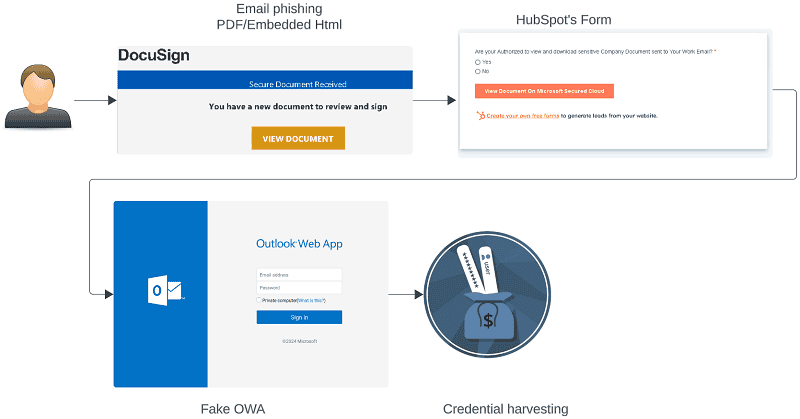
Hackers, through a phishing campaign using malicious DocuSign files, are attempting to target long-term presence mainly in Azure cloud environments of European companies. This was discovered by Unit 42 of Palo Alto Networks recently.
According to Unit 42’s security specialists, a phishing campaign affected about 20,000 employees of European automotive, chemical and industrial companies between June and September this year. Specifically, this campaign focused on stealing login credentials from corporate accounts and then hijacking the affected companies’ Microsoft Azure corporate cloud infrastructure.
In doing so, the hackers attempted to maintain a permanent presence within this infrastructure and continue to access the sensitive data contained therein. They did this by constantly logging into new devices with the stolen login credentials.
The hackers also attempted to access the cloud storage in these cloud environments and create new users. However, these actions that could have led to even more problems in the long run were prevented.
Phishing links to HubSpot Free Form Builder
The hackers’ attack path was via emails containing a malicious DocuSign PDF file or an inserted HTML link. The file, which attempts to attract victims’ attention via social engineering, and the link then referred them to a malicious Hubspot Free Form Builder.
From the latter environment, they were redirected again to the malicious pages that the hackers use to try to extract data. In this case, a Microsoft Outlook Web Access login page. Here the victims had to enter their email address and login credentials for Azure. From there, the hackers hijacked it and gained access to the cloud environment.
Attackers unknown
Who exactly is behind the attacks is unknown. However, Unit 42 specialists do indicate that they came across Ukrainian- and Russian-language websites in their investigation of the attack infrastructure, writes The Register.
When the phishing campaign was discovered, most of the infrastructure for these attacks was already offline. Two nonetheless found examples of the phishing-pace source code showed that many phishing links redirected to spoofed websites of the attacked companies. The hackers also used robust and secure anonymous hosting services for their attacks, and one hosting service was used multiple times for attacks.
Also read: LLMs of Google customers could leak through Vertex AI