A new StrelaStealer malware campaign has affected more than 100 companies and organizations in the U.S. and Europe. Hackers are now also using ZIP files to spread the malware payload, Palo Alto Networks Unit42 concludes.
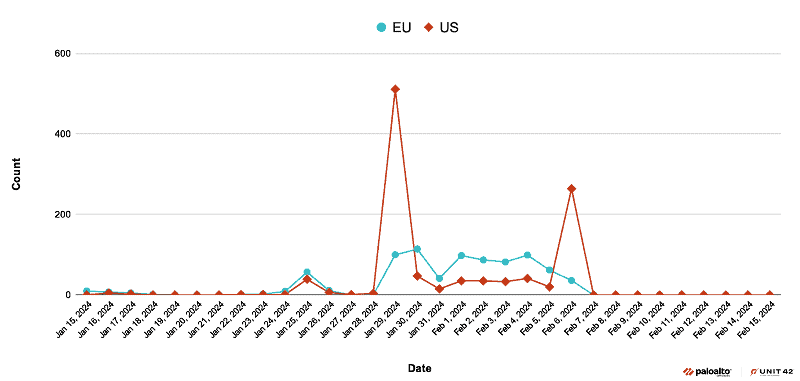
The StrelaStealer malware spread particularly quickly in November 2023, as Palo Alto’s Unit42 discovered. In recent times, the attackers primarily targeted organizations in the U.S. and Europe. There was also a significant uptick in the months of January and February this year.
The malware variant has been known since 2022 and previously targeted predominantly Spanish-speaking end users. The malware targets victims through phishing to steal login credentials for email accounts via Outlook or Thunderbird clients. The hackers then send these login credentials to a Command and Control (C2) server.
New attack path
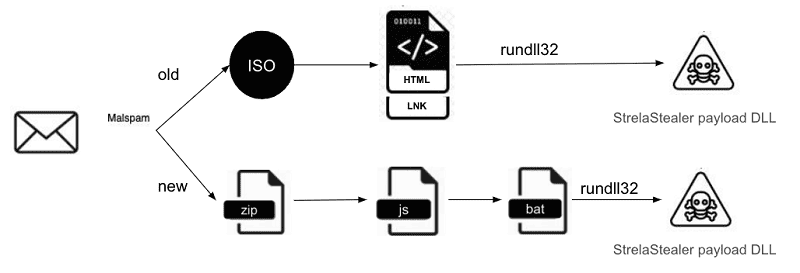
In the past, the StrelaStealer attack path involved sending emails containing manipulated .ISO files with an .Ink shortcut and an HTML file. The latter file used a polyglot to trigger a ‘rundll32.exe’ file to execute the malware payload. This polyglot file infection also made the malware difficult to detect by security software.
The StrelaStealer campaign uses .ZIP files that place JScript files on affected systems. When executed, they install a batch file and a base64 encrypted file that extracts into a DLL file. This DLL, in turn, causes rundll32.exe to install the StrelaStealer malware.
The new infection chain additionally provides control flow obfuscation to make analysis difficult. It also removes PDB strings to evade detection by security tools that operate according to static signatures.
High tech a favourite target
Most companies in the U.S. and Europe now affected by the new variant of StrelaSteaker include those in the high tech and financial sectors. Companies in the legal, manufacturing, government, energy and utility, insurance and construction sectors are also among the victims.
PaloAlto Networks Unit42 experts urge end users to exercise caution when receiving unknown emails about payments or invoices, for example. Of course, they should also not just download and open attachments from unknown senders.
Read also: Netherlands extradites suspect behind Raccoon Infostealer to the US