Cisco Talos recently found that Google Cloud Run has been abused on a large scale. Attackers are using this service to distribute high volumes of banking trojans, particularly to target financial institutions in Latin America.
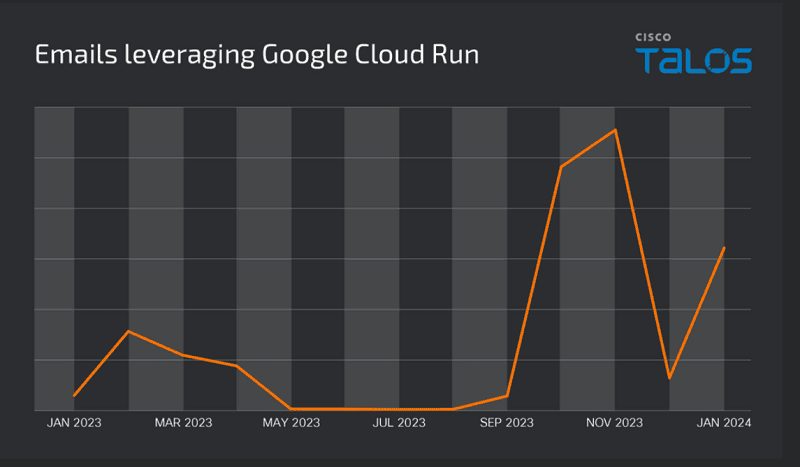
Recent research by Cisco Talos shows that cybercriminals have been abusing the Google Cloud Run service to distribute banking trojans since as early as September 2023. Google Cloud Run allows users to deploy front- and back-end services, websites or applications. The service handles these workloads without having to manage infrastructure or to account for scalability.
Cisco Talos researchers state that this cloud service is also very popular with the spreaders of the banking malware. This is mainly because of its relatively low cost and ability to bypass standard security blocks and filters.
Attack path
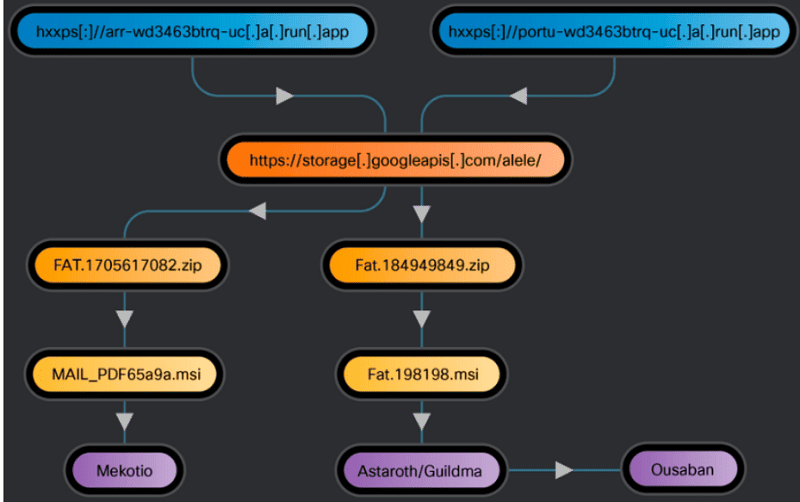
Cybercriminals use the service as a vehicle for hosting malicious websites or services. Victims are persuaded to click on links through phishing, with messages that look like legitimate communications or invoices. These lead to malicious services hosted on Google Cloud Run; there, the malicious payload is subsequently installed.
Sometimes the payload is also delivered via MSI files. This happens, for example, because Google Cloud Run gives a 302 redirect to a Google Cloud Storage location where a ZIP file containing a malicious MSI file is stored.
Mainly Latin American victims
The malware campaign mainly targets companies in Latin America, but organizations within the U.S., in European countries and in South Africa are also targeted.
Through Google Cloud Run, the cybercriminals mainly distribute three specific banking trojans; Astaroth, Mekotio and Ousaban. Astaroth, among others, is a notorious banking trojan. It can be tailored specifically to countries or companies.
In the discovered campaign, this trojan first targeted victims from Brazil, but now also targets 300 financial institutions in 15 Latin American countries. This also captured login credentials for crypto-exchange services.
Google Cloud investigates problem
Google Cloud, meanwhile, is aware of the vulnerability in Google Cloud Run. One commented to Bleeping Computer that it is investigating the breach. The malicious links are said to have since been removed by Google Cloud.
Also read: Dutch police and Cisco Talos take down Babuk Tortilla ransomware