Researchers of security specialist Aqua Security have found that hackers have been scanning Docker instances for possible unsecured API ports for several months now. When these are found, they are attacked, to then install new Kinsing crypto-mining malware.
Research by the security specialists has shown that hackers have been scanning instances of the Docker container platform in recent months that are not sufficiently secured. Above all, they are looking at API ports that are not password-protected and are thus open to everyone. In this way, hackers gain access to large computing power sources and then use them for crypto-mining.
Installing Ubuntu containers
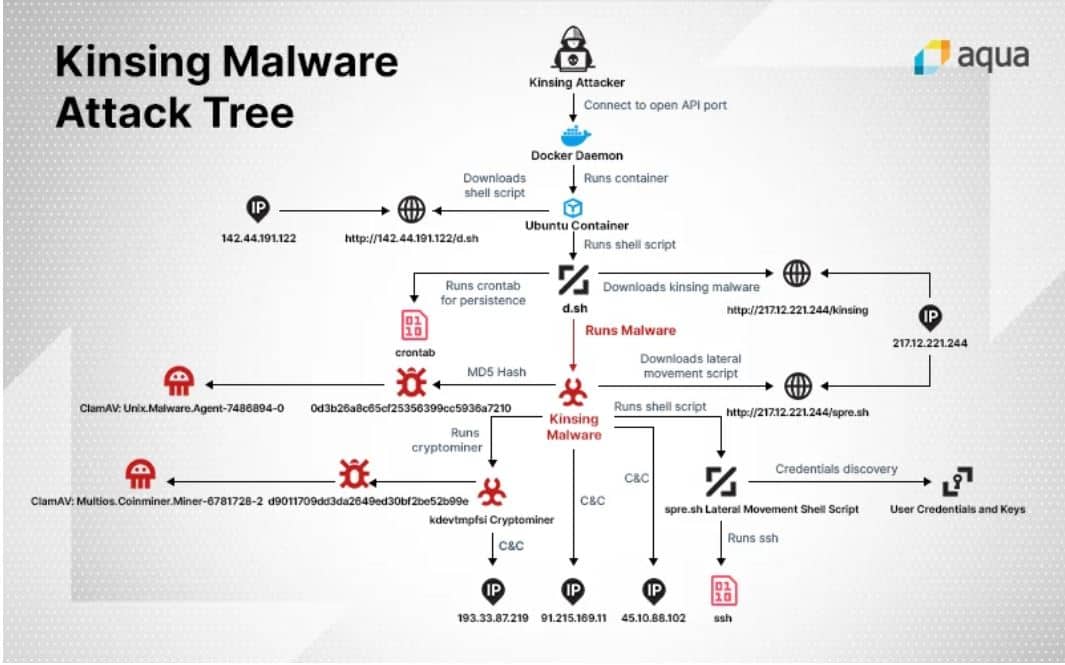
Specifically, after accessing a Docker instance through an unsecured gate, spider hackers spin up an Ubuntu container. In this container, they download and install the new Kinsing malware.
Secondary functionality
The Docker instance is then used for crypto-mining, but also has secondary functions. For example, the hacked instance with the malware removes other malware that can run locally.
It also collects local SSH passwords so that the Kinsing malware can spread within the affected company’s container network. In this way, the Kinsing malware can easily infect multiple cloud environments.
Multiple attacks
According to the security experts of Aqua Security, this attack with crypto-ming malware and botnets on Docker instances is one in a longer tradition. The first of these attacks was already observed in early 2018. Since then, six major attacks have already been identified by various security companies.
Security tips
The security specialists therefore call on companies to thoroughly check the security settings of their Docker instances and to ensure that no administrative APIs inadvertently give access to these instances via the Internet. They recommend placing these special APIs behind a firewall or only making them accessible via a VPN gateway if they need to be accessible online. Otherwise, they should simply be disabled.