Security researchers have found vulnerabilities in Linux PolicyKit (also known as Polkit). The vulnerabilities allow hackers to gain complete access to affected machines and upload malicious code. The issue has since been patched.
According to Qualys researchers, the so-called PwnKit exploit manipulates a twelve-year-old vulnerability in the Linux Polkit system tool. The tool manages privileges in Unix-based operating systems. It provides a mechanism for non-privileged processes to securely interact with privileged processes. Furthermore, the tool allows commands to be executed with high privileges.
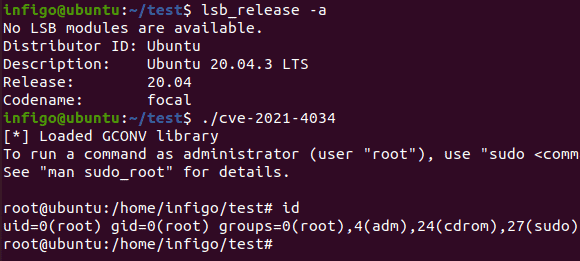
A memory corruption vulnerability has been present in the tool since 2009. It allows hackers with limited privileges to access all privileges on an affected machine, even the root. In this way, they can upload and distribute malicious payloads with the highest system privileges. The exploit was discovered in November and has now been disclosed.
Polkit daemon doesn’t have to be running for the vulnerability to be exploited. Polkit is installed by default in every major Linux distro, making the threat extremely real.
Attack scenarios
According to Qualys, the most natural attack scenario is an internal malicious employee gaining access to full root privileges. Only hackers who already have system access can access full root privileges via the vulnerability. Hackers must be authenticated to the vulnerable machine and cannot perform remote attacks without this authentication.
Specialists expect that the exploit will be abused considerably in the foreseeable future. A working method has already been tested for Linux distribution Ubuntu 20.04.
Testing
Major Linux distro suppliers have already released patches. Qualys calls upon administrators to carefully check their Linux systems for the presence of the exploit and hackers. They should pay close attention to log entries such as ‘The value for the SHELL variable was not found in the /etc/shells file’ or ‘The value for environment variable […] contains suspicious content’. Qualys adds that, in some instances, PwnKit can be executed without leaving any traces.
Users who cannot patch immediately can take a temporary measure to limit the threat. Qualys advises using the chmod 0755 /usr/bin/pkexec command to remove the SUID bit from the pkexec command. This prevents the command from running as a binary.