In 2017, the news sounded that criminals had managed to install an advanced backdoor on certain Android devices, even before they had left the factories. Now, almost two years later, this is also confirmed by Google itself.
The backdoor in question is Triada, a malware that was uncovered by Kaspersky as early as 2016. He called it one of the most advanced mobile Trojans our malware analysts have ever encountered.
Once installed on an affected phone, Triada was able to manipulate the Zygote process in Android. Zygote is a process at the heart of Android, which is used as a template for each application. Once the Trojan had entered Zygote, it literally became part of every application on the device and could manipulate it.
Triada was mainly used to install spam apps that showed ads, but in one attack that Kaspersky discovered, the Trojan was also used to spoof urls in the browser, for example. In this way, users could be directed to another web page, such as a phishing site.
Backdoor
In July 2017, Dr. Web researchers reported that they had found Triada embedded in the firmware of several Android devices. According to the security company, this involved more than 40 mainly Chinese smartphones, from brands such as Leagoo and Doogee.
The attackers used this backdoor to download and install additional malware modules in the background. Because Triada was deeply integrated in the operating system on these devices, the Trojan could not be removed in the standard way in this case.
Supply Chain
Since then, Google has also started its own research and this week it has come out with it. Google confirms the findings of Dr. Web, but does not appoint any affected brands or models. Google’s team writes that it suspects that a supplier to the manufacturers using the name Yehuo or Blazefire is hiding behind the supply chain attack.
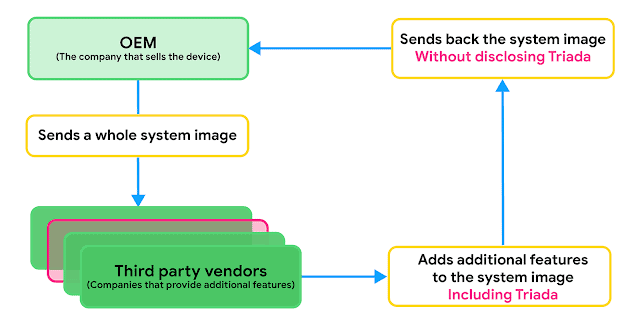
Sometimes OEMs want to include features that are not part of the Android Open Source Project, such as facial unlocking. The OEM can then choose to collaborate with a third party who can develop the desired function, and send the complete system image to that supplier, explains Lukasz Siewierski of the Android Security & Privacy Team in the report.
According to Siewierski, Triada’s developers began to focus on the supply chain after Google had taken measures to combat the Trojan in 2016. This prevented Triada from gaining root access on a device and improved Google Play Protect to be able to remotely disinfect affected phones.
Build Test Suite
Triada is a good example of how Android malware authors are becoming more and more adept, Siewierski says. By working with the OEMs and giving them instructions on how to remove the device threat, we have reduced the spread of pre-installed Triada variants and removed infections from the devices through the OTA updates.
Last year, Google also launched the new Build Test Suite program, which allows manufacturers to submit new or updated system images for a security review. This includes scanning for pre-installed PHAs, or potentially harmful applications, in the system image. In the first year, 242 images with PHAs were stopped in this way.
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.