vector for this appears to be a vulnerability on the Apple SoC in iOS, which made iPhones, among others, susceptible. The vulnerable hardware feature may have been intended for testing or debugging.
After the initial zero-click iMessage attack and subsequent privilege escalation, the hackers were able to exploit this feature to bypass hardware-based security and manipulate the contents of protected memory areas.
Kaspersky researchers uncovered this key vulnerability after a thorough reverse-engineering process.
Patches implemented
Apple has since repaired the vulnerability in the SoC. This specifically involved vulnerabilities CVE-2023-32434, CVE-2023-32435, CVE-2023-38606 and CVE-2023-41990. The mitigation is for all Apple devices, meaning not only iPhones, but also iPads, iPods, macOS laptops and desktops, Apple TV and Apple Watch.