Dutch security researcher Victor Gevers found an account that the Kremlin used to grant itself access to the servers of local and foreign companies operating in Russia. The account was found in thousands of MongoDB databases that appeared to be accessible online without a password.
Gevers spoke to the site ZDNet and told about the back door account he found. He argues that, if any hacker had found this account, they would have been able to access the sensitive information of thousands of companies operating in Russia. The first time I found the credentials was in the user table of a Russian Lotto site, Gevers said during the interview. I had to do some digging to understand that the Kremlin requires remote access to systems that process financial transactions.
More than 2,000 databases
The researcher states that he found the same admin@kremlin.ru-account in more than 2,000 other MongoDB databases. All of them were exposed online and belonged to local and foreign companies operating in Russia. These included databases of local banks, financial institutions, telecom companies and even Disney Russia. That looked like this:
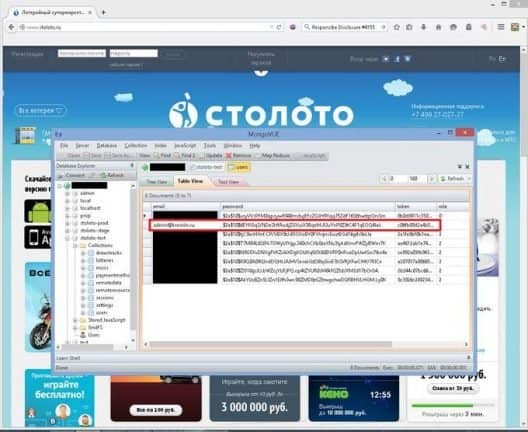
Gevers even found the account in a Mongolian DB database belonging to the Ukrainian Ministry of the Interior, which contained information about the ERDR investigations that were carried out on corrupt politicians in the country. That is remarkable, because Russia and Ukraine have been in conflict for some years.
In his investigation, Gevers did not find out what the account was used for. As a whitehat hacker, he only researched leaking MongoliaDB databases and tries to respect privacy as much as possible in his research, by minimizing the search for information such as owners’ email addresses. All systems with this password were accessible to everyone anyway. The MongoDB databases were all rolled out with default settings. So anyone without authentication had access to CRUD [Create, Read, Update, Delete].
It has taken us quite some time and effort to contact the Kremlin and warn about the problem. But we never succeeded. At the same time, the message seems to have got through. We still discover Russian databases of companies, but these credentials have not been found in recent months, says Gevers.
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.Until recently many 🇷🇺 companies were using MongoDB not securely.
Most of them are reported to the owners. The biggest issue was that @KremlinRussia_E requires remote access to businesses and used the same credentials everywhere as we found them in the thousands of open databases pic.twitter.com/U5UGMXttNK— Victor Gevers (@0xDUDE) January 27, 2019
